Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove ETC file extension Ransomware?
Ransomware is one of the worst cyber infection, roaming the internet. And, unfortunately, if you find your files renamed with the added ETC file extension at the end, you’re dealing with ransomware. And, you’re in trouble. The ETC file extension is linked to a pretty nasty infection, which encrypts all of the data you have stored on your PC, and then demands you to pay ransom if you wish to get it back. But, here’s a little secret that’s not so secret: even if you pay, odd are, you won’t regain control of your files. That’s probably not what you wanted to hear, but it’s the truth. The fight against the infection is one you can’t win as it’s stacked against you. It’s rigged right from the start. Think about it. Ransomware invades your system. It encrypts your data by adding the .etc file extension, so you can’t access your files anymore. Then it requires you to pay a ransom, which will, supposedly, win you a decryption key, which will, presumably, decrypt your date. First of all, there are too many ‘ifs’ and ‘buts.’ That should be your first red flag. And, secondly, you have NO guarantees that everything will work out in the end. Consider this. You pay the ransom, but receive a decryption key that doesn’t work, and your files are still inaccessible. Or, you don’t receive a key at all. And, what then? You’ve paid good money for something you failed to receive, or received and doesn’t work. And, not only will your data still be decrypted, but wicked strangers will have access to your private life. Oh, yes. By paying the ransom, you let the unknown individuals behind the ransomware infection into your personal and financial details. Do you expect that to end well for you? Hardly. Do yourself a favor and do the smart thing, even if it’s difficult and unpleasant – forsake your files. They’re not worth placing your privacy in jeopardy.
How did I get infected with?
Ransomware tools, like the one encrypting your files with the ETC file extension, are notoriously sneaky. They use slyness and subtlety to slither into your system. And, even though, they’re bound to gain your permission to enter, they still sneak in undetected. Surprising, isn’t it? How do you suppose they manage that? Well, it’s pretty straightforward. The applications are masterful in the arts of deception. Through trickery and finesse, they make their way to your computer. More often than not, using the old but gold methods of invasion. That includes hitching a ride with spam email attachments, corrupted sites or links, or freeware. Also, they can pose as fake updates. For example, while you’re convinced you’re updating your Java or Adobe Flash Player, in actuality, you’re installing ransomware.And, before you know it, all of your files are renamed with an added .etc extension. To keep that from happening, try to be more careful. Don’t give into carelessness for such infections prey on it. Don’t rush and don’t be naive. Always do your due diligence, and remember that even a little extra attention today can save you a ton of troubles tomorrow.
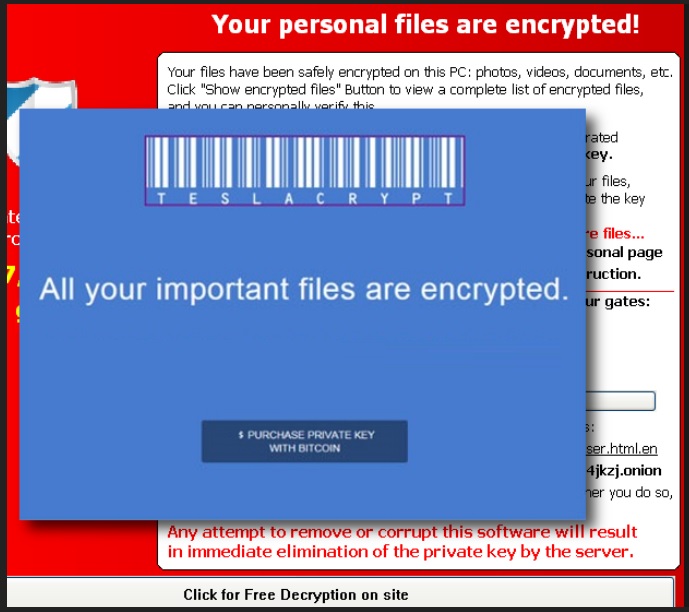
Why is this dangerous?
Once the ransomware slithers into your system, it wastes no time. Immediately after infiltration, it gets to work and encrypts all of the data you have on your PC. When it’s done, each and every file will have an added ETC extension at the end. For example, if you have a picture called ‘summer,’ you’ll find it as ‘summer.etc.’ And, after that nasty addition, you won’t be able to open it. The extension makes your files inaccessible. Even if you rename them, the encryption will hold. The only way to get rid of it, and reclaim your data is to apply the decryption key. Unfortunately, to get it, you have to comply with the infection’s ransom demands. As was already explained, that’s ill-advised. There are several ways the exchange can go down, and they all end badly for you. Why not spare yourself the regret, which you’ll undoubtedly feel if you choose to go down this path and go through with ransom? Protect your privacy! Don’t jeopardize your personal and financial details by paying! Yes, if you pay, you MAY get back your files. But for how long? And, will you at all? It’s not worth taking such a colossal risk for such minuscule prospects of success! Don’t gamble with your private life! Choose privacy over data. After all, pictures, music, etc., can be replaced. But what will happen if strangers with malicious intentions get a hold of your private information? Don’t wait around to find out!
ETC file extension Removal Instructions
STEP 1: Start Your Computer into Safe Mode with Networking
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Restart the computer
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.

