Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Bitcoinrush@aol.com Ransomware?
Reader recently start to report the following message being displayed when they boot their computer:
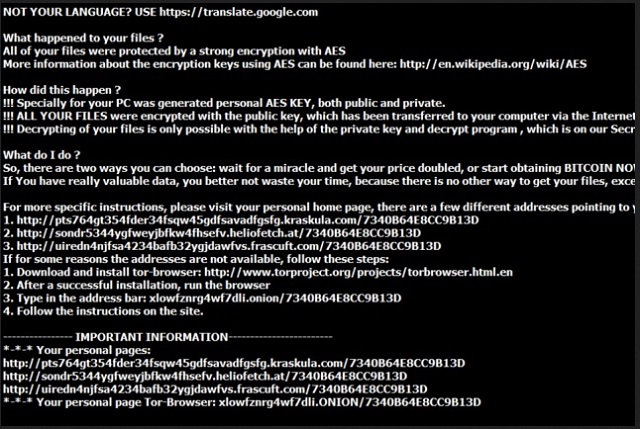
What happened to your files ?
All of your files were protected by a strong encryption with RSA-4096 using CryptoWall 3.0. More information about the encryption keys using RSA-2048 can be found here: http://en.wikipedia.org/wiki/RSA_(cryptosystem)
What does this mean ?
This means that the structure and data within your files have been irrevocably changed, you will not be able to work with them, read them or see them, it is the same thing as losing them forever, but with our help, you can restore them.
How did this happen ?
Especially for you, on our server was generated the secret key pair RSA-4096 – public and private. All your files were encrypted with the public key, which has been transferred to your computer via the Internet. Decrypting of your files is only possible with the help of the private key and decrypt program, which is on our secret server.
What do I do ?
Alas, if you do not take the necessary measures for the specified time then the conditions for obtaining the private key will be changed. If you really value your data, then we suggest you do not waste valuable time searching for other solutions because they do not exist.
For more specific instructions, please visit your personal home page, there are a few different addresses pointing to your page below:
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
1. hxxps://kpai7ycr7jxqkilp.torexplorer.com/3koe
2. hxxps://kpai7ycr7jxqkilp.tor2web.org/3koe
3. hxxps://kpai7ycr7jxqkilp.onion.to/3koe
If for some reasons the addresses are not available, follow these steps:
1. Download and install tor-browser: hxxp://www.torproject.org/projects/torbrowser.html.en
2. After a successful installation, run the browser and wait for initialization.
3. Type in the address bar: kpai7ycr7jxqkilp.onion/3koe
4. Follow the instructions on the site.
Bitcoinrush@aol.com is connected to a dangerous cyber infection. Once your system was invaded by ransomware, it displays a message that contains the email address. And, in case you were wondering, having a ransomware on your computer is NOT good. It’s quite possibly the worst type of infection you can catch. That’s because its attack is quite personal as it targets your data. Everything you have stored on your computer is in jeopardy. The ransomware is programmed to encrypt each one of your files and demand a ransom for the decryption key, required to free them. And, the tool wastes no time. Shortly after infiltration, it gets to work and takes over. All of a sudden, your pictures, documents, videos, music, etc., is no longer under your control. You find your files have been renamed with some strange new extension, and no matter how many time you rename them, you cannot open them. That’s because the encryption renders them inaccessible. Once the process is complete, and everything is encrypted, the dreaded tool makes it known that if you wish to take back your data, you have to pay a ransom. The ransomware, affiliated with Bitcoinrush@aol.com, asks for a monetary transaction in bitcoins. Do NOT pay the kidnappers! There a few ways the exchange can go down, and each one ends badly for you. It’s a game you can’t win. Yes, it’s difficult to forsake your files, but think of it this way: by letting go of your data, you protect your privacy. After all, files can be replaced. Can you say the same about your personal and financial details?
How did I get infected with?
Ransomware cannot just show up in your system one day as if by magic. There’s nothing magical about it getting on your PC. You take the blame for its appearance as you’re responsible for its installment. That’s right. You agreed to install the tool. However, don’t be too hard on yourself. Such infections, like the one hiding behind Bitcoinrush@aol.com, are immensely deceptive. They use every trick in the book to dupe you into allowing them in, without you even realizing it. More often than not, they sneak in undetected via spam email attachments. Experts advise you to be extra vigilant when dealing with suspicious-looking emails. For example, if they’re from an unknown sender, be more cautious. It’s best NOT to open it at all, but if you do, do NOT open any of the links it displays and do NOT download any of the attachments it contains. Doing either will only bring you regret and headaches. Cyber threats prey on carelessness. So, don’t provide it! Be more attentive and always do your due diligence. Naturally, that’s not the only method of invasion, which ransomware infections can turn to so as to sneak into your PC. They can also hide behind freeware, corrupted links, or sites. Whichever method they choose to use, it’s important you remember NOT to give into distraction, naivety, and haste! Instead, be more thorough and cautious. Even a little extra attention goes a long, long way.
Why is Bitcoinrush@aol.com dangerous?
Once the infection sneaks into your system, its programming kicks in, and it begins encrypting everything. Nothing is safe from its reach. Upon completion of the process, everything you had stored on your computer is no longer accessible to you. It’s under the control of the ransomware, and there is only one way to get it back – pay up. Once the tool is done encrypting your photos, music, videos, and everything else, it displays a message that explains the situation in which you find yourself. It announces that there’s a ransomware infection on your computer, that it has encrypted your data, and that if you wish to decrypt them, there’s only one way to do it – pay a ransom. The infection, hiding behind Bitcoinrush@aol.com asks for payment in bitcoins, which can amount to over $1000. Let’s say that again: $1000! But even if you choose to pay the money, there are NO guarantees these people will keep their end of the bargain. After all, you’re dealing with criminals. People, who have one goal, and it’s to exploit you for money. Do you honestly believe they’re worthy of your trust? And, even if you feel it’s worth the 50/50 chance and the $1000, do NOT pay them! By completing the transaction, you’ll grant unknown third parties access to your personal and financial information. And, once you do that, there’s no going back. Strangers with questionable intentions and possibly wicked agendas will have access to your private life. Do you think that will end well for you? Hardly. Choose yourself over your files. As was already stated, data is replaceable. Your privacy is not.
Bitcoinrush@aol.com Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Bitcoinrush@aol.com Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Bitcoinrush@aol.com encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Bitcoinrush@aol.com encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



