Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Locky Files Virus?
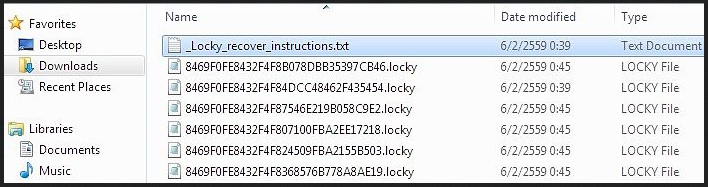
A vicious ransomware named Locky which demands payment through a Tor website – all Marvel fans should be quite impressed right now. Unfortunately, this wordplay is the first and last fun experience that the Locky virus has to offer. Ransomware has always been a synonym for trouble so you’re now stuck with a notoriously dangerous type of infection on board. Therefore, you have to take action as soon as possible. Locky is among the newest members of the ransomware family and it mainly follows the classic ransomware pattern. It invades your machine in silence and, using a complicated AES encrypting algorithm, locks your personal files. Once Locky has messed with your personal data, your data changes file format so it’s inaccessible. And practically useless. The virus performs a thorough scan on your machine searching for files with specific extensions. Then it encrypts them. You should know that this parasite goes after a rich variety of files such as pictures, music, videos, presentations, documents, etc. Furthermore, it encrypts unmapped network shares. That means a huge percentage of your personal and probably valuable information falls victim to Locky. How exactly does the virus lock your files? The same way CryptoWall (the most popular ransomware infection at the moment) does. It modifies the names of your files so the infected data now has a malicious .locky extension to it. Your computer can’t recognize this new random file format, the machine is unable to read it and, logically, you’re unable to use your very own personal data. Are you indignant already? It gets worse. Once the parasite has successfully locked out your access to the files stored on your PC, it starts generating a ransom note. Now, there are numerous problems with this message. First of all, the virus puts _Locky_recover_instructions.txt files on the desktop and in every single folder which contains an encrypted file. That means the stubborn ransom note is basically everywhere. However, Locky also replaces your wallpaper with the very same ransom instructions, just in case you haven’t noticed them yet. According to this incredibly aggravating warning message, regaining access to your files is only possible if you pay a certain (hefty) sum of money in bitcoins. On theory, you’re supposed to receive a decryption key in exchange for your money. On practice, though, you will probably receive nothing. Hackers don’t have a single reason whatsoever to play by the rules, including the rules they invented themselves. As you figured out already, ransomware-type infections get developed solely for monetizing purposes. Many PC users give into panic when their data all of a sudden gets encrypted. That means many people end up paying the ransom and getting scammed. It goes without saying that you should never allow crooks to blackmail you. This entire online fraud poses a serious, direct threat for your bank account. Instead of becoming a sponsor to cyber criminals, get rid of the parasite.
How did I get infected with?
This Locky files virus is hiding within a word document and is distributed via spam email-attachments or spam messages from unknown or known senders. The Locky virus has been detected in the following documents: invoice_S-10018692.doc, invoice_S-25977180.doc, invoice_J-89357653.doc, invoice_J-15289132.doc, invoice_J-66242861.doc, invoice_J-19161427.doc, invoice_J-79516505.doc, invoice_J-48151889.doc, invoice_J-06274026.doc, invoice_J-4018766.doc, invoice_S-27167647.doc, invoice_S-19297687.doc, invoice_J-50815479.doc, invoice_S-33312040.doc, invoice_S-67984094.doc, invoice_J-, 00833468.doc, invoice_S-28730695.doc, invoice_S-95922191.doc, invoice_J-03203373.doc, DOC201114-201114-001.doc
It have landed on your machine as a malicious Word document which you were careless enough to click open. Another plausible scenario is that the parasite was bundled with some freeware or shareware bundle. Remember, program bundling offers an extremely efficient, quick and stealthy distribution technique. It’s rightfully considered the most commonly used virus infiltration method at the moment so you should always keep that in mind. No potential threat online should be underestimated unless you’re deliberately trying to cause your machine damage. Are you? If not, make sure you avoid unverified websites and their illegitimate programs. Also, avoid the various third-party commercials you might come across while surfing the Web. It’s a lot easier to protect your PC from malware than it is to uninstall a virus later on.
Why is this dangerous?
Ransomware viruses are something you definitely do not want to have on board. The minute you realize you’re dealing with the nasty Locky parasite, you have to take measures. Otherwise, you’re exposing yourself to danger. Locky gets installed as an executable and begins to mess with your files almost immediately. This thing is very resourceful, very tricky and, unfortunately, very harmful. As previously mentioned, Locky locks out your access to your personal data by changing its format. Then the infection installs some malicious .exe files on board and starts convincing you that the only way to regain access to your information is by paying a ransom. The payment itself is supposed to happen through a Tor website named Locky Decrypter page. However, following these instructions guarantees you nothing. You could end up in a much more worrisome situation than your current one – with your machine still infected, your data still encrypted and a large sum of your money gone. Therefore, paying the ransom should be the absolute last thing you do. Unfortunately, once your files get encrypted by Locky, consider them lost. There is still no method to restore them without paying the ransom but you should always keep in mind that you keeping your end of the bargain doesn’t mean hackers would do the same thing. Don’t waste time and don’t let cyber criminals harass you. To delete the Locky virus manually, please follow the detailed removal guide that you will find down below.
Remove Locky files virus Manually
STEP 1: Kill the Malicious Process
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 3: Locate Virus Startup Location
STEP 4: Recover Locky Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with LOCKY encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate LOCKY encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

Delete the following registry keys as well:
HKCU\Software\Locky
HKCU\Software\Locky\id
HKCU\Software\Locky\pubkey
HKCU\Software\Locky\paytext
HKCU\Software\Locky\completed
HKCU\Control Panel\Desktop\Wallpaper
- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover LOCKY encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.
Please, have in mind that the names in your machine might be different as they might be generated randomly. It is always a good idea to use a reputable anti-malware program after manual removal to identify additional problems and to prevent this from happening again. Keep your software up-to date!




