Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Freefoam Ransomware?
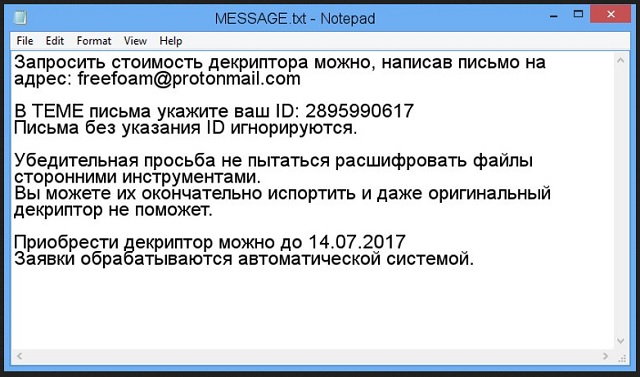
Readers recently started to report the following message being displayed when they boot their computer:
You can ask for the cost of the decryption by writing a letter to the address: freefoam@protonmail.com
In the subject of the letter, write your ID: [RANDOM DIGITS]
Letters without an ID are ignored.
Please do not try to decrypt files with third-party tools.
You can ruin them completely and even the original decryptor will not help.
You can buy the decrypt by [DATE]
Submissions are processed by an automated system.
Freefoam is the name of a newly-discovered ransomware threat. These infections are among the worst types of cyber intruders. If not, THE worst. They make their attack quite personal, as they keep your data hostage in exchange for a ransom. Their scheme is quite simple. Invade, corrupt, extort. Freefoam resorts to trickery to infiltrate your system. Once inside, it takes over. The tool grabs hold of every single file, you keep on your computer. Music, photos, videos, documents. It all falls under the clutches of the cyber threat. Freefoam solidifies its keep over your data, by attaching a special extension. At the end of each file, you find an added “freefoam.” If you had a photo, called ‘me.jpg’ it becomes ‘me.jpg.freefoam.’ Once the extension is in place, your files are beyond your reach. They become inaccessible. You can try to move or rename them, but it’s pointless. You cannot open a single one. The ransomware backs you into a corner with a seeming single choice. Compliance. Well, here’s a better alternative. Do NOT comply but forsake your files. Yes, it’s not a pleasant alternative. But it’s the one that doesn’t cost you your privacy. To follow the infections demands is to expose yourself. If you pay, you grant access to your personal and financial details to cyber criminals. And, that is NOT something, you want to do. You will NOT enjoy the repercussions. Do yourself a favor. Make the tougher but wiser choice. Say goodbye to your data in the name of your privacy.
How did I get infected with?
There are plenty of ways you can catch the Freefoam cyber plague. But, more often than not, you invite it into your system, yourself. Yes, you may not recall the process. But, it’s more than likely, it took place. The infection resorts to the old but gold methods of infiltration. And, dupes you into permitting its install. All, while keeping you clueless to the entire exchange. Yes, the tool asks if you agree to install it, but still keeps you oblivious. It may seem confusing, but it’s rather simple. Freefoam doesn’t outright seek your access. If it did, you’d deny it. So, instead, it hides behind freeware, corrupted links, spam email attachments. There are plenty of way it can deceive you, while concealing its presence. It’s up to you to be thorough enough to discover it. Don’t give into naivety and distraction. Don’t rush. Do NOT skip reading the terms and conditions. They’re crucial if you want to keep your PC infection-free. Always do your due diligence when installing updates, tools, anything off the web. Even a little extra attention helps you prevent threats from sneaking in undetected. Threats like Freefoam. Always apply caution when allowing something into your system. It goes a long way.
Why is Freefoam dangerous?
Freefoam seems to target Russian-speaking users. That’s because the ransom note, it leaves after encryption, is in Russian. The infection uses RSA encryption algorithm to put your files under lock down. Once it’s done with locking each one you have on your computer. It keeps them hostage until you make payment. And, the tool even provides you with incentive act fast, and don’t delay. It provides you with a dead line. Once your given time runs out, the decryption key you need gets deleted. Then, you lose your files for sure. But, here’s the thing. You lose them either way. Let’s explain. What guarantees do you imagine you have? Do you think after payment, you regain control of your data? You have ZERO guarantees that compliance leads to anything positive. There are several scenarios that can unfold after payment. And, they all end badly for you. Say, you transfer the sum, the cyber kidnappers requested. Then, what? You wait to receive the promised decryption key, right? Well, what if you don’t get it? What if they send you none? Or, if they give you one that doesn’t work? And, even if it does work, and all seems fine and dandy, it’s not. The decryption key, you pay to buy, only removes the encryption. The infection itself remains. The Freefoam program still lurks on your computer, ready to strike again. Do you see now, why it’s best to discard your data? No matter what course of action you take, you lose. So, cut your losses. Lose your files, so you don’t also lose money and your privacy. It’s the less pleasant, but better alternative.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Freefoam Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Freefoam Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Freefoam encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Freefoam encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



