Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Vault File Extension Ransomware?
Ransomware is known to be one of the most dangerous and aggressive kinds of PC infections out there and it’s an incredibly unpleasant sight on any computer screen. The way this utter pest works is, it slithers its way into the machine through lies and deceit, then it encrypts a huge part of your very own personal files and denies you access to your data. The parasite even has the colossal impudence to ask for a certain sum of money (and usually, not a small one) in order to restore your files and it also claims that if you refuse to play by hackers’ rules, your movies, pictures and music will be lost forever. Quite nasty, don’t you think? Ransomware parasites directly aim for stealing your money and in case you’re gullible enough, you might fall victim to this trickery. Now, back to your problem. We spent so much time explaining the malicious ways of ransomware for one very simple reason – you have been infected with it. If you notice that your files have changed format and their names now include a random .vault extension that your computer can’t recognize, stop wondering what happened to your machine. You’re dealing with ransomware and, to be exact, you’re dealing with the nasty VaultCrypt virus. This parasite was mainly oriented towards Russian and other Slavic PC users but that doesn’t mean it cannot get installed on your machine everywhere on the globe. As we mentioned, ransomware relies mainly of the fact you would be nervous/anxious enough to obey the malicious instructions provided by the crooks and, ultimately, pay the ransom demanded. Therefore, that is exactly what you should NOT do. Remember, you have no reason to become a sponsor of crooks and they have no reason to follow the rules. Paying the ransom will not regain you access to your files and will not result in anything else but the sole fact you will lose money. Does this sound fair to you? In order to learn how to both delete the parasite and restore your data, keep on reading.
How did I get infected with?
You obviously didn’t install the parasite voluntarily, then how did the cyber infection end up on your PC system? That’s probably the most commonly asked question when it comes to viruses but, unfortunately, it’s almost impossible to know exactly how and why the ransomware parasite landed on your PC. Such programs usually travel the Web attached to spam emails or spam messages that you might have clicked open thus giving green light to the parasite. Another possibility is that you were careless enough to click some corrupted third-party web link or you downloaded a freeware/shareware bundle from a questionable website. Now, you certainly don’t want to underestimate the great danger bundles could pose to your safety. All types of viruses might be attached to the legitimate software you attempt to install so unless you’re extremely careful and very cautious, you may end up letting a huge variety of PC issues land on your machine. To avoid such an unpleasant scenario, always select the advanced or the custom option in the Setup Wizard instead of the basic one. This way you remain in control of the programs that enter your machine and you will surely not get a nasty surprise on the PC screen later on. Also, it’s highly recommended that you go through the Terms and Conditions of the software you’re downloading unless you’re willing to jeopardize your very own cyber security.
Why is Vault File Extension dangerous?
There is only one reason why ransomware infections exist in the first place – to take away your money. Harassing you is just a bonus. After this parasite successfully lands on the PC, it performs a full scan searching for your .doc, .jpg, .xls, .mdb, .pdf, .cd, rtf files. Then the devious ransomware program encrypts them and completely denies you access to your own files. It goes without saying that there might be some really important and valuable information infected by the parasite as well but now that all of your data includes the malicious .vault extension it’s practically unreadable. As you can see, however unrighteous this tactic is, keeping most of your data hostage is an extremely efficient way to make you pay the money demanded by the crooks. You will see a warning message claiming the only way to recover you files would be paying the ransom in bitcoins and it’s not shocking news that this is nothing but a cyber scam. Hackers are supposed to provide you a decryption key In exchange for your money – a unique combination of symbols which will allow you to view and use your data again. The only program is, hackers don’t play by the rules, even if it’s the rules they invented themselves. There is absolutely no guarantee that you will receive anything from the cyber criminals so, obviously, paying the money would be a terrible idea. To sum up, not only does this virus modify the Windows registry behind your back in order to include the nasty .vault extension thus locking your private data but it also directly asks for illegal money. If you don’t appreciate being manipulated, having you access restricted and being blackmailed and you want to regain control over the PC and to restore all your files, get rid of the ransomware. In order to delete this virus manually, please follow the detailed removal guide down below.
Vault File Extension Removal Instructions
STEP 1: Start Your Computer into Safe Mode with Networking
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Restart the computer
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.

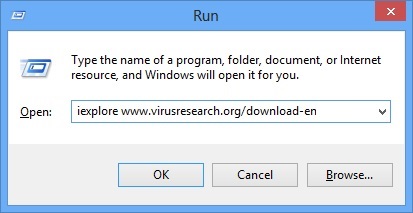
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type iexplore www.virusresearch.org/download-en
- Internet Explorer will open and a professional scanner will prompt to be downloaded
- Run the installer
- Follow the instruction and use the professional malware removal tool to detect the files of the virus.
- After performing a full scan you will be asked to register the software. You can do that or perform a manual removal.
