Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove RotorCrypt Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
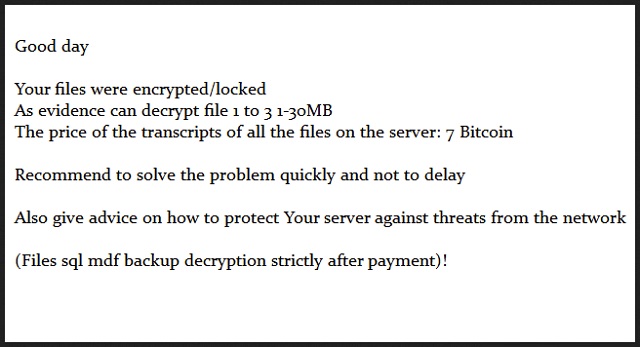
Good day
Your files were encrypted/locked
As evidence can decrypt file 1 to 3 1-30MB
The price of the transcripts of all the files on the server: 7 Bitcoin
Recommend to solve the problem quickly and not to delay
Also give advice on how to protect Your server against threats from the network
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
(Files sql mdf backup decryption strictly after payment)!
RotorCrypt is a file-encrypting parasite which mainly targets Russian PC users. It’s among the newest members of the nasty ransomware family. And yes, it’s dangerous. There are plenty of reasons why ransomware is considered to be the worst type of infection. You’re yet to discover all malicious tricks and shenanigans this virus has in store for you. However, one thing is for sure. RotorCrypt will cause you trouble. Researchers believe there’s a connection between RotorCrypt and the Rotor Virus. Both parasites lock files using the same algorithm. Their names are also suspiciously similar. Whatever the origin of RotorCrypt is, though, this program is a complete and utter pest. It goes after all your files. Favorite pictures, funny videos, favorite music files. MS office files, important work-related documents and presentations, etc. Ransomware doesn’t discriminate. This pest attacks all the personal information you’ve stored on your machine. Do you see the problem already? Your own files and your own computer. RotorCrypt strikes your memories. As you could imagine, that’s part of the parasite’s clever scheme. The pesky RotorCrypt Ransomware firstly performs a thorough scan on your PC. Once it locates your data, encryption begins. By using the strong RSA cipher, this infection locks all your files. It creates a bizarre file extension named .c400. That’s how you can tell that your data has been encrypted. RotorCrypt also renames the target files. It adds one of two email addresses – likbez77777@gmail.com or ELIZABETH7@PROTONMAIL.COM to their new names. Ransomware messes with the original format of your data. After its manipulations are complete, your computer won’t be able to read your files. Simple as that. RotorCrypt holds your precious information hostage thus causing inevitable harm. You’re now unable to use your data. And that’s not all. The virus creates removal instructions in every single folder that contains encrypted data. Those are many, many folders. According to the ransom notes, freeing your files would cost you money. Quite a lot of money. RotorCrypt demands 7 Bitcoins which equals almost 5000 USD. In exchange for your money, you’re supposed to receive a unique decryptor. As you can see, though, you won’t receive anything. Crooks are only interested in stealing your money. That means you shouldn’t even consider paying the ransom. You don’t have to sponsor greedy cyber criminals.
How did I get infected with?
The most popular technique ransomware applies are spam emails. Crooks often send infections directly to your inbox. That is because many people open every single email they receive. As a result, they compromise their own machines. RotorCrypt was probably attached to some corrupted email or message. Stay away from anything unreliable you may come across in your inbox. There might be a vicious intruder waiting for your click. To prevent getting infected, you have to delete such emails on the spot. If you make the mistake of opening them, a GWWABPFL.EXE file will get created. This is the start of your cyber trouble. Avoid random email-attachments because they are usually dangerous. In addition, stay away from illegitimate websites/torrents/bundles. Make sure you’re perfectly aware what you download. Keep in mind that ransomware also travels the Web via exploit kits. Your software should always be up-to-date. Last but not least, RotorCrypt might have landed on board with the help of a Trojan. Definitely check out the PC for more parasites. The ransomware might be having company.
Why is RotorCrypt dangerous?
RotorCrypt Ransomware locks your data. It turns all your files into unreadable, inaccessible, useless gibberish. Therefore, seeing the .c400 appendix is certainly bad news for your data. The parasite encrypts them for one very simple and prosaic reason. Ransomware is nothing but a fraud aiming at your bank account. Hackers try to trick you into contacting them. That is why they provide you two email addresses. Stay away from both of them. In the worst case scenario, your files will remain locked and your money will be gone. Are you willing to lose 5000 dollars? If not, ignore the parasite’s deceptive ransom notes. Paying the sum is not an option. Furthermore, you should never support crooks’ malicious, illegitimate business. Hackers will use every cent they gain to develop more malware. You could restore your data without giving them anything. For starters, get rid of the parasite. To do so manually, please follow our manual removal guide down below.
RotorCrypt Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover RotorCrypt Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with RotorCrypt encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate RotorCrypt encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



