Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Zinocrypt Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
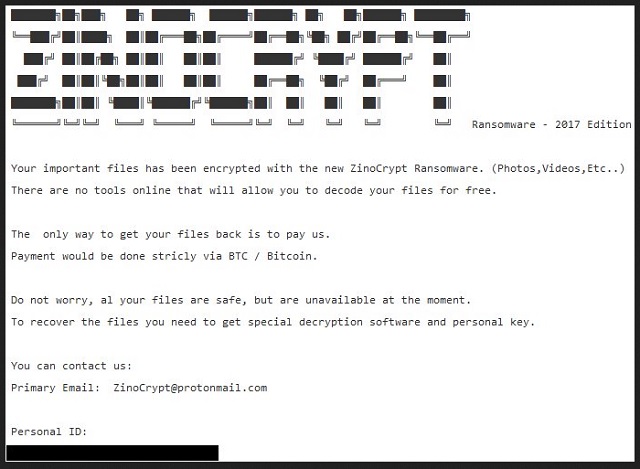
ZENOCRYPT Ransomware – 2017 Edition
Your important files has been encrypted with the new ZinoCrypt Ransomware. (Photos,Videos,Etc..)
There are no tools online that will allow you to decode your files for free.
The only way to get your files back is to pay us.
Payment would be done strictly via BTC / Bitcoin.
Do not worry, al your files are safe, but are unavailable at the moment.
To recover the files you need to get special decryption software and personal key.
You can contact us:
Primary Email: ZinoCrypt@protonmail.com
Personal ID:
[Redacted]
You probably didn’t think you’d lose all your data today. But if you came across the Zinocrypt tool, that’s what happened. Zinocrypt is a dangerous cryptovirus that locks your files after infiltration. Once the application slithers its way in, it doesn’t take long before it activates. And, after its programming kicks in, it encrypts everything. All you have on your PC falls victim to the tool. You no longer have access to your photos, videos, documents, anything. The only way to change that is to submit. It’s to follow their ransom demands. The infection claims that, once you pay up, all will be well. Upon your transfer of the ransom, you’ll get a decryption key. Then, when you apply it, your data gets released. But that sounds a bit too good to be true, wouldn’t you say? And, that’s because it is. It’s all lies. Payment doesn’t make your problems go away. On the contrary! It increases them. It’s one thing to be naive enough to rely on extortionists to keep their word. But consider the following. By transferring the ransom amount, you allow said extortionists into your private life. You give them access to your personal and financial information. And, once they get a hold of it, they can use it as they wish. Is that something, you want? Think about the consequences that entails. Don’t risk exposing your private life for the prospect of regaining your files. That’s right. A prospect. Compliance does NOT guarantee you’ll manage to decrypt your data. It guarantees nothing but your privacy getting stolen and exposed. Is that something, you’d like? Or, would you rather keep your private life private? Pick the latter, and don’t pay. It may seem harsh but it’s the better alternative. Make the wise choice, and pick the lesser evil. Say goodbye to your files, and maintain your privacy.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How did I get infected with?
Zinocrypt may claim to be a newly-created infection, but it uses the same old invasive techniques. It turns to the usual antics to slither its way in. Bogus updates, corrupted links, spam email attachments. It may even gain entry via social media websites and services for file-sharing. But the most common means of infiltration is still freeware. It continues to be the top invasive method as it provides the easiest way into your system. That’s because, most users don’t bother to exercise caution during its install. They don’t even read the terms and conditions. For reasons unknown, they say YES to everything, and hope for the best. Well, that’s a losing strategy if ever there was one. Don’t rely on luck! Apply caution! Understand that carelessness leads to the installment of cyber threats. Distraction, naivety, and haste are not your friends. They invite infections. Attention, on the other hand, helps you keep them away from your PC. Vigilance goes a long way. Always opt to do your due diligence. It can save you an abundance of grievances.
Why is Zinocrypt dangerous?
All evidence points to the ransomware as being a ‘new’ one. It’s stated so in the ransom note, it leaves you. Zinocrypt states its 2017 edition is getting distributed right now, and plagues users. Experts have accepted that the March-surfaced tool has indeed been created this year. So far, there’s no evident to suggest otherwise. Zinocrypt doesn’t take long before it locks your files. Music, videos, documents, pictures, archives, text files. All falls under its hold. The tool attaches a special extension at the end of each file. Say, you have a text file called ‘sunday.txt.‘ After the ransomware gets done with it, it becomes ‘sunday,txt.zino.’ That extension renders it useless. After it’s in place, you cannot access any of your files. Renaming or moving them changes nothing. The only way to free them of Zinocrypt’s clutches is payment. The tool makes sure to state that in its ransom note. It’s a text file, called ZINO_NOTE.txt. You can find it on your Desktop. As well as in each affected folder, harboring encrypted data. Its contents are rather standard. Pay a ransom in Bitcoin to receive a decryption key, which unlocks your files. Or, lose them. As was already explained, it’s not that simple. Say, you choose to risk it, and pay the requested amount. What then? What if the tool fails to send you the promised decryption key? Or, sends the wrong one? And, even if everything falls into place, and your data gets unlocked, what’s next? The key only removes the encryption. Not the ransomware. Zinocrypt remains on your PC, ready to strike again. What if it locks your files again an hour after decryption? You’re back to square one, but with less money, and an exposed private life. Don’t take such risks. Don’t gamble. Discard your data for the sake of your privacy. It’s the better choice.
Zinocrypt Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Zinocrypt Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Zinocrypt encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Zinocrypt encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



