Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Trojan.Reconyc just keeps popping up and you cannot remove it?
As the name suggests, Trojan.Reconyc is part of the Trojan family. It’s a nasty cyber menace that threatens the well-being of your system. The infection dupes you into giving it the green light of admission. Yes, you approve its installation. And, despite giving your consent to let it in, you have no idea it’s even there. That’s how the program works. It sneaks in undetected, and reveals itself on its own time. It usually clues you in when the meddling begins. When that time comes, it’s pretty hard to ignore it. You suffer from frequent online intrusions. Like, a pop-up bombardment, and constant redirects. Your system crashes more often, and your computer’s performance slows down to a crawl. And, since everything the Trojan shows you is unreliable, you face many risks. Like, a severe malware risk. That’s right. For example, if you make the mistake of pressing a single pop-up, that’s it. You get stuck with more unwanted infections. A click equals your consent on installing more cyber threats. So, you’d better not click on anything, the Trojan displays. What’s worse, the malware threat isn’t even the worst threat you face. Do yourself a favor, and don’t take chances. As soon as you become aware of the infection’s presence, act! Find where its hiding place is on your system, and delete it upon discovery! The more time the Trojan spends on your PC, the more issues you’ll face. So, act sooner rather than later. Locate and delete it the first chance you get.

How did I get infected with?
Like most cyber infections, Trojan.Reconyc turned to deception to invade your system. As was already stated, it duped you into installing it. All the while, hiding its existence from you until it decided otherwise. But, still. How do you suppose you approved a program in, but not realize it? Well, the tool used your carelessness against you. Trojans are masters of slyness and subtlety. And, Trojan.Reconyc is no exception. It snuck past you with the help of the old but gold means of infiltration. Like, hiding behind spam email attachments, corrupted links, or freeware. The Trojan can also pretend to be a fake system or program update. For example, you believe you’re installing a Java update, but you’re not. In actuality, you’re allowing a dangerous cyber plague into your system. That’s why caution is crucial! Always make sure to read the terms and conditions. Take the time to do your due diligence. That extra time you spend being vigilant and thorough can save you countless issues. Remember. Infections prey on carelessness. Don’t provide it. Turn to caution instead.