Remove Vault File Extension Manually
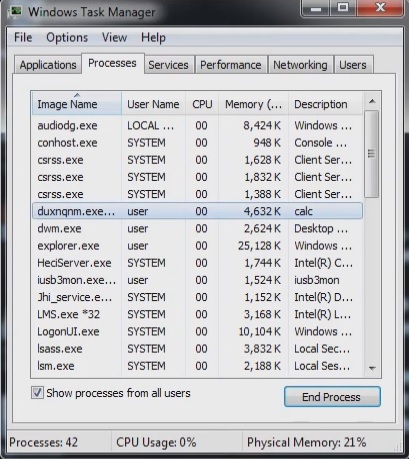
Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
Locate the process of teslacrypt. Have in mind that this is usually a random generated file.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Before you kill the process, type the name on a text document for later reference.
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you run the professional scanner to identify the files.
It is always a good idea to use a reputable anti-malware program after manual removal, to prevent this from happening again.
STEP 3: Restore Vault Encrypted Files
There are several methods you can use, however nothing is guaranteed.
Method 1 – recover the encrypted files by hand:
You can try to use the built in feature of Windows called System Restore. By default the system restore feature is automatically turned on. Windows creates shadow copy snapshots that contain older copies since the system restore was performed. These snapshots will let us to recover any previous version of your file, although it will not be the latest one, still you can recover some important information. Please note, that Shadow Volume Copies are only available with Windows XP SP2, Vista, Windows 7 and Windows 8.
Method 2 – partially restore the encrypted files by using Microsoft Office junk files:
Basically you need to show your hidden files. The fastest way to do that is:
- Open Folder Options by clicking the Start button .
- In the search box type “FOLDER OPTIONS”.
- Select View TAB
- Under Advanced settings, find Show hidden files and folders and select it and then click OK.
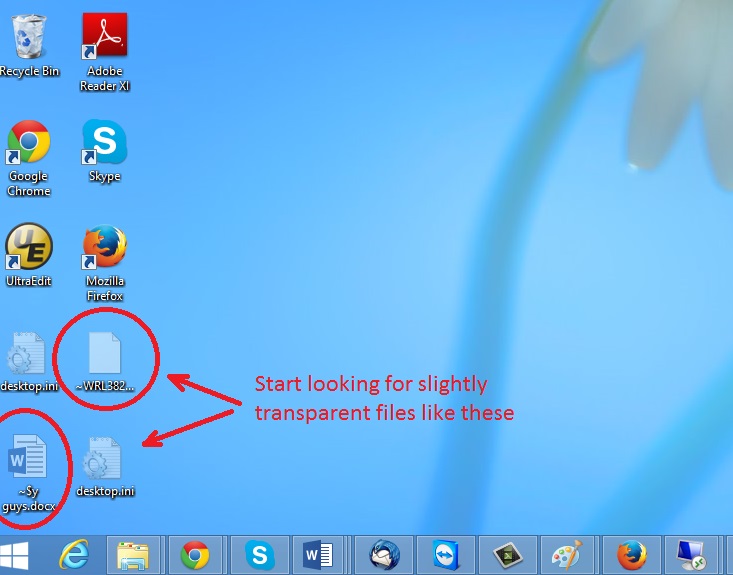
In the picture above I marked two hidden files. You are interested in every file that looks like ~WRL382.tmp This is actually a Microsoft office junk file that contains the previous version of the Word document itself. The Cryptowall parasite will not encrypt these files. The name of the file will be unknown, but you can recover a lot of lost documents using this method. This can be utilized for Microsoft Word and Microsoft Excel. In addition you can try to match the file sizes in order to figure out what is what and eventually you can restore a slightly older original document. In the picture on the left there is another method you can locate the files in question.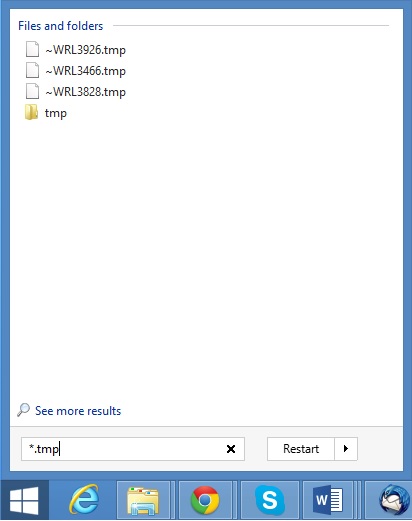 All you have to do is to hit the start button and type *.tmp. You will be presented a list of all the temp files located in your computer. The next thing is to open them one by one with Microsoft Word/Excel and recover the lost information, by saving it to another place. You can do that, by opening a new instance of MS Word/Excel, trough the file menu select open and then navigate to the location of the TMP file.
All you have to do is to hit the start button and type *.tmp. You will be presented a list of all the temp files located in your computer. The next thing is to open them one by one with Microsoft Word/Excel and recover the lost information, by saving it to another place. You can do that, by opening a new instance of MS Word/Excel, trough the file menu select open and then navigate to the location of the TMP file.
Method 3 – Decrypt Encrypted Files
A few tools has been developed to try that – like the Panda Ransomware Decrypt Tool, however nothing is guaranteed. If you go that way you should know that there are some limitation like you have to have an original and encrypted file in order to try to find a proper key.