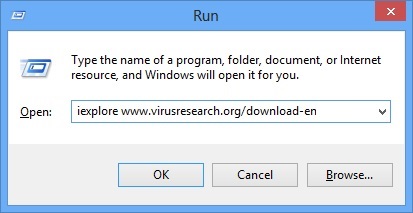
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type iexplore www.virusresearch.org/download-en
- Internet Explorer will open and a professional scanner will prompt to be downloaded
- Run the installer
- Follow the instruction and use the professional malware removal tool to detect the files of the virus.
- After performing a full scan you will be asked to register the software. You can do that or perform a manual removal.
Remove ETC file extension malware Manually
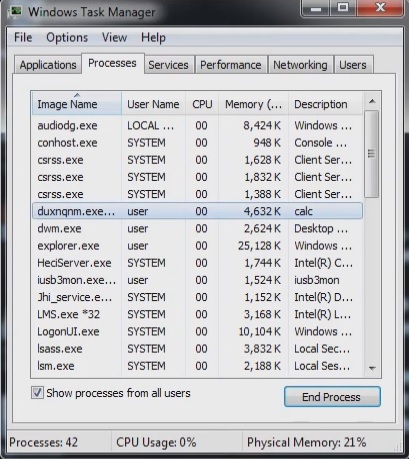
Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
Locate the process of the Ransomware. Have in mind that this is usually a random generated file.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Before you kill the process, type the name on a text document for later reference.
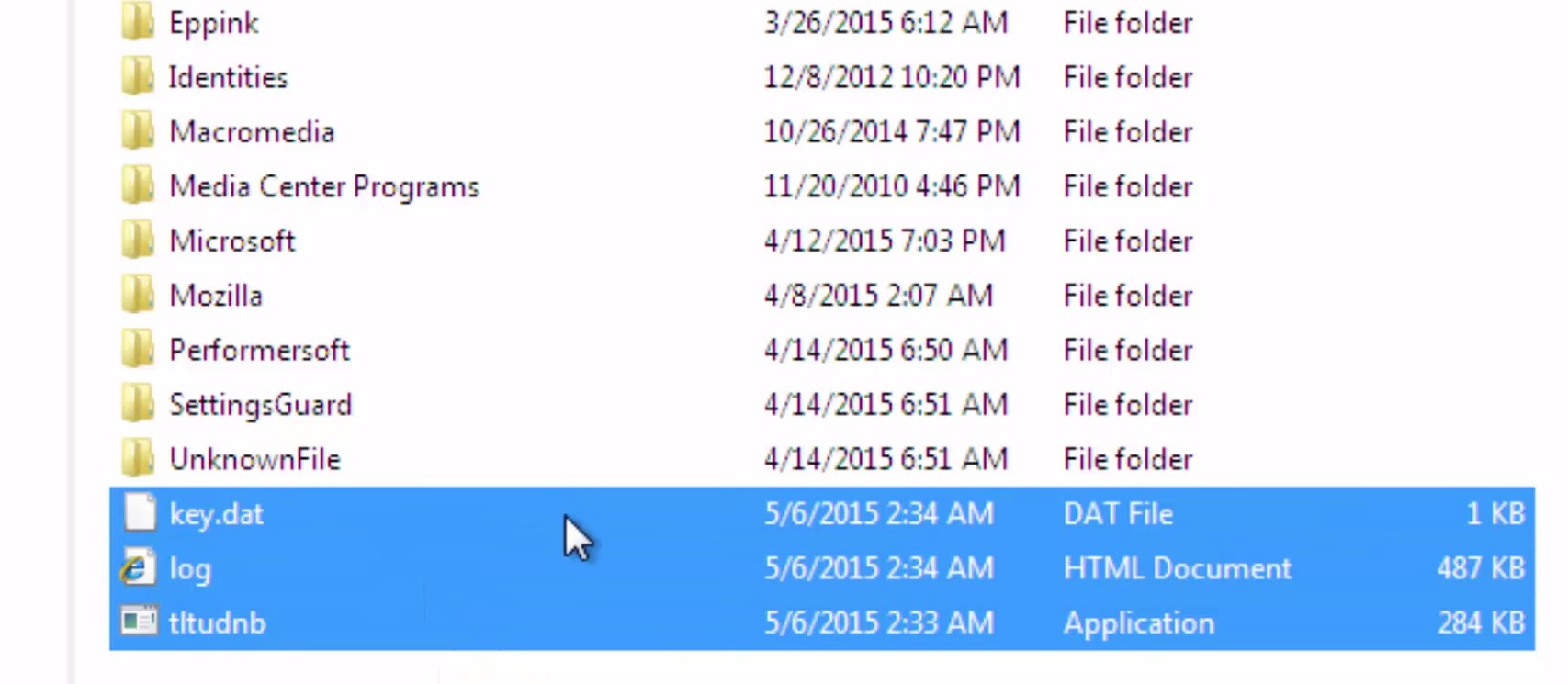
Navigate to your %appdata%/roaming folder and delete the executable.
Open your Windows Registry Editor and navigate to
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\
and
HKLM\Software\Microsoft\Windows\CurrentVersion\Run\
delete the name crypto13
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you run the professional scanner to identify the files.
It is always a good idea to use a reputable anti-malware program after manual removal, to prevent this from happening again.