Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove 726 Ransomware?
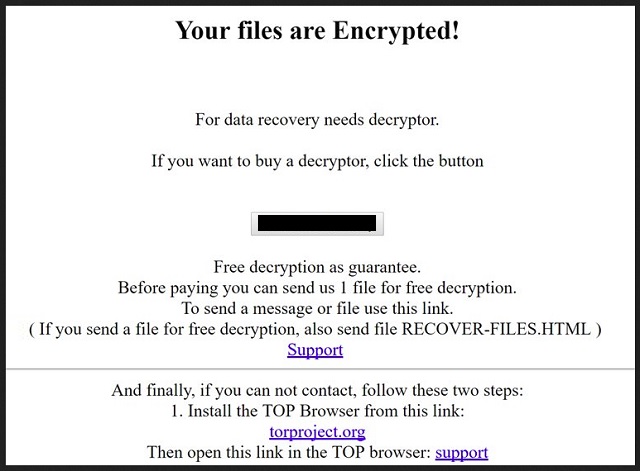
Readers recently started to report the following message being displayed when they boot their computer:
Your files are Encrypted!
For data recovery needs decryptor.
If you want to buy a decryptor, click the button
Yes, I want to buy
Free decryption as guarantee.
Before paying you can send us 1 file for free decryption.
To send a message or file use this link.
( If you send a file for free decryption, also send file RECOVER-FILES.HTML )
And finally, if you can not contact, follow these two steps:
1. Install the TOR Browser from this link:
Then open this link in the TOR browser:
726 is the name of a recently-discovered file-encrypting infection. It’s a new ransomware that derives from an old foe. 726 is an updated variant if the GlobeImposter threat. And, a continuation of sorts to the 725 plague. The ransomware exhibits the same characteristics, you’ve come to expect. It invades your system via deceit. Once inside, takes over and corrupts everything. You find every file, you keep on your computer, locked. There’s an appended 726 extension to each one. And, it renders them unusable. Even though, they’re where you left them, they’re beyond your reach. Pictures, documents, music, all of it. It’s encrypted, and renaming or moving files doesn’t free them of the 726 hold. The only way out, the ransomware provides, is compliance. It leaves a ransom note fort you to find. It’s on your Desktop, as well as in each affected folder. It’s called “RECOVER-FILES-726.html” and it has instructions. Ones, the cyber threat expects you to follow. It states you must pay 0.18 BitCoin as ransom. Once you complete the transfer, there will be an exchange. The infection sends you a special decryption key. Apply it, and free your files of encryption. And, here’s the ringer. You remove the encryption, not the infection. The ransomware remains, ready to strike again at any moment, it so chooses. Not to mention, the more severe problem. You open the door to your privacy. These cyber extortionists can then enter. Compliance leads to nothing positive. It only gives you a false sense of control. Payment means you’ll lose money, and your private life. And, still, odds are, you will NOT regain your files. So, don’t comply. Discard your data from the beginning. The game, 726 threat lays out, is not one, you should play. The risks are too great. And, there are no rewards.
How did I get infected with?
The 726 menace tends to slither in via the usual antics. The ransomware turns to the old but gold means of infiltration. They assist it in its attempts for a sneaky invasion. But, do you know what? No matter which method, the tool uses, it needs a key ingredient. Its success rests on you. Or, rather, your carelessness. For the ransomware to slither in undetected, you have to be careless enough to allow it. Each means, it turns to, requires the user’s distraction. You have to click a link, download an attachment, install a tool or fake update. And, NOT be vigilant enough to notice the ransomware. Take the spam email attachments, for example. You can receive a message from a seeming reputable company, like PayPal or DHL. It reads you have to download and open the attachment, which is an invoice, receipt, et cetera. You have to be attentive enough to spot the deceit, and call foul. Take the time to do your due diligence. Don’t follow instructions blindly. That applies for installing freeware, trusting seeming updates, anything. Any time, you allow something into your computer off the web, take it with a grain of salt. Suspicion leads to due diligence. And, that helps to keep infections away.
Why is 726 dangerous?
Here’s why you mustn’t play by the rules, laid out by 726. Or, any ransomware, for that matter. They set up a game, you’re rigged to lose. Understand that now, and accept it as fact. You cannot win against such a threat. There’s aren’t enough ways to stress that you lose no matter what you do. It’s a question of prioritizing your losses. Choose what you’re willing to go without. It’s either your files. Or, your files, money, and privacy. And, when put like that, it’s an easy choice, wouldn’t you agree? If you decide to participate, and pay the ransom, you’ll regret it. First off, it guarantees you nothing. The cyber kidnappers can send you the wrong key. Or, not send one at all. And, second, as mentioned, the key removes the encryption. So, you’re still stuck with a ransomware. Only now, you lost money. And, gave the extortionists a way to your privacy. Don’t allow these people to get a hold of your personal and financial details! Isn’t it enough that they got your files? Don’t let them have that, too. Don’t pay. Say goodbye to your data. It’s a tough call to make, but it’s the better alternative.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
726 Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover 726 Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with 726 encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate 726 encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



