Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove MP3 file extension Ransomware?
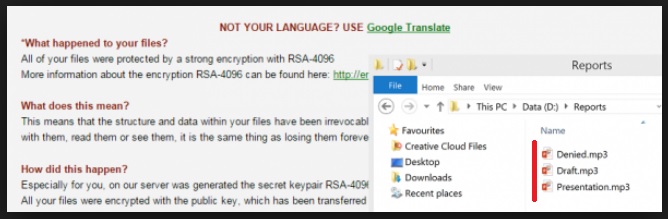
There’s a new ransomware, roaming the internet and infiltrating users’ computers. It’s associated with the MP3 file extension since its encryption process is complete with the addition of MP3 at the end of each one of your files. Once the pesky infection slithers into your PC, it quickly goes to work. Its programming kicks in, and it wastes no time to take control of your data. The ransomware encrypts every file you have stored on your system – pictures, videos, documents, music, etc. Nothing escapes its reach. You’ll find each file renamed with an added MP3 file extension and, thus, no longer accessible to you. For example, if you had a music video called ‘remix,’ you’ll come to find it as ‘remix.MP3,’ and you won’t be able to open it. After the infection is done with the encryption, it demands you pay a ransom for the decryption key, which will free your files. Whatever you do, do NOT comply! Regardless what the ransomware requires of you, don’t go through with it for it WILL end badly for you, and you WILL regret it. The best thing you can do is cut your losses by forsaking your data. They’re not worth you gambling for your privacy. One more thing you should know is that since the ransomware is currently such a plague on users, there have appeared a whole bunch of programs, which claim to overcome the MP3 encryption. Supposedly, these programs decrypt all of your files, and you don’t have to consent to the infection’s ransom demands. Don’t believe these lies! These are unsubstantiated claims, provided by wicked third parties, who only seek to exploit you further in your panic and weakness. Don’t fall for their treachery. It’s all a lie.
How did I get infected with?
Ransomware cannot enter your system unless you explicitly permit it. It’s required to ask for your approval before it installs itself, and if it fails to get it, it cannot get in. It’s as simple as that. So, with that in mind, how do you suppose it snuck in? Well, ransomware tools are notoriously resourceful when it comes to finding a way into your PC. They’re masters of deception, and MP3 is no exception. It dupes you into allowing it in while keeping you oblivious to it. How? Well, this is where the old but gold means of infiltration come into play. The pesky program usually slithers its way in by hiding behind freeware or spam email attachments, corrupted links or sites. Also, it can pretend to be a bogus system or program update, like Java or Adobe Flash Player. If you wish to keep the infection from succeeding and stop it from slithering into your PC, and making a mess, be more careful! It may not seem as much of advice, but attention is imperative! Such infections prey on carelessness, so don’t provide it! Don’t throw caution to the wind, and don’t give into gullibility and haste. Instead, be more vigilant. Even a little extra attention can save you an abundance of issues. Remember that.
Why is this dangerous?
The ransomware, currently plaguing your PC, is a new variant of the Teslacrypt 3.0, and it uses the .mp3 file extension to ‘kidnap’ your data. And, after it’s done with the encryption process, it lists its demands. Supposedly, if you comply, you’ll receive the decryption key and release your files from its captivity. But can you trust a hazardous infection to keep its end of the bargain? There are NO guarantees that, even if pay its ransom, the tool will provide you with the necessary key, which will decrypt your data. It can just as easily NOT give you one at all. Or, it can, but it can be one that doesn’t work. The scenarios just go from bad to worse, and each one ends with you, full of regret about ever deciding to place your faith into a ransomware infection. Still not convinced? Let’s try something. What would you say is the best case scenario? Let’s say it’s this: you go through with its requirements, receive a decryption key, apply it and it works, and you free your files. That sounds pretty good, right? But consider this. What’s stopping the infection from striking back again the very next day? Nothing. Its programming can kick back again, and you’ll find your files encrypted once more. And, you’re back to square one. Only this time, malicious strangers have access to your personal and financial details. Oh, yes. If you pay the ransom, you grant access to your private life to the wicked strangers behind the ransomware, residing on your PC. Do yourself a favor, and avoid all of that. Understand that this is a fight you simply cannot win. The stacks are against you from the start. So, do what’s best for you and your system, and make the wisest choice – say goodbye to your files. They’re replaceable. Your privacy is not.
MP3 file extension Removal Instructions
STEP 1: Start Your Computer into Safe Mode with Networking
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Restart the computer
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.

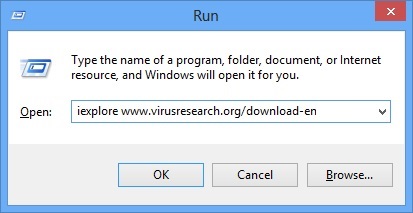
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type iexplore www.virusresearch.org/download-en
- Internet Explorer will open and a professional scanner will prompt to be downloaded
- Run the installer
- Follow the instruction and use the professional malware removal tool to detect the files of the virus.
