Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
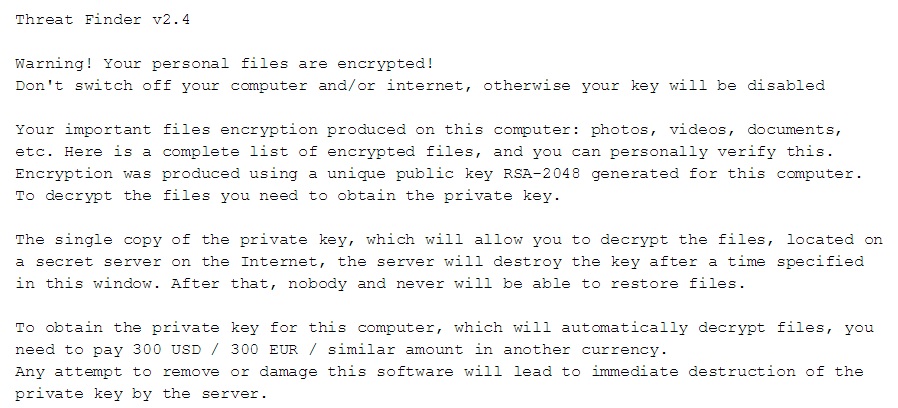
If you are seeing “Warning! Your Personal Files are Encrypted” message – don’t panic!
Threat Finder is a malicious ransomware. After it infects your computer, it acts like the typical kidnapper. It takes charge of your computer and encrypts all of your files – photos, documents, pictures, videos, music, everything. After the encryption is done, and your computer is locked and unusable, the malware displays a message seeking ransom. Threat Finder usually demands to be paid $300 in order to “release” your data unharmed. However, caution is advised. Even if you do pay, there is absolutely NO guarantee that the ransomware will decrypt your files. The best thing, you can do to protect yourself from this malevolent, damaging program is to create backups of your data. That way, even if Threat Finder “kidnaps” your computer, you’ll have nothing to lose and you can ignore the ransomware and its demands.
Threat Finder usually slithers its way into your system by hiding behind spam email attachments, corrupted websites, or links. Also, it often hitches a ride with freeware as it provides the perfect cover for this malicious and harmful program. That’s because, most users pay little to no attention when going through its install, and seem to believe it’s a sublime idea to skip reading the terms and conditions. They agree to everything in haste and pay for their distraction as they quickly find that this is NOT a sublime idea. If you want to avoid putting everything you have stored on your PC in harm’s way, be more attentive! Maybe if you’re a bit more careful, you’ll avoid getting stuck with a dangerous ransomware application like Threat Finder.
After Threat Finder encrypts your files and places your computer in lock down, it states its demands. As was already mentioned, the malware informs you that you have to pay $300 if you wish to have your files decrypted. To pressure you into giving in, it even displays the exact moment when you’ll run out of time, and your files will be left encrypted. Don’t panic! Panic will only make you pay, and that’s not a good idea. Threat Finder usually gives you 72 hours to respond, which means you have four days to fulfill its request and to make it easier for you to do so, the ransomware provides you with payment options. You can choose to pay via Bitcoin or MoneyPak, and the cyber kidnappers give you detailed instructions on how you can pay using either method. It seems easy enough but when you think about it, you have no idea whether it will work. You have to ask yourself if there is something on your computer worth gambling $300 for? Think long and hard before you answer, and know that like all kidnappers, the people behind Threat Finder cannot be trusted. They’re only using you to make some quick cash, and for all you know, they might leave your files encrypted even if you do pay the ransom. That’s why it’s advised to not give into Threat Finder’s demands. Don’t humor the program and the third parties behind it!
Threat Finder Removal Instructions
STEP 1: Start Your Computer into Safe Mode with Networking
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Restart the computer
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.

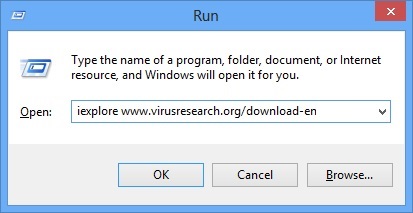
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type iexplore www.virusresearch.org/download-en
- Internet Explorer will open and a professional scanner will prompt to be downloaded
- Run the installer
- Follow the instruction and use the professional malware removal tool to detect the files of the virus.
- After performing a full scan you will be asked to register the software. You can do that or perform a manual removal.
Remove Threat Finder Manually
You need to delete the following files and registry keys. These were in our case:
%UserProfile%\Start Menu\Programs\Startup\ctfmon.lnk
%UserProfile%\Application Data\nur-xcp-sabb.pad
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
%UserProfile%\Application Data\lsass.exe
the Trojan creates the following registry entries which you need to delete:
HKCU\Software\Microsoft\Internet Explorer\Main\”NoProtectedModeBanner” = “1”
Delete the created registry entries to revert the internet protection of the compromised computer:
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\4\”2500″ = “3”
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\3\”2500″ = “3”
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\2\”2500″ = “3”
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\1\”2500″ = “3”
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\0\”2500″ = “3”
Modifies the following registry entries:
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\4\”1609″ = “0”
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\3\”1609″ = “0”
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\2\”1609″ = “0”
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\1\”1609″ = “0”
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\0\”1609″ = “0”
the Trojan locks the computer and displays a fraudulent message on the screen informing the user that they are in breach of copyright law. You need to locate the picture and delete it.
You can alternatively use your msconfig to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you run the professional scanner to identify the files.
It is always a good idea to use a reputable anti-malware program after manual removal, to prevent this from happening again.