Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Czech Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
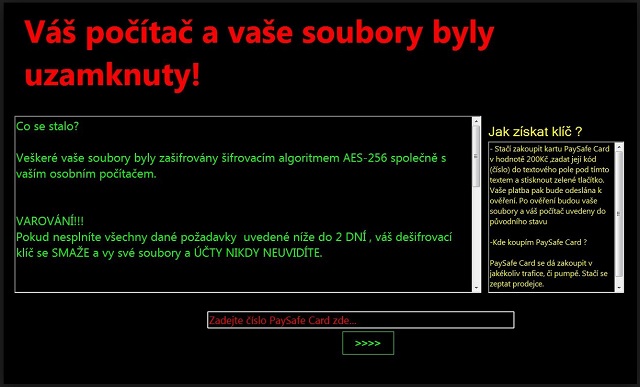
Váš počítač a vaše soubory byly uzamknuty!
Co se stalo?
Veškeré vaše soubory byly zašifrovány šifrovacím algoritmem AES-256 společně s vaším osobním počítačem.
VAROVÁNÍ!!!
Pokud nesplníte všechny dané požadavky uvedené níže do 2 DNÍ, váš dešifrovací klíč se SMAŽE a vy své soubory a ÚČTY NIKDY NEUVIDÍTE.
Jak získat klíč?
– Stačí zakoupit kartu PaySafe Card v hodnotě 200Kč ,zadat její kód (číslo) do textového pole pod tímto textem a stisknout zelené tlačítko.
Vaše platba pak bude odeslána k ověření. Po ověření budou vaše soubory a váš počítač uvedeny do původního stavu.
– Kde koupím PaySafe Card?
PaySafe Card se dá zakoupit v jakékoliv trafice, či pumpě. Stačí se zeptat prodejce.
Czech is the name of a program from the ransomware family. It’s an encrypting tool that’s plaguing web users. It’s debatable whether it’s a new or an older one, but one thing’s for sure. New or old, it’s a dangerous cyber plague. There’s no debate on that matter. Czech is a hazardous infection, which you mustn’t underestimate. It invades your system, and once in, puts you through utter hell. The ransomware locks each file you keep on your computer. And, we do mean every single one. Its clutches spread throughout, and there’s no escape. Once it locks your data, it demands payment for its release. Whatever you do, do NOT pay! It’s a scam! A lie! It’s an extortion ploy with a much bigger end game. The infection doesn’t just want to get money out of you. The end game is to get a hold of your private information. And, to comply with its requirements, is a mistake! If you pay the ransom, you grant access to your private life to the people behind Czech. To extortionists with agendas. Don’t let that scenario unfold! Protect your privacy. T’s much more important than some pictures or videos. It may seem harsh but forsake your files. Don’t pay. In the grand scheme, they’re not worth the risk.
How did I get infected with?
The Czech tool is utterly unimpressive when it comes to its invasive methods. The infection turns to the usual antics to invade your PC. That includes the old but gold methods of infiltration. In other words, it hides behind spam email attachments or freeware. It can also sneak in via corrupted links or sites. And pose as a fake update, as well. For example, you may believe you’re updating your Java, but you’re not. In actuality, you’re installing a dangerous ransomware, and don’t even know it. Why? Well, because you’re not paying enough attention. Most users throw caution to the wind when installing a tool, or an update. That’s a horrible strategy with expected results – infections. They prey on carelessness. That’s why you shouldn’t grant it! Instead, go the opposite route! Be extra thorough. Take the time to read the terms and conditions. Don’t just agree to everything and hope for the best. Due diligence can save you a ton of troubles. Choose caution.
Why is Czech dangerous?
Once Czech dupes you into installing it, you’re in trouble. The tool doesn’t waste time but gets to work. It targets everything you have on your computer. Your documents, music, pictures, videos, etc. It all falls under the nasty program’s keep. It uses the AES-256 encryption to render your files inaccessible. The application appends a special extension at the end of each of your files. Thus, solidifying its hold over it. Once the extension is in place, that’s it. Your data is locked, and beyond your reach. The only way to regain control of your files is with payment. Czech leaves you a ransom note after the completion of the encryption. It lists its demands, and leaves instructions. Instructions, you must follow if you wish to unlock your data. As was mentioned, compliance is NOT advised! On the contrary, the best thing you can do, is say goodbye to your data. Don’t pay the 200 Czech Krona, which the ransomware wants. It may be just 9 US Dollars, but even if it were just $1 it still wouldn’t be worth payment. That’s because if you transfer the sum through PaySafe card, like how it states, that’s it. You open the door to your privacy to the cyber criminals behind Czech. Think about it. To complete the payment, you leave personal and financial details. Details, which these extortionists can then use for their agendas. And, in case you were wondering, that’s bad! There isn’t a single scenario where that exposure ends well for you. Not to mention, even if you comply to your fullest, you still have NO guarantees. The ransomware can double-cross you at any given moment. After all, these are malicious cyber extortionists. What do you expect? For them to keep their end of the bargain? Don’t be naive. Choose the more unpleasant but wiser choice. Forsake your files to protect your privacy.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Czech Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Czech Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Czech encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Czech encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