Why is this dangerous?
Trojan.Reconyc exhibits the standard Trojan traits. After is slithers into your system undetected, it doesn’t waste much time. The tool’s programming kicks in shortly. Pretty soon after invasion, you begin to suffer the Trojan’s touch. Trojan.Reconyc is an invasive application. It meddles with your system settings, changing them as it so wishes. You’ll have to endure a lot of unapproved reshuffles. Like, a replaced search engine and homepage. But that’s the least of your concerns, having to do with your browsing. Once the Trojan settles, it turns your online activities into an unbearable mess! Every time you open your browser or a new tab, you get interrupted. You suffer redirects to suspicious websites. You also get stuck with a myriad of pop-up ads taking over your screen, as well. The never-ending flood of pop-ups and the redirects are constant. And, they have consequences. They end up slowing down your computer, and causing frequent crashes. But, these are the minor inconveniences you face. Even the malware risk we explained above pales in comparison. The most unfortunate issue you encounter is the security threat. Trojan.Reconyc jeopardizes your personal and financial information. It spies on your browsing habits, catalogs them, and then sends the gathered data. To whom? Well, to the third parties that published it. Keep your private life away from strangers with agendas! Delete the Trojan as soon as the opportunity presents itself.
Manual Trojan.Reconyc Removal Instructions
STEP 2: Windows 7/XP/Vista Removal
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Start Your Computer into Safe Mode with Networking in Windows 8
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Move the mouse to the upper right corner until the windows 8 charm menu appears
- Click on the magnifying glass
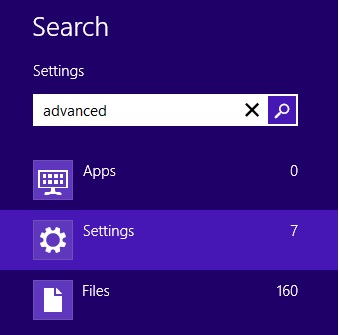
- select Settings
- in the search box type Advanced
- On the left the following should appear
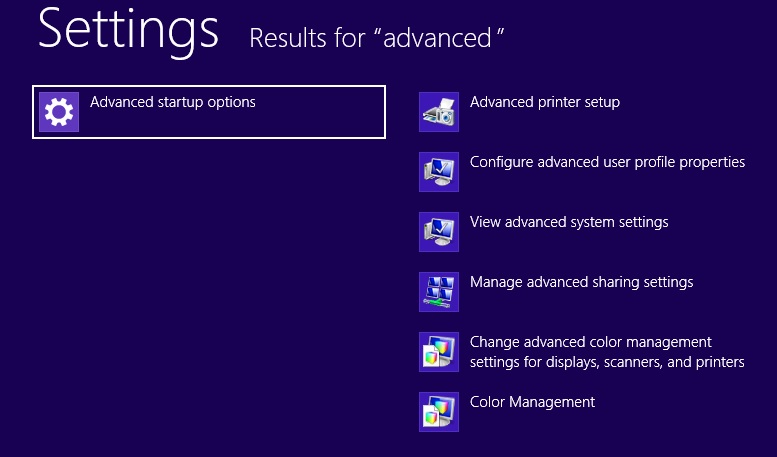
- Click on Advanced Startup Options
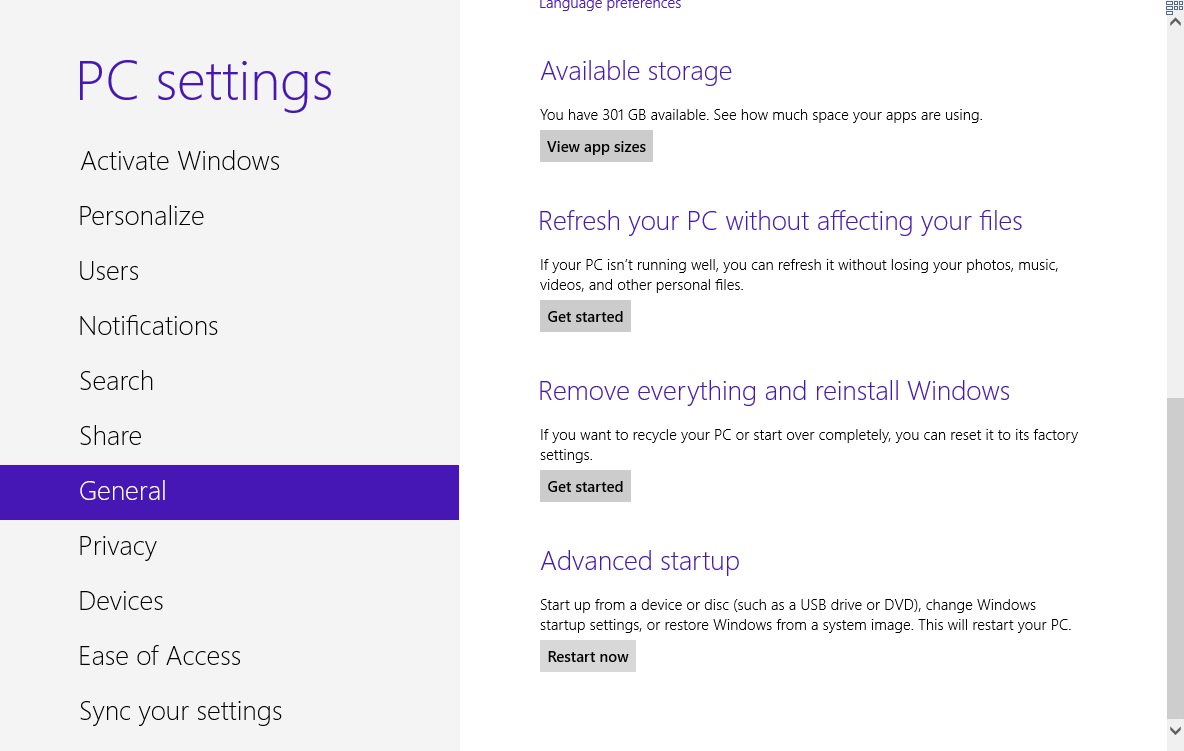
- Scroll down a little bit and click on Restart Now
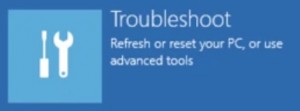
- Click on Troubleshoot
- Then Advanced options

