Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Onion.to Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
Hello,
We can decrypt your data, here is price:
– 7 Bitcoins in 20 hours without any stupid questions and test decryption.
– 12 Bitcoins if you need more than 20 hours to pay us, but less than 48 hours.
– 14 Bitcoins if you need more than 48 hours to pay us.
Pay us and send payment’s screenshot in attachment.
In this way after you pay we will send you decryptor tool with instructions.
TIME = MONEY.
If you don’t believe in our service and you want to see a proof, you can ask about test decryption.
Test decryption costs extra 1.5 Bitcoin to final price.
About test decryption:
You have to send us 1 crypted file.
Use sendspace.com and Win-Rar to send file for test decryptions.
File have to be less than 5 MB.
We will decrypt and send you your decrypted files back.
Also, if you don’t wanna pay you can try to bruteforce cryptokey, but it will take about 1500+ days if you have powerful enough machine.
Answer us with your decision.
Time limit starts from this email.
Here is our bitcoin wallet:
{WALLET ID}
We can recommend easy bitcoin exchange service – localbitcons.com
or you can google any service you want.
Source: Affected users.
Despite its funny and somewhat cute name, Onion.to is a deadly ransomware infection. This pest sneaked into your computer and wrecked havoc. Unfortunately, ransomware infections are one of the most aggressive viruses out there. And the Onion.to is not an exception. This menace has locked your files in complete silence. The ransomware is working behind your back. You probably haven’t noticed anything out of the ordinary, have you? Your device was a bit more sluggish, but that’s all, right? Well, this was the plan. Onion.to has entered your PC and scanned your HDD for target files. Then, it encrypted them with a complicated algorithm. Once those three operations were complete, the ransomware informed you of its presence. An obnoxious ransom note, demanding a lot of money appeared, isn’t it? That is to be expected. This virus is a classic member of its family. It seems that hackers are focus only on those win-lockers. However, the users are not informed well enough. The ransomware can “lock” all your personal files. Your documents, pictures, archives, presentations, etc. are still there. Yet, you cannot open or use them. The only way to remove the lock is to pay the demanded ransom. That is what the crooks want you to believe. We recommend keeping a backup on an external hard drive. This way you can restore your files without paying the ransom. If you have such backups, don’t use them before you remove the virus. Otherwise, you risk infecting your backup storage too. In fact, whatever you do, remove the infection first. There are cases when the victims paid the ransom, restored their files and just hours later, the ransomware re-encrypted them again. Consider the situation before you take action. You are dealing with cyber criminals. These people are not playing fair. They will do anything. Don’t trust them! Don’t contact them! And most importantly, don’t sponsor them! Every cent you send to them will be used for virus development. It is up to us to put an end to this blackmail. It is better to say goodbye to your files than to contact hackers.
How did I get infected with?
There are many ways for a ransomware to travel the web. However, the good old spam emails are probably the most commonly used method. You must have heard it a thousand times, but let’s repeat it one more time: don’t open emails from strangers. This is not an old wives’ tale. Hackers attach dangerous viruses to email letters. Nowadays, it is very hard to spot a spam message. Scammers are imaginative. They write on behalf of well-known organizations and companies. They would present their malicious files as something that is hard to be resisted. Invoices, job applications, letters of recommendation, it can be anything. Be vigilant! Check the sender’s contacts before you download anything. You can do so by entering the email address you have received a message from into some search engine. If it was used for shady business, someone must have complained about it online. Yet, this method is not flawless. Your computer’s security is your responsibility. Double-check everything. If you receive a letter from an organization, go to their official website. There, you will be able to find their authorized email addresses. Compare them with the one you have received a message from. If they don’t match, delete the spam email immediately. Other ransomware distribution techniques are: torrents, fake software updates, and corrupted links. Ransomware parasites are sneaky. Trust your instincts. If you think that something looks suspicious, there probably is a good reason for that.
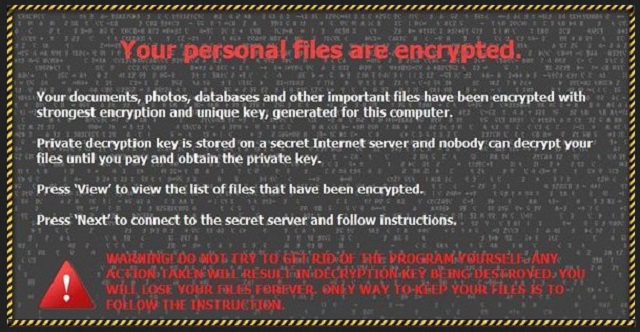
Why is Onion.to dangerous?
To decrypt your files, the crooks want Bitcoins. This currency cannot be tracked. Once you pay, you will never be able to get your money back. And no one can guarantee you that the hackers will send you working decryption tools. If they send you anything at all. Those people locked your files and now want money to restore them. Do they seem like fair people? They will not hesitate to double-cross you. Don’t negotiate with them. You can never win a game against criminals. You will only lose your time and money. Onion.to is still being developed. Hackers are making it stronger and stronger. However, security experts are working on decryption tools, too. Have some faith. Try to restore your files without paying the ransom.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Onion.to Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Onion.to Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Onion.to encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Onion.to encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



