Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Monument Ransomware?
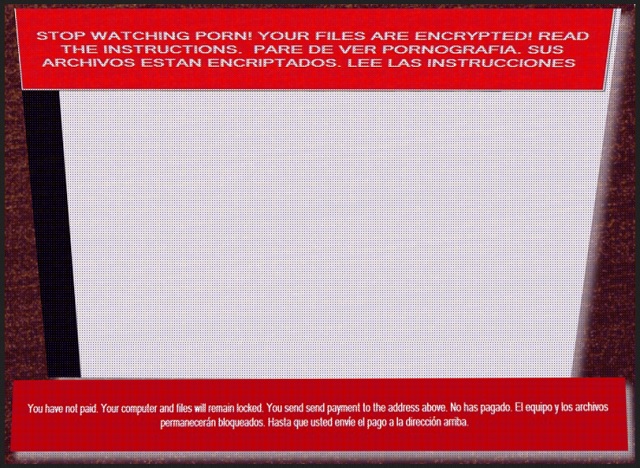
Readers recently started to report the following message being displayed when they boot their computer:
YOUR COMPUTER HAS BEEN HACKED
YOU MUST PRY .25 BITCOINS WITHIN 24 HOURS OR _35 AFTER 24 HOURS TO GET YOUR FLES BACK
AFTER 48 HOUR YOUR COMPUTER WILL BE DESTROYED IF YOU HAVE NOT PAID
HACKED
YOUR BITCOIN PAYMENT ADDRESS ADDRESS IS:
[RANDOM CHARACTERS]
IF YOU DO NOT HAVE BITCOINS BUY THEM AT WWW.LOCAL BITCOINS.COM
OR FIND A BITCOIN ATM NEAR YOU AT WWWW.COINATMRADAR.COM
View Encrypted Files
Send $200 USD (.15 BTC)within 24 hrs this Address:
[RANDOM CHARACTERS]
Click here to verify your payment and unlock your files!
The Monument infection is an updated version of the Jigsaw ransomware. You can also find it under the name DarkLocker. It tends to slither into your system under the guise of a fake update or via freeware. Then, once it’s in, puts you through hell. The tool encrypts every file you have on your computer. Pictures, documents, videos, music, all your data, falls victim to the ransomware. It locks your files and demands a ransom for their release. Ransomware programs tend to append a special extension at the end of each file you have. It further solidifies their grip over your data. You cannot open them, and moving or renaming them does nothing. In the case of Monument, that extension is a bit longer than you may imagine. Say, you have a picture called ‘pic.jpg.‘ It becomes ‘pic.jpg.To unlock your files send 0.15 Bitcoins to 1P87AphL2mETbyxLV18oJYXgsJxwLfgYiz within 24 hours 0.20 after 24 hours.’ It’s rather lengthy, but it gets the point across. After it’s done locking your data, the program leaves a TXT file. It’s the ransom note that contains instructions on what you’re expected to do. It’s written in English, Spanish, and Russian. And, it threatens that if you delay payment, there will be repercussions. The initial request is for 0.15 Bitcoin to get sent within 24 hours. After the deadline passes, the amount increases to 0.20 Bitcoins. What’s more, delays cost you not only money, but files, as well. The cyber kidnappers state they may get forced to delete 1-5 files every hour. And, if you don’t pay them in the first 48 hours after the ransomware strikes, you lose everything. The infection deletes all your locked data. Don’t fall for the scare tactics. Keep your cool, and do what’s in your best interest. It may seem harsh now, but the best thing you can do, is say goodbye to your data. They’re not worth the risks of compliance. Do NOT follow Monument’s instructions. There are many ways the infection can double-cross you. Don’t let it. Compliance runs the risk of strangers getting a hold of your private life. Lose your files instead of losing your privacy. It’s the better alternative. It’s not a pleasant one, but it’s the lesser of two evils.
How did I get infected with?
It’s rather unlikely that you installed the Monument tool yourself, right? You would remember doing such a thing, wouldn’t you? Well, not necessarily. You may not have memory of the exchange, but it did take place. The program sought your approval on its install. And, you gave it. If you hadn’t, you wouldn’t be in your current predicament. But how? How do you suppose you permit such a dangerous program to enter? Well, it duped you. You got duped. The application doesn’t just pop out, and seek access. If it did, you can deny it, and it can’t have that. So, instead of being straightforward, it’s sneaky. Trickery and deceit assist it in its covert infiltration. The most common methods of invasion include freeware and supposed updates. Fr example, you may believe you’re updating your Java, but you’re not. In actuality, you’re installing a hazardous ransomware. And, why is that? You’re not cautious enough to catch it in the act. So, it manages to slip by you, and wreak havoc. If that’s something, you’d rather avoid, choose caution over carelessness. One leads to infections, while the other helps to keep them out. Always read the terms and conditions when installing tools or updates. Don’t underestimate how far due diligence gets you. It can save you a ton of headaches and troubles. Distraction, naivety, and haste provide a one-way ticket to an infection-filled PC. Go the opposite route. Be thorough and vigilant. Even a little extra attention goes a long way.
Why is Monument dangerous?
Do NOT comply with the demands, Monument lays out! Compliance only buries you deeper into the abyss of troubles. Think about it. Let’s examine what happens if you choose to do what the tool asks of you. It seeks payment in Bitcoin. Say, you transfer that money. Then, what? You rest on the notion that cyber extortionists will keep their word. That they will follow through on their promises. Do you honestly believe you can trust them to keep their end of the bargain? Are you that naive? And, even if they do follow through, don’t rejoice just yet. Upon receiving payment, they’re expected to send you a decryption key. Then, you apply it, and free your files. But what if they send you one that doesn’t work? And, even if they give you the right one, then what? The decryption key removes the encryption. Not the infection. The Monument program remains on your system. And, what’s to stop it from striking again? It can lock your data at any time it chooses, and you’re back to square one. Only this time, you have less money. And, your private life is no longer private. That’s right. If you send the ransom money, you leave private information. Information, which the cyber kidnappers can then access. Do you think it’s wise to allow these criminals access to your personal and financial data? Once they get a hold of it, they can use it as they see fit. Don’t let your private details fall into the hands of extortionists. Do NOT pay. In the grand scheme of things, privacy is much more important than your files. Data is replaceable. Your private information is not.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Monument Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Monument Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Monument encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Monument encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



