Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Vegclass@aol.com Ransomware?
Reader recently start to report the following message being displayed when they boot their computer:
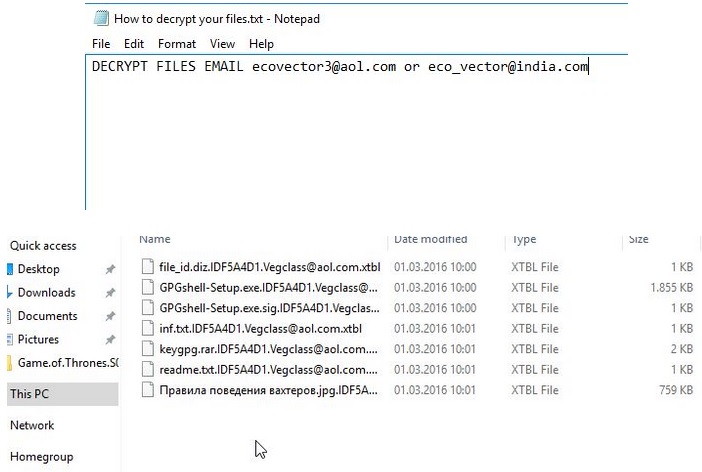
Attention!!! To restore information email technical support send 3 encrypted files Econvector3(@)aol.com or Eco_vector(@)india.com
OR
DECRYPT FILES EMAIL ecovector3(@)aol.com or eco_vector(@)india.com
Vegclass@aol.com is a malicious email address, used as a file extension, and it’s part of a ransomware infection. So, if you suddenly see it, you are one of the unlucky web users, who’ve managed to catch one of the worst cyber infections out there. Yes, ransomware programs are notoriously dangerous and damaging, and have certainly earned the title ‘worst of the worst.’ They’re designed to target your files, and take them hostage until you pay them a ransom for their release. Oh, yes. The malicious tool, which slithered into your system, will waste no time once it settles, and begin encrypting every single file you have stored on your computer. Nothing will be safe from its reach. Everything – pictures, music, videos, documents, will be locked. Files, ranging from DOC, DOCX, XLS, PDF, MP3, MP4, AVI, JPEG, GIF, etc. The ransomware is thorough. It will spread through your PC like a fast-acting disease, and encrypt everything. Once its encryption process is complete, you’ll find you files renamed and inaccessible. You won’t be able to open a single one. And, if you wish to change that, and regain your control over them, you have to pay the ‘kidnappers.’ If you comply and follow the instructions, which these people will provide you with, they will, supposedly, send you a decryption key, which you can use to free your files. ‘Supposedly’ being the word of the day. Don’t forget you’re dealing with unknown individuals that support a malicious, harmful tool, which locks your files, and demands payment for their release. They cannot be trusted to keep their end of the deal. There are no guarantees that even if you comply, you’ll gain back your data. So, experts advise NOT to pay at all. To pay is to get stuck in a worse situation, so don’t. Avoid a bigger mess by sacrificing your files for your privacy. It’s a difficult decision to make, but in the long run, it’s certainly the right one.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How did I get infected with?
Ransomware cannot just magically show up on your computer. Even though that’s probably not what you were hoping to hear, you’re responsible for the infection’s unexpected appearance. First, you need to understand that tools like the one hiding behind the Vegclass@aol.com email, cannot enter your PC without explicit permission to do so. At some point, the ransomware asked whether you agree to install it and, evidently, you obliged. Otherwise, you wouldn’t be reading this article right now. It should be noted, however, that the tool doesn’t just openly ask for permission. Oh, no. Don’t expect anything less that mastery of slyness and finesse. The tool uses every known trick in the book to meet its restrictions and ask for approval, while staying in the shadows and attempting to avoid getting noticed. Do you know how it accomplishes that? Like most cyber threats, this one turns to the old but gold methods of infiltration. It often hides behind freeware, corrupted links or sites, spam email attachments, or bogus updates. If you wish to prevent such sneaky infections from invading your system, be more vigilant! Don’t be careless but, instead, be more thorough. Always do your due diligence and take your time when installing a tool or an update. Carefully read the terms and conditions, instead of just agree with everything and hope for the best. That’s a horrendous strategy, which you’ll come to regret. Choose caution over carelessness. Your future self will thank you for it.
Why is Vegclass@aol.com dangerous?
Once the ransomware gains entry, its programming kicks in, and it begins encrypting your data. You’ll find every file on your computer renamed with an added .vegclass@aol.com extension. For example, if you had a music file, called ‘bestsong,’ you’ll now see it as ‘bestsong.vegclass@aol.com.’ This renaming process will render your files inaccessible, and you won’t be able to open them. Once the ransomware is done, and your files are under its control, the pesky tool makes sure to inform you of your current predicament. It changes your wallpaper to a How to decrypt your files.png one, and leaves a How to decrypt your files.txt file, which will contain the instructions you must follow. Your new desktop picture contains a precise and to-the-point message, which it leaves nothing to th imagination – “Attention!!! To restore information email technical support send 3 encrypted files to Econvector3(@)aol.com or Eco_vector(@)india.com,” or the even shorter version – “DECRYPT FILES EMAIL ecovector3(@)aol.com or eco_vector(@)india.com.” If you send three of your encrypted files to the emails, which these people displayed, they will decrypt them for you as a sign of good faith. But that doesn’t mean that they are trustworthy. If anything, that just proves how cunning they are in their attempts to get you to pay the ransom. So, think about this. If you pay up, there’s nothing to stop them from sending you the wrong decryption key, or not sending you one at all. Or, even if everything is fine with the key and it works, what is preventing the ransomware from kicking back in the very next day, and encrypting your data once more? Nothing. The answer is nothing. And, not only will you lose money, and gain the opportunity of dealing with the infection again and again, but paying also raises a severe security issue. To transfer money to these individuals is to provide them with your personal and financial information. And, that’s hardly desirable. Don’t allow strangers into your private life! Nothing positive will come from that. Keep your money, protect your privacy, and discard your data. Your files aren’t worth the gamble.
Vegclass@aol.com Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Vegclass@aol.com Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Vegclass@aol.com encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Vegclass@aol.com encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



