Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Promoz Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
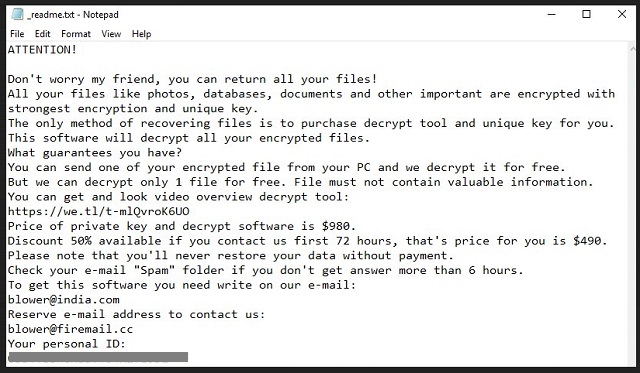
———————————————- ALL YOUR FILES ARE ENCRYPTED ———————————————–
Don’t worry, you can return all your files!
All your files documents, photos, databases and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees do we give to you?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information
Don’t try to use third-party decrypt tools because it will destroy your files.
Discount 50% available if you contact us first 72 hours.
—————————————————————————————————————————
To get this software you need write on our e-mail:
blower@firemail.cc
Reserve e-mail address to contact us:
blower@firemail.cc
Your personal ID:
[redacted 43 alphanumeric chars]
Promoz Ransomware is a destructive cryptovirus. It sneaks into your system through trickery, infects your entire system, and corrupts your files. The virus spread its roots around your entire system. It alters settings, drops malicious files, modifies the registry, and starts dangerous processes. This, of course, happens without any noticeable symptoms. You cannot catch the virus in time to limit its corruption. Without triggering any alarms, the ransomware gets your OS under control and starts its malicious operations. This invader targets the user-generated files. Pictures, video, documents, archives, databases. The ransomware encrypts your precious data with strong algorithms. You can see the icons of your files, but you cannot open, nor edit them. You can identify the corrupted files by the “.promoz” extension. Thus, if you have a file named “example.txt,” the ransomware will rename it to “example.txt.promoz.” The ransomware gets your data under lock and key and drops its ransom note. A text file named “_readme.txt ” explains the situation you are in, as well as lists the hackers’ demands. The threat actors ask for $490. They give you 72 hours to start the payment procedure. If you fail to do so, they threaten to double the asked sum. Do not swing into action! Take a moment to consider the situations. Paying the ransom is the worst you can do. These criminals promise decryption. Practice, however, shows that the hackers tend to ignore their victims once they get what they want. Furthermore, receiving questionable software from hackers may result in far worse consequences. Do not test your luck. Do what’s best for you and your system. Remove the ransomware ASAP!
How did I get infected with?
Torrents, spam messages, fake updates, malicious software bundles, corrupted links. There are myriads of virus distribution strategies. You can never know where Promoz might strike from. Its tricks are cunning and effective. They, however, are not flawless. These distribution methods rely on your carelessness. They succeed when you toss caution to the wind. Do not give into naivety. No anti-virus can protect you if you act recklessly. Only your actions are powerful enough to keep your device secure and infection-free. Even a little extra attention can spare you an avalanche of problems. Don’t visit shady websites. Download software from reliable sources only. Don’t skip installation steps. And, of course, be very careful with your inbox. Do not interact with unexpected messages. Treat them as potential threats. Always verify their senders. If, for example, you receive an unexpected email from an organization, go to their official website. Compare the email addresses listed there to the questionable one. If they don’t match, delete the pretender immediately. You can also enter the suspicious addresses into a search engine. If they were used for questionable business, someone might have complained.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.

Why is Promoz dangerous?
Promoz is a complete and utter menace. This virus sneaks into your device and wrecks everything. It locks your files and prevents you from accessing their content. Everything save also gets encrypted. The ransomware makes your device useless. Well, you can still browse the Web, but that’s limited. You cannot trust your compromised computer for sensitive operations such as online banking. Promoz lurks in the shadows and endangers your security. This nasty invader is a nightmare. There is still no third-party decryptors for this nasty ransomware. Paying the ransom, however, is not advisable. Sponsoring cybercriminals is never a good idea. These people promise a lot, but they don’t always deliver. There are cases when the victims paid just to get blackmailed for more. There are also instances when the victims received nonfunctional decryption tools. You cannot win a game against criminals. Don’t waste time in debates. Your best course of action is the immediate removal of the ransomware. Find where Promoz lurks and delete it upon detection! The sooner you clean your system, the better!
Promoz Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Promoz Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Promoz encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Promoz encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.