Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Juicy Lemon Ransomware?
Despite having a name that sounds like a fruit commercial, Juicy Lemon Ransomware is actually a PC virus. A particularly virulent one, to be exact. This is a relatively new member of the ransomware family and it’s just as devastating, cunning and ruthless as all the other similar programs we’ve tackled so far. Juicy Lemon Ransomware will indeed leave you quite bitter. The virus first encrypts your personal data. Then, relying on your despair and panic, it demands € 1000 in Bitcoin. If you refuse to pay the ransom, Juicy Lemon Ransomware holds your files hostage so you won’t be able to use any of them. Pictures, music, Microsoft Office documents, videos – all your private information gets effectively encrypted. As you could imagine, you have no access to your own files, regardless of how important some of them may be. And that’s not even the worst part. Remember, you’re now stuck with one immensely troublesome malicious program. After it initially got installed, Juicy Lemon Ransomware performed a thorough scan on your device. This way the virus managed to locate your private data. Once the scan is complete, encryption begins. At this stage of the process you might notice that something is off with your machine. The PC speed gets significantly slower because Juicy Lemon Ransomware is using system resources. Now, if you spot the parasite’s activity on time, you could prevent further encryption (and damage) by shutting down the computer. Unfortunately, most people only notice Juicy Lemon Ransomware when it’s too late. How does the encrypting process work? The parasite messes with the file format of your data. It copies your files and deletes the originals. What you’re left with are the modified copies which, of course, are unreadable. Juicy Lemon Ransomware adds .id-[victim’s ID]_email1_support_@_juicylemon.biz_email2_provectus_@_protenmail.com_BitMessage_BM-NBRCUPTenKgYbLVCAfeVUHVsHFK6Ue2F at the end of its malicious copies of your data. As you can see, the virus includes an ID in the file appendix – this is the identification number of your computer. Furthermore, Juicy Lemon Ransomware uses a highly complicated encrypting algorithm in order to lock your data. Due to its trickery, your files are completely inaccessible and practically unusable. While infecting your data, Juicy Lemon Ransomware also dropped RESTORE FILES.txt and [victims-ID].txt files in all the folders that contain encrypted information. Obviously, that makes quite a lot of folders. According to this message, you have to pay a hefty sum of money in order to free your files. To learn why paying the ransom would be the absolute worst idea possible, keep on reading.
How did I get infected with?
Chances are, you opened some malicious email which contained the virus. Even though spam messages from unknown senders and spam email-attachments are the oldest tricks in the book, those two are effective beyond belief. Therefore, hackers don’t seem to be giving them up anytime soon. Other popular infiltration techniques are fake job applications, corrupted torrents, unsafe websites and suspicious-looking freeware bundles. Next time you come across something untrustworthy online, simply avoid it. Keep in mind what incredibly stealthy methods cyber criminals use and don’t neglect your safety for even a minute. A minute is probably all it took Juicy Lemon Ransomware to invade your machine. Also, a rule of thumb for the future – keep backups of all your most valuable files. This way, even if your PC falls victim to malware once again, you won’t lose any personal information.
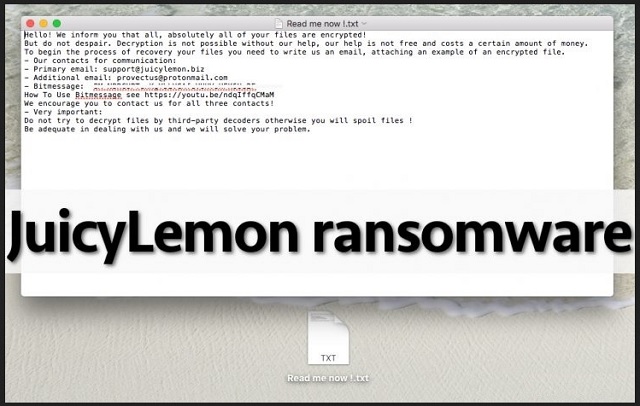
Why is Juicy Lemon dangerous?
The ransom message informs you that hackers are willing to offer some help. How incredibly kind of them to help you restore the files they encrypted in the first place! As you could imagine, crooks’ malicious “help” is the last thing you need right now. Ransomware is solely money-oriented so if you follow hackers’ instructions, you’ll get involved in their cyber fraud. Are you willing to be scammed? No? They don’t even think about contacting hackers. Juicy Lemon Ransomware provides you two email addresses – support(@)juicylemon.biz and provectus(@)protonmail.com. Stay away from both. Making a deal with greedy and sly cyber criminals will not help you restore you data, despite the fact you’re promised a decryption key in exchange for your money. Hackers don’t have a single reason whatsoever to follow the rules so don’t pay anything. Get rid of the intruder instead. To delete it manually, please follow the detailed removal guide you’ll find down below.
Juicy Lemon Removal Instructions
STEP 1: Kill the Malicious Process
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 3: Locate Startup Location
STEP 4: Recover Juicy Lemon Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Juicy Lemon encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Juicy Lemon encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