- After performing a full scan you will be asked to register the software. You can do that or perform a manual removal.
Remove MP3 file extension malware Manually
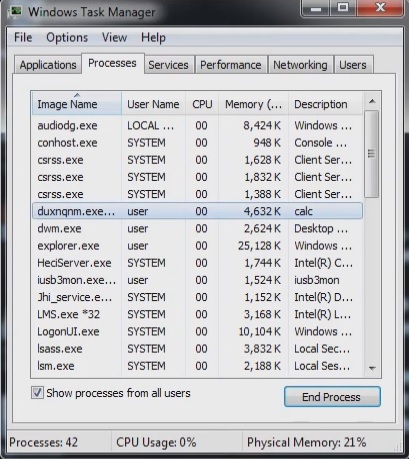
Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
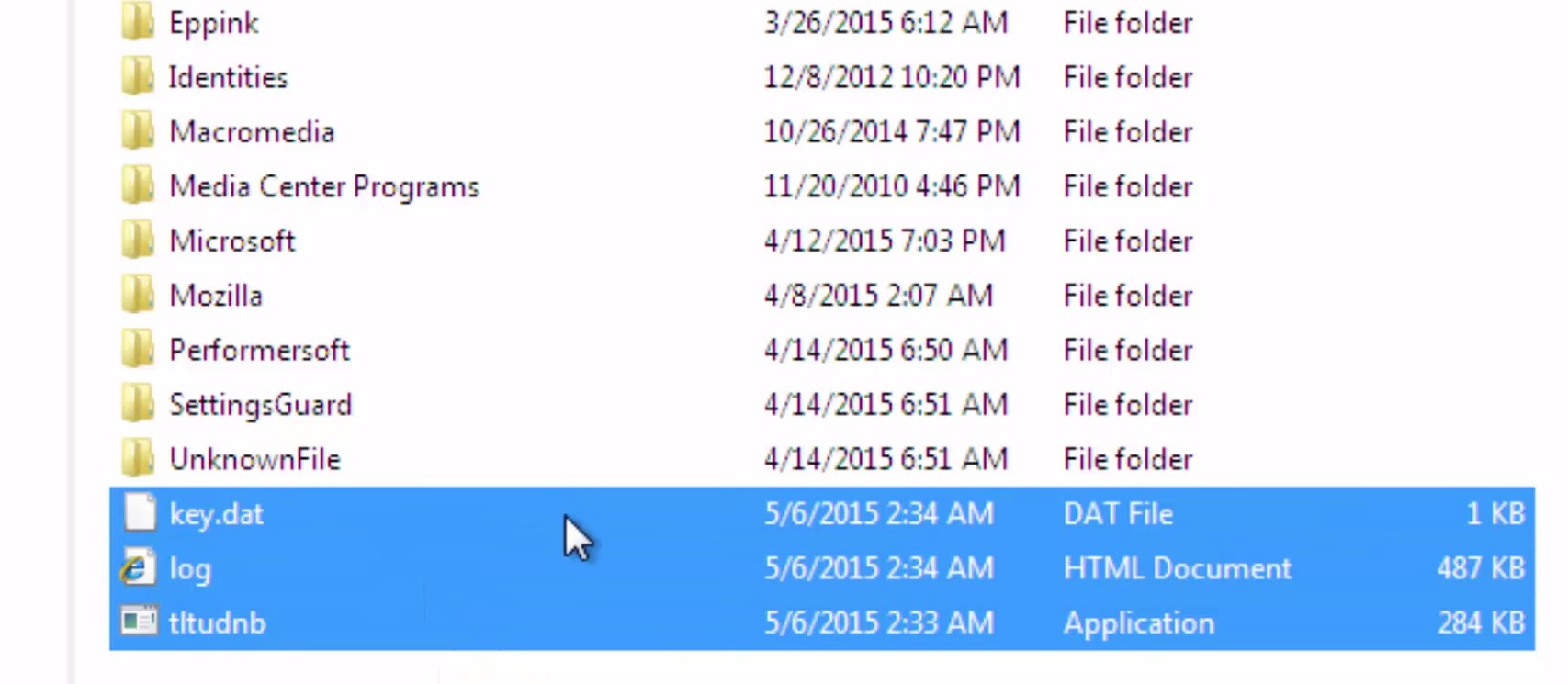
Locate the process of the Ransomware. Have in mind that this is usually a random generated file.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Before you kill the process, type the name on a text document for later reference.
Navigate to your %appdata%/roaming folder and delete the executable.
Open your Windows Registry Editor and navigate to
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\
and
HKLM\Software\Microsoft\Windows\CurrentVersion\Run\
delete the name crypto13
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you run the professional scanner to identify the files.
It is always a good idea to use a reputable anti-malware program after manual removal, to prevent this from happening again.