Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Purge Ransomware?
Reader recently start to report the following message being displayed when they boot their computer:
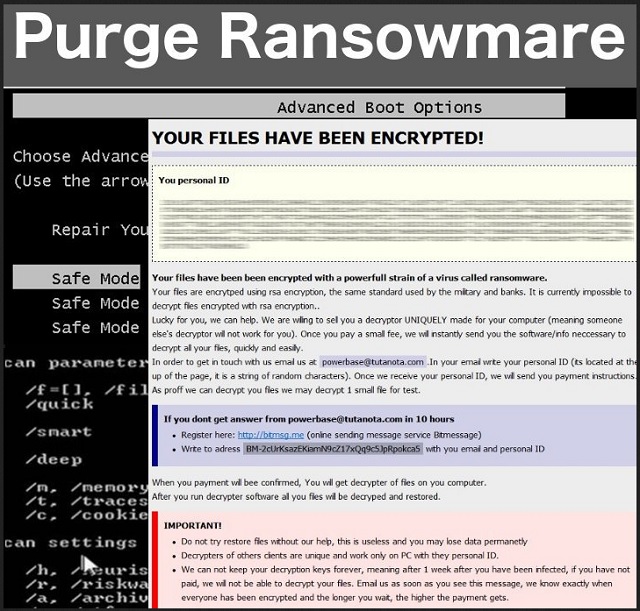
YOUR FILES HAVE BEEN ENCRYPTED!
Your files have been been encrypted with a powerfull strain of a virus called ransomware. Your files are encrytped using rsa encryption, the same standard used by the military and banks. It is currently impossible to decrypt files encrypted with rsa encryption.
Lucky for you, we can help. We are willing to sell you a decryptor UNIQUELY made for your computer (meaning someone else’s decryptor will not work for you). Once you pay a small fee, we will instantly send you the software/info neccessary to decrypt all your files, quickly and easilly.
In order to get in touch with us email us at powerbase@tutanota.com.In your email write your personal ID (its located at the up of the page, it is a string of random characters). Once we receive your personal ID, we will send you payment instructions.
As proff we can decrypt you files we may decrypt 1 small file for test.
If you dont get answer from powerbase@tutanota.com in 10 hours
Register here: hxxp://bitmsg.me
Write to adress BM-2cUrKsazEKiamN9cZ17xQq9c5JpRpokca5 with you email and personal ID
When you payment will bee confirmed, You will get decrypter of files on you computer. After you run decrypter software all you files will be decryped and restored. Do not try restore files without our help, this is useless and you may lose data permanetly. Decrypters of others clients are unique and work only on PC with they personal ID. We can not keep your decryption keys forever, meaning after 1 week after you have been infected, if you have not paid, we will not be able to decrypt your files. Email us as soon as you see this message, we know exactly when everyone has been encrypted and the longer you wait, the higher the payment gets.
One brand new cyber infection you might stumble across is Purge Ransomware. As its name implies, this is a ransomware-type program. The summer of 2016 has been quite rich in these pests so far. We’re pretty much facing new infections every day and Purge is one of them. You’re now stuck with a dangerous, aggressive and problematic kind of virus. Ransomware is so immensely dreaded for a reason. Numerous reasons, actually. These infections encrypt your personal files and leave them unusable. Take Purge Ransomware, for instance. Being a classic representative of the ransomware family, it doesn’t deviate from the rules. It’s quite similar to Cerber, Bart, UltraCrypter, etc. What all these infections share is the fact they aim directly at your bank account. Purge is just the nth parasite that tries to steal your money. It uses an asymmetric encrypting algorithm in order to lock your files. And it succeeds. The parasite takes down all private data it manages to locate. Pictures, music, videos, MS Office documents. Anything of value you might have stored on board falls victim to this nuisance. It infects a huge percentage of your private information and encrypts the target data. Purge Ransomware utilizes RSA and the AES-256 cipher. Unfortunately, this is a particularly complicated algorithm. Anything the virus locks remains locked. Purge creates two keys – a public one and a private one. You need the private key to free your infected data. The only trouble is, hackers aren’t willing to give this key for free. Quite the opposite. The demand a certain sum of money in Bitcoins, a “small fee”, as they call it. However, their “small fee” varies between 1 Bitcoin (580 USD) and 3 Bitcoins (1740 USD). It seems that crooks’ idea of a small sum is quite different from ours. When locking your files, Purge Ransomware adds a malicious extension to them – .purge. This malicious appendix replaces the original file extension. That’s how you know for sure that you’re dealing with ransomware. The virus also drops payment instructions and tries to blackmail you. As mentioned already, though, paying the money would be a terrible mistake. Restrain yourself from contacting hackers and don’t even consider paying the ransom. Giving your money to crooks will not solve anything. It might make your situation worse, though. You may end up with your PC still infected, your files still unreadable and your Bitcoins gone.
How did I get infected with?
Ransomware uses secretive and stealthy methods to get spread online. For example, Purge might have landed on board via some email-attachment. Stay away from spam messages/emails from unknown senders and be careful. Sometimes you only need about as much as a single careless click to install malware. How do you prevent this? Pay attention on time. Delete what you don’t trust and be careful. Preventing installation is much easier than having to uninstall a virus afterwards. Thus, always keep an eye out for potential infections. Another popular infiltration method is freeware/shareware bundling. Ransomware also travels the Web via Trojans, fake software updates, illegitimate torrents. There are plenty of clever infiltration techniques so make no mistake. You have to outwit crooks on a daily basis. Last but not least, ransomware might get installed when you visit a malicious website.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Why is Purge dangerous?
Ransomware is both sneaky and destructive. Quite a combination, right? Purge is the nth irritating ransomware-type infection out there. Obviously, it doesn’t belong on your machine. This pest adds a .purge extension and denies you access to your own data. It also provides you the highly questionable powerbase@tutanota.com email address. You’re supposed to use it and make the payment. However, you’d be making a deal with cyber criminals. To put it mildly, hackers aren’t famous for being honorable people. They do promise you a decryption key but usually deliver nothing. The virus adds a How to restore files.hta file which gives you more information about the payment. However, these tricks are all created solely to steal your money. Don’t believe this pest’s empty threats and empty promises. Take care of your machine instead. Get rid of the parasite. The sooner you uninstall this aggravating intruder, the better. To delete Purge Ransomware manually, please follow our comprehensive removal guide down below.
Purge Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Purge Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Purge encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Purge encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



