Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
This article can help you to remove Triton Virus. The step by step removal works for every version of Microsoft Windows.
Trojans are probably the most feared cyber infection. There is a good reason for that. These parasites are deadly. They sneak into your computer unnoticed and wreak total havoc. Before you even notice them, your entire OS is infected. Triton Trojan is not an exception. On the contrary. This particular parasite is an example of an advanced Trojan. Following a successful installation, Triton Trojan roots deeply into your system. It corrupts essential files and system processes. It creates its own entries in your System Registry and deletes unwanted ones. The virus successfully interferes with most anti-virus programs. The virus can completely disable your anti-virus app. It is a breach of your security. What is interesting about this Trojan is that it uses a Python executable. This unusual choice of programming language confirms the assumption that the hackers behind the parasite are not only imaginative but also quite capable. Their creation is deadly. Triton Trojan can cause irreversible damage. It is programmed to steal personal data (online banking details, personally identifiable information, usernames, passwords, etc.). The Trojan can also be used for industrial espionage, as well as sabotage. This parasite can download and install third-party software. It gives the hackers a way to control your computer. Triton Trojan is a serious infection. Do not waste your time. Act against the parasite. We have provided a manual removal guide. Yet, bear in mind that the removal process requires advanced computer skills. If you fail to delete all components of the virus, it will re-install itself. If you, on the other hand, delete too many files (the wrong files), your system will crash. Therefore, we recommend you to use a powerful anti-malware program.

How did I get infected with?
Triton Trojan uses a few distribution methods. Torrents, fake updates, software bundling. Yet, one technique stands out. The good old spam emails are the number one cause of Trojan infections. Do not open emails from strangers. If you receive such a letter, verify it. The crooks tend to write on behalf of well-known organizations, companies, post offices, banks, police departments, etc. If you receive such a message, go to the organization’s official website. Compare the email addresses listed there with the one you have received a letter from. If they don’t match, delete the pretender immediately. When you open a questionable email, opt for red flags. A reliable company would use your real name to address you. Thus, is the letter starts with “Dear Customer” or “Dear Friend,” proceed with caution. You probably know that the attached files can be corrupted. Did you know that a hyperlink can be corrupted too? Do not follow links blindly. If you are not sure whether a message is legit or not, contact the organization. It is up to you to keep your computer virus-free. Be always vigilant and doubting. Even a little extra caution goes a long way.
Why is this dangerous?
Triton Trojan is extremely dangerous. Once on board, it corrupts your entire system. It is a camouflage master. So, you are in fact lucky to know that your computer is infected. The Trojan can spend days, even weeks on one’s computer without raising an alarm. The more time it remains active, the worst your predicaments become. Triton Trojan collects information about you. It knows what you do online and what files you have saved on your computer. The Trojan can steal personal data. It may also delete files. This pest has admin privileges. It can modify your system settings, install new programs and even uninstall your software. What will happen to your computer depends on the hackers and what they want and need. They can turn your machine into a coin miner or into a part of a botnet. Or they may continue to spy on you. All possible outcomes are unwanted. Do not waste precious time. Clean your computer now!
Manual Triton Removal Instructions
The Triton infection is specifically designed to make money to its creators one way or another. The specialists from various antivirus companies like Bitdefender, Kaspersky, Norton, Avast, ESET, etc. advise that there is no harmless virus.
If you perform exactly the steps below you should be able to remove the Triton infection. Please, follow the procedures in the exact order. Please, consider to print this guide or have another computer at your disposal. You will NOT need any USB sticks or CDs.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Track down Triton related processes in the computer memory
STEP 2: Locate Triton startup location
STEP 3: Delete Triton traces from Chrome, Firefox and Internet Explorer
STEP 4: Undo the damage done by the virus
STEP 1: Track down Triton related processes in the computer memory
- Open your Task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Carefully review all processes and stop the suspicious ones.

- Write down the file location for later reference.
Step 2: Locate Triton startup location
Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
Clean Triton virus from the windows registry
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to: %appdata% folder and delete the malicious executable.
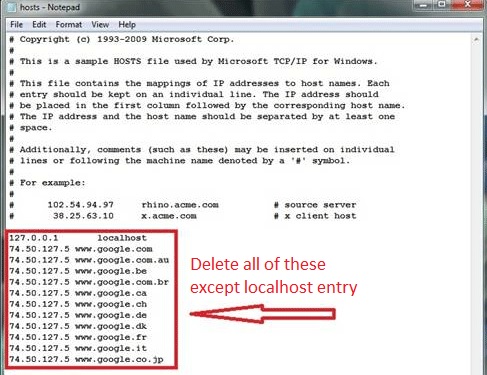
Clean your HOSTS file to avoid unwanted browser redirection
Navigate to %windir%/system32/Drivers/etc/host
If you are hacked, there will be foreign IPs addresses connected to you at the bottom. Take a look below:
Step 4: Undo the possible damage done by Triton
This particular Virus may alter your DNS settings.
Attention! this can break your internet connection. Before you change your DNS settings to use Google Public DNS for Triton, be sure to write down the current server addresses on a piece of paper.
To fix the damage done by the virus you need to do the following.
- Click the Windows Start button to open the Start Menu, type control panel in the search box and select Control Panel in the results displayed above.
- go to Network and Internet
- then Network and Sharing Center
- then Change Adapter Settings
- Right-click on your active internet connection and click properties. Under the Networking tab, find Internet Protocol Version 4 (TCP/IPv4). Left click on it and then click on properties. Both options should be automatic! By default it should be set to “Obtain an IP address automatically” and the second one to “Obtain DNS server address automatically!” If they are not just change them, however if you are part of a domain network you should contact your Domain Administrator to set these settings, otherwise the internet connection will break!!!
- Check your scheduled tasks to make sure the virus will not download itself again.
How to Permanently Remove Triton Virus (automatic) Removal Guide
Please, have in mind that once you are infected with a single virus, it compromises your whole system or network and let all doors wide open for many other infections. To make sure manual removal is successful, we recommend to use a free scanner of any professional antimalware program to identify possible virus leftovers or temporary files.