Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Help_recover_instructions+vgv Ransomware?
Ransomware is not something you ever want to cross the threshold of your system. And, if it does, you’re in for a horrendous experience. Why? Well, ransomware is aimed at your data. It’s programmed to attack your data and targets every single file you have stored on your PC. The infection takes your files hostages and demands you pay ransom if you ever wish to see them again. Make no mistake. Your files haven’t moved from where you left them. You can see them, but you can’t access them. That’s because the ransomware encrypts them. And, nothing is safe from its reach – pictures, videos, music, documents, etc., everything falls under its control. The infection also prevents you from accessing your Control Panel or opening your browser and going online. With no internet access, it completely cuts you off. By backing you into a corner, it hopes it will force you to comply with its demands. And, ultimately, what the tool wants is money. The ransom usually requires some form of monetary payment. And, after the encryption is complete, and your data is the ransomware’s ‘captive,’ it makes sure to show you what it desires. When that moment comes, Help_recover_instructions appears. It’s a text file, which holds the infection’s ransom requirements. Whatever they are, do NOT comply! If you do, your situation will only worsen! There’s no way to stress this enough: Your predicament will NOT improve! Don’t dig yourself deeper into the hole. Cut your losses, and say goodbye to your files. It may seem harsh, but it’s truly the best thing you can do in a situation as dreadful as this one. Ransomware infections are an opponent you simply cannot defeat. The game is rigged against you from the start. We repeat: cut your losses! Files can be replaced, but the safety of your personal and financial details? No.
How did I get infected with?
Ransomware doesn’t just magically appear on your computer. Like most cyber infections, its installation has to be approved before it enters your system. That means that, at some point, the current plague of your PC, asked for your permission, and you granted it. You must have. Otherwise, you wouldn’t be in this situation. It’s more than likely that you don’t remember the exact moment when you consented to its installment. Do you know why that is? Such infections tend to slither in undetected. They may be required to ask for permission, but they don’t do so openly. They do it quite sneakily, usually with the help of the old but gold means of invasion. That includes hiding behind spam email attachments, freeware, corrupted websites, or links. Also, they can pretend to be a fake system or program update. For example, you may be convinced you’re updating your Adobe Flash P|layer or Java, but you’ll be installing a dangerous infection instead. Here’s where vigilance and due diligence are crucial as they help keep such nasty, harmful tools away! Don’t give into naivety, haste, and distraction! Cyber infections, like the one currently messing with you and your system, prey on carelessness. So, instead of throwing caution to the wind, be extra attentive! Even a little extra caution goes a long way.
Why is Help_recover_instructions+vgv dangerous?
If you spot the Help_recover_instructions text file, you’re in for a hard decision. To forsake your files and protect yourself from the reach of wicked individuals, or rely on hope and decency? We’ll explain. Well, after the ransomware sneaks into your system and proceeds with its agenda – to corrupt it, soon after you’ll be faced with a choice. Once the infection completes the encryption process and takes all of your data hostage, it displays the Help_recover_instructions text file, which contains its ransom demands. And, here’s where you have to decide whether to comply with them or not. Experts advise you do the latter. And, here’s why. Don’t forget that you’re dealing with malicious strangers, who seek to exploit you to make a profit. To think that they will be decent enough to return the ownership of your files once you pay is naive, to say the least. Even if you pay, and they do grant you with a decryption key, there are no guarantees, it will work. It may be fake. Or, even if it works, your joy will be brief. Why? Well, think about it. What’s stopping the ransomware from kicking back in the very next day? Nothing. It can easily encrypt everything again, and you’ll be back to square one. Only, apart from losing money and your files, you’ll have also taken a colossal security risk. By paying the ransom, you grant unknown third parties with access to your personal and financial information. Do you consider that wise? Hardly. Either way, you look at it, you lose. So, why play the game at all? Act in your best interest, and say goodbye to your files. It’s the best and worst scenario at the same time. But it all simmers down to the following question “Which loss can you live with: losing your data or exposing your private life to strangers?” Figure out your priorities and act.
Help_recover_instructions+vgv Removal Instructions
STEP 1: Start Your Computer into Safe Mode with Networking
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Restart the computer
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.

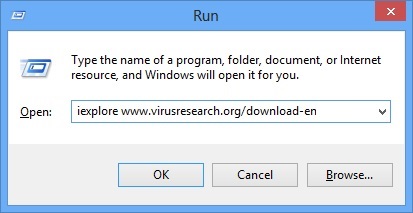
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type iexplore www.virusresearch.org/download-en
- Internet Explorer will open and a professional scanner will prompt to be downloaded
- Run the installer
- Follow the instruction and use the professional malware removal tool to detect the files of the virus.
- After performing a full scan you will be asked to register the software. You can do that or perform a manual removal.
Remove Help_recover_instructions+vgv Manually
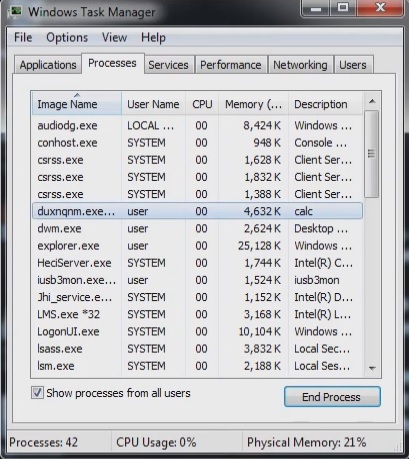
Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
Locate the process of teslacrypt. Have in mind that this is usually a random generated file.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Before you kill the process, type the name on a text document for later reference.
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you run the professional scanner to identify the files.
It is always a good idea to use a reputable anti-malware program after manual removal, to prevent this from happening again.