- Then Startup settings

- Then Restart
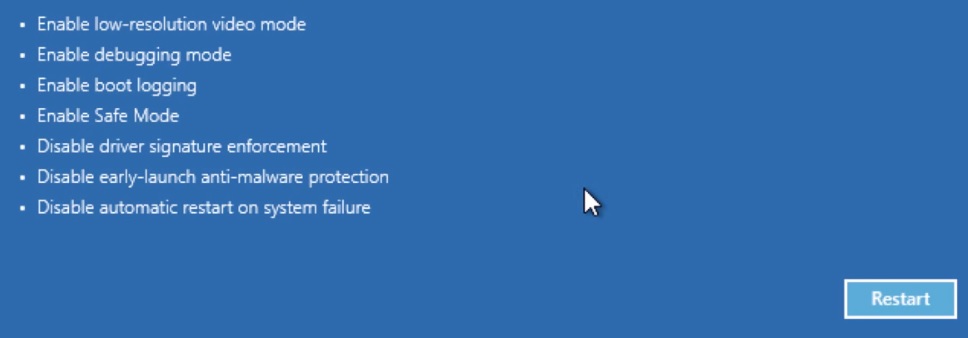
- When you see this screen press F5 – Enable Safe Mode with Networking

STEP 2: Start Your Computer into Safe Mode with Networking in Windows 7/XP/Vista
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Restart the computer
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.

STEP 3: Locate the startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: backgroundcontainer

- Then open your explorer and navigate to:
%LocalAppData%\uqgtmedia
where %LocalAppData% refers to:
C:\Users\{username}\AppData\Local
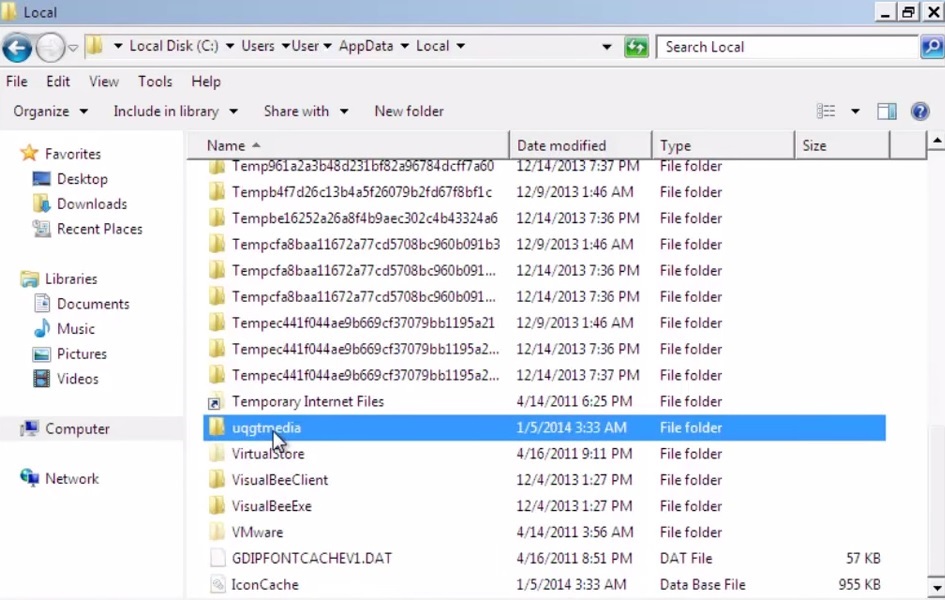
- delete the whole folder
Double check with any antimalware program for any leftovers. Keep your software up-to date.



