Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Lukitus Ransomware?
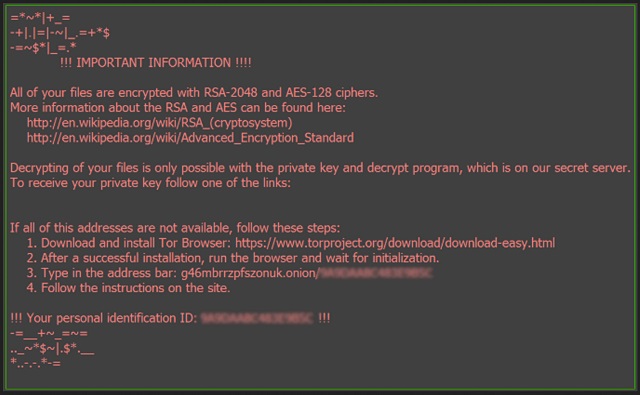
Readers recently started to report the following message being displayed when they boot their computer:
!!! IMPORTANT INFORMATION !!!!
All of your files are encrypted with RSA-2048 and AES-128 ciphers.
More information about the RSA and AES can be found here:
http://en.wildpedia.org/wiki/RSA_(cryptosystem)
http://en.wikipedia.org/wiki/Advanced_Encryption_Standard
Decrypting of your files is only possible with the private key and decrypt program, which is on our secret server.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
To receive your private key follow one of the links:
If all of this addresses are not available, follow these steps:
1. Download and install Tor Browser: https://www.torproject.org/downIoad/download-easy.html
2. After a successful installation, run the browser and wait for initialization.
3. Type in the address bar: g46mbrrzpfszonuk.onion
4. Follow the instructions on the site.
!!! Your personal identification ID: !!!
Ransomware viruses are the most dreaded type of infections. There is a reason for this. These parasites are destructive. They enter your computer unnoticed, locked your files and demand hefty sums to restore your access to them. Lukitus File Virus is the latest example of how frustrating and destructive these viruses can be. Lukitus is the newest variant of the infamous Locky Ransomware. We can say that this parasite is a classic in its field. It sneaks into your machine and remains hidden until it is already too late. Upon installation, Lukitus starts a system scan. It targets user generated files. Such as your pictures, documents, videos, databases, archives, etc. Then, it will lock these files. The ransomware uses the strong RSA-2048 and AES-128 ciphers to encrypt your files. It also adds the .lukitus extension at the end of each encrypted file. Thus, if you have a picture named example.jpeg, the virus will rename it to example.jpeg.lukitus. You will be able to see the icons of your files, but you won’t be able to open or use them. Once the encryption process is finished, the ransomware displays its ransom note. The victims should go through a few steps to discover the complete payment instructions. After installing Tor browser and visiting a specific web page, the victims will be required to transfer 0.49 BTC (about $2 050 USD) into the hackers’ Bitcoin wallet. And then, supposedly, they will be able to download a decryptor. Do not, under any circumstances, contact the crooks. These people are criminals and are likely to ignore you once the ransom is paid. Unfortunately, there are no alternative file decryptors for this ransomware. However, if you have system backups, there may not be a need for you to pay the ransom. Before you plug in any device, clean your computer. Otherwise, the ransomware will compromise your external memory, too. You can use our detailed guide, yet, Lukitus Ransomware is quite complicated. So is its removal. Hence, we recommend you to use a trustworthy anti-virus app.
How did I get infected with?
Lukitus Ransomware is distributed via massive spam email campaign. The crooks write anonymously and politely urge the victims to download the attached files. The files are usually archives which are corrupted. Once you open the files, a JS code is executed. It downloads the ransomware from a remote server. This happens in a split-second. Then, the virus gets installed and you know how it all ends. The bottom line here is that you could have prevented this infection. The hackers rely on your carelessness and negligence. Do not open suspicious emails. Check the sender’s contacts first. Simply, enter the questionable address into some search engine. If it was used for shady business, someone might have complained online. This step, unfortunately, is not flawless. New emails are created every second. So, double check the sender. If, for example, you receive a message from a company or organization, go to their official website. You can find their authorized email addresses there. Compare them with the one you have received a letter from. If they do not match, delete the imposter immediately. When you open an email, look for red flags. Generally, anything out of the ordinary should be recognized as one. If you do not expect invoices or job applications and you still receive one, it is probably a scam. Only your caution can keep your computer safe.
Why is Lukitus dangerous?
Ransomware viruses are feared for a reason. They are deadly. Lukitus is not an exception. It has sneaked into your computer and locked your files. You can see the pictures of your documents and pictures, but you cannot open or use them. If you create new files, the ransomware will encrypt them, too. Your computer becomes useless. To restore your files, the Lukitus Ransomware demands Bitcoins. This currency is untraceable. Do not trust the word of cyber criminals. The hackers tend to ignore their victims once the ransomware is paid. And since the payment method is untraceable, no one, not even the authorities, can help you. Therefore, we strongly recommend against paying the ransom. One more thing to mention here. The Lukitus Ransomware is a complicated locker. There are no guarantees that the hackers themselves can undo its encryption. There are hundreds of cases where the victims received only partially working tools or nothing at all. Do not expect the hackers to keep their part of the deal. Besides, the file decryption process does not remove the virus itself. If you skip the removal, the ransomware will re-encrypt your newly restored files. How many times are you willing to pay for your files? Do not pay the ransom. Never forget that you are dealing with criminals. They will double-cross you. Keep in mind that by using your infected machine to pay the ransom, you are giving the ransomware a chance to record your credit card details and other sensitive information. Lukitus is a sophisticated ransomware. Never underestimate it. Consider discarding your data. Clean your machine and only then, try to restore some of your files from backup files. Unfortunately, the threat of ransomware viruses is quite serious. Adopt habits that will prevent future troubles. Start backing up your important data on external devices (USB sticks, SD cards, external hard drives, clouds, etc.) It is also a good idea to invest in a professional anti-virus program.
Lukitus Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Lukitus Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Lukitus encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Lukitus encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



