Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove DMA Locker Ransomware?
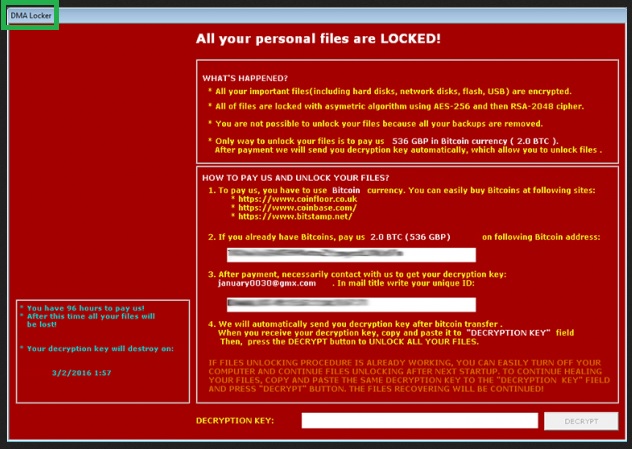
DMA Locker is a relatively new member of the ransomware family. And this is a family you certainly don’t want to have anything to do with. Here you will find answers to some of the most frequently asked questions about this pest; you can also read our comprehensive removal instructions below. You’re now stuck with a particularly aggressive, destructive and nasty type of PC virus. You’re in trouble. Therefore, you have to take action. DMA Locker works the same way all ransomware parasites do – it encrypts personal data. That means it effectively locks music, pictures, videos, documents, anything of value you may have stored on your machine. DMA Locker infects your files using a complicated asymmetric algorithm so it makes your private information absolutely inaccessible. After it invaded your machine, the parasite immediately dropped some .exe files and scanned your computer searching for personal data to encrypt. The PC cannot read your files after they have been modified and all of your valuable data is now practically useless. Once DMA Locker has effectively demolished your cyber experience, it starts generating a huge red pop-up message which has two versions – one in Polish and one English. According to this ransom note, the only way to regain access to your infected files is by paying a certain sum of money in bitcoins. And it’s quite a hefty one. It goes without saying that paying the ransom doesn’t guarantee you anything because, to put it mildly, hackers aren’t known for keeping their word. The DMA Locker virus doesn’t have a detached decryption feature like most similar programs do. This time the decryptor comes biult-in but it’s safe to say apart from that, DMA Locker follows the classic ransomware pattern. The only reason why this pest was developed in the first place was to scam gullible PC users. Therefore, paying the ransom should be the very last thing you do. Crooks are supposed to provide you some highly questionable decryption key in exchange for your money. Obviously, cyber criminals don’t have a single reason to follow the rules, including the rules they invented. DMA Locker is nothing but the nth opportunity for frauds to lie to your face and, ultimately gain dubious revenue at your expense. Even if you do pay the ransom, you won’t regain access to your infected files as they will remain encrypted. You don’t really want to become a sponsor of nasty cyber criminals, do you? Then get rid of the parasite before it successfully damaged your bank account.
How did I get infected with?
Ransomare in general and this nuisance in particular travel the Web the exact same way all virtual parasites do – via stealth and deceit. As you can imagine, no one in their right mind would install such a malicious program voluntarily. That means if DMA Locker is now on your PC system, you clicked something that you should have ignored. Some of the most popular infiltration techniques online are spam messages, spam email-attachment and corrupted third-party commercials. Make sure you avoid them in the future. Clicking a compromised web link could automatically install all kinds of malware. You should also stay away from unverified websites, especially when you’re downloading software. Keep in mind that bundled freeware/shareware is one of the most commonly used distribution methods online. Therefore, it’s definitely worth it to check out the programs you install in advance. Go though the Terms and Conditions, go through the EULA (End User License Agreement) and don’t skip installation steps. Remember that rushing would cost you lots of time, energy and nerves if you accidentally stumble across some virtual pest. Avoid illegitimate pages and always pay attention to the programs you give green light to. Keep in mind that you could never be too cautious when surfing the Web.
Why is DMA Locker dangerous?
The DMA Locker parasite, as mentioned already, is extremely virulent. This thing travels the Web in complete silence and once it gets installed, begins to wreak havoc. Thanks to the thorough scan the virus performs, it quickly finds all of your private information. Of course, this might include some particularly important files or some very sensitive private data. How aggravated are you knowing that your own files are being held hostage? Ransomware offers hackers a convenient way to make money online and that’s why they lock out your access to your own information. Crooks are trying to get you to panic. It goes without saying that panicking will not recover your data. On the other hand, panicking might cost you money. Don’t contact hackers, don’t pay the ransom they demand, don’t believe anything the pop-up message claims and, most importantly, don’t allow crooks to scam you. The sooner you uninstall the nasty DMA Locker virus, the better so why hesitate? In order to get rid of this malicious parasite manually, please follow the detailed instruction that you will find down below.
DMA Locker Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Start Your Computer into Safe Mode with Networking
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Restart the computer
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.

- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
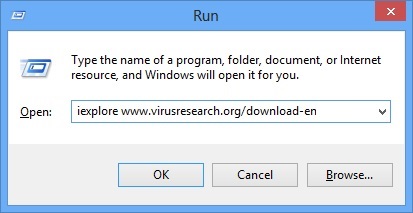
- A dialog box should open. Type iexplore www.virusresearch.org/download-en
- Internet Explorer will open and a professional scanner will prompt to be downloaded
- Run the installer
- Follow the instruction and use the professional malware removal tool to detect the files of the virus.
- After performing a full scan you will be asked to register the software. You can do that or perform a manual removal.
Remove DMA Locker Manually
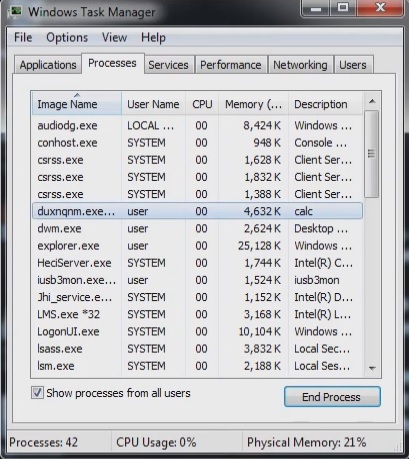
Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
Locate the process of teslacrypt. Have in mind that this is usually a random generated file.
Before you kill the process, type the name on a text document for later reference.
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you run the professional scanner to identify the files.
It is always a good idea to use a reputable anti-malware program after manual removal, to prevent this from happening again.