Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Wowsmith123456@posteo.net Ransomware?
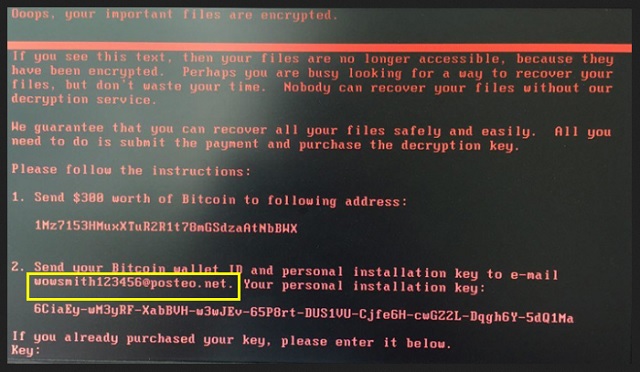
The Wowsmith123456@posteo.net Ransomware is the newest update of the infamous Petya Ransomware. And this one is a classic in its field. It is extremely dangerous, sneaky and destructive. The wowsmith123456@posteo.net Ransomware is a well-known infection. Its developers are still working on it for a reason. This ransomware spreads like wildfire. It has infected hundreds of computers worldwide. If you are attacked by this virus, you are in a serious trouble. The ransomware employs stealthy techniques to enter its victims’ computers unnoticed. Once on board, the virus scans your HDD and encrypts all target files. Then it will delete all shadow copies of your files and system backups. All this happens in the background. You cannot notice the virus, not until it is too late. Only after the encryption process is complete, will the wowsmith123456@posteo.net Ransomware display its ransom note. The virus locks your screen. It demands a $300 USD as a ransom. You are supposed to pay in Bitcoin and then contact the hackers. Restrain yourself from doing so. Contacting criminals is never a good idea. These people have invaded your computer. They will not hesitate to use your email address to further harass you. Consider discarding your data. Even if it is worth the money, don’t do it. You can never win against criminals. Understand the situation. It is a lose-lose one. By paying, you are exposing your private and financial information at risk. Files are replaceable, privacy is not. The virus is on your computer. A file-recovery won’t remove the threat. You must clean your computer. You can do it either manually or automatically. Keep in mind, however, that this virus is quite complicated, so is its removal. We recommend you to use a trustworthy anti-virus program.
How did I get infected with?
To reach its victims, the wowsmith123456@posteo.net Ransomware uses the oldest known virus distribution technique. The good old spam emails are the reason why you are suffering. The payload file of the ransomware is usually attached as a file. However, the body of the emails provides a link which will also download the virus. As you can see, a bit more caution could have prevented the infection. The Internet is not a safe place. It is bursting with parasites which wait for you to make a mistake. Learn your lessons. When you receive a message from an unknown sender, do your research. Enter the questionable address into some search engine. If it was used for shady business, someone might have complained. Crooks tend to write on behalf of well-known organizations and companies. If you receive such a letter, go to the organization’s official website. You can find their authorized email addresses there. Compare them with the one you have received a message from. If they don’t match, delete the spam email immediately. Only your caution can spare you troubles. Always do your due diligence. This is your computer, after all. You are the one who is responsible for its security.

Why is Wowsmith123456@posteo.net dangerous?
The wowsmith123456@posteo.net Ransomware plays psychological games with you. The virus displays its ransom note out of the blue. It also uses a red font and blocks your access to your system. Seeing these changes, many people will panic. That is what the crooks planned. They want you to act impulsively. Don’t do it. Take your time to consider the situation. Meanwhile, do not contact the crooks. The virus demands money for your own files. It has deleted all system backups and shadow copies. Nothing on your HDD can be accessed. However, there may not be a need to. If you have backups saved on external devices, you can use them to restore your precious files. We strongly recommend against contacting the hackers. They promise a lot. Yet, they are not trustworthy. Once the ransom is paid, hackers tend to ignore the users. Even if they contact you back, there is still no guarantee that their decrypting key will work. These people are criminals. They may use your email address to blackmail you. On top of that, the file-decrypting process is not removing the infection itself. You will restore your files just to have them re-encrypted. How many times are you willing to pay for your documents? Your best course of action is the removal of the virus.
Wowsmith123456@posteo.net Removal Instructions
STEP 1: Kill the Malicious Process
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 3: Locate Startup Location
STEP 4: Recover Wowsmith123456@posteo.net Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Wowsmith123456@posteo.net encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Wowsmith123456@posteo.net encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.