Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove WildFire Locker Ransomware?
Reader recently start to report the following message being displayed when they boot their computer:
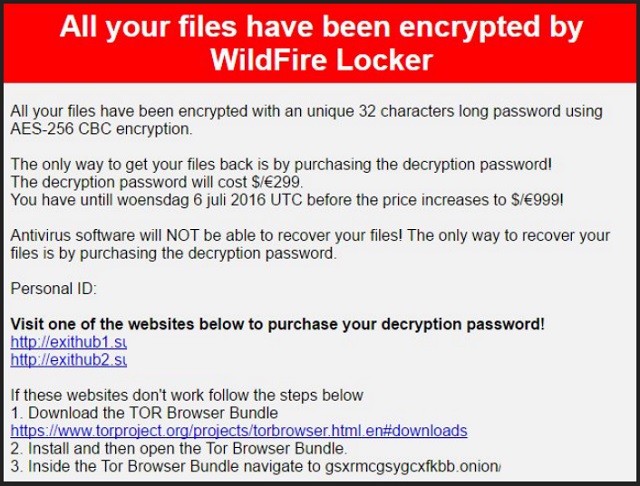
All your files have been encrypted by WildFire Locker
All your files have been encrypted with an unique 32 characters long password using AES-256 CBC encryption.
The only way to get your files back is by purchasing the decryption password!
The decryption password will cost $/€299.
You have untill woensdag 6 juli 2016 UTC before the price increases to $/€999!
Antivirus software will NOT be able to recover your files! The only way to recover your files is by purchasing the decryption password.
Personal ID: –
Visit one of the websites below to purchase your decryption password!
If these websites don’t work follow the steps below
1. Download the TOR Browser Bundle hxxps://www.torproject.org/projects/torbrowser.html.en#downloads
2. Install and then open the Tor Browser Bundle.
3. Inside the Tor Browser Bundle navigate to gsxrmcgsygcxfkbb.onion/
WildFire Locker does indeed spread like a wild fire. And it’s just as devastating in the cyber world. This program’s name is definitely more accurate than the names of other similar infections we’ve tackled. Not to mention, it’s a lot less dramatic. Take for example Juicy Lemon, Jigsaw, Cerber, Ninja, CryproJoker and Locky. Now, the virus you’re stuck with belongs to the nasty ransomware family. Trust us when we say, this is a family you don’t want to have absolutely anything to do with. You know how some programs slither onto your PC system and lock your personal files? That’s ransomware. Being a classic ransomware-type infection, this is what WildFire Locker does as well. It uses the notoriously harmful AES -256 CBC encrypting cipher in order to encrypt your files. Music, pictures, videos, Microsoft office documents, etc. – the virus doesn’t discriminate. A huge percentage of your personal data falls victim to WildFire Locker and its nasty shenanigans. That means .jpg, .jpeg, .pdf, .png, .txt, .xls, .doc, .docx, .mdb, .html and many more file formats get encrypted. Logically, the parasite’s goal is to infect as much data as possible. By using an asymmetric algorithm, WildFire Locker does exactly what its name implies – locks your data. It renames the target files and adds to them a malicious .wflx extension. The minute you see this extension, consider your information gone. Remember, ransomware was solely developed to cause damage. It’s doing that job pretty well, unfortunately. Your encrypted data now looks like this – Filename#WildFire_Locker#[original file name]##.[original extension].wflx. The problem with this file format (apart from the fact it was created by hackers) is that it’s unreadable. Your computer can’t recognize this file format, thus, you can’t use you files. Simple as that. Ransomware applies quite a clever technique by taking down your personal data. Many people would panic when all of a sudden their files become inaccessible. Panic is your worst enemy right now. While encrypting your data, the parasite also drops .txt, .html and .bmp files. They contain payment instructions. You see where this is going, don’t you? WildFire Locker is attempting to blackmail you. As you could imagine, this whole thing is nothing but a nasty cyber fraud that could seriously damage your bank account. The ransom note claims you have to pay “$/€299 in Bitcoins within one week”. If you don’t make the payment on time, the sum is supposed to reach $/€999. Are your files really worth that much? Hackers promise a decryption password in exchange for the ransom. However, you shouldn’t even consider giving your money away. This is a trap.
How did I get infected with?
Ransomware in general and WildFire Locker in particular travel the Web in silence. It goes without saying nobody would download cyber infections voluntarily, right? Some of the popular infiltration methods include spam email-attachments and spam messages. Next time you receive something suspicious-looking in your inbox, simply delete it. WildFire Locker may have gotten installed via a corrupted freeware bundle or a malicious torrent. Always watch out for potential infections and pay attention online. Rushing can’t guarantee you safety. In addition, avoid third party-pop-ups and unreliable websites. Those might turn out to be dangerous as well. WildFire Locker could also get installed with the help of a sneaky Trojan or through a fake software update. You see, there are many threats on the Web. Make sure you outwit crooks in order to protect your machine from malware.
Why is WildFire Locker dangerous?
The WildFire Locker virus firstly performs a thorough scan on your machine. This way the parasite successfully locates your private files. As already mentioned, WildFire Locker takes down all kinds of file formats thus causing you a great headache. When your data gets encrypted, the ransomware starts playing mind games with you. According to a .txt file named HOW_TO_UNLOCK_FILES_README_(victim’s unique ID).txt, you have to make a payment. Keep in mind that you’d be making a deal with cyber criminals, though. Why would you trust hackers? They have no reason whatsoever to follow the rules (even the rules they invented). In the worst possible scenario you’ll still have your files locked and, on top of it, you’ll lose a hefty sum of money. Never negotiate with crooks. Instead, uninstall their malicious parasite on the spot. To do so manually, please follow the comprehensive removal guide down below.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
WildFire Locker Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover WildFire Locker Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with WildFire Locker encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate WildFire Locker encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



