Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove CryptXXX Ransomware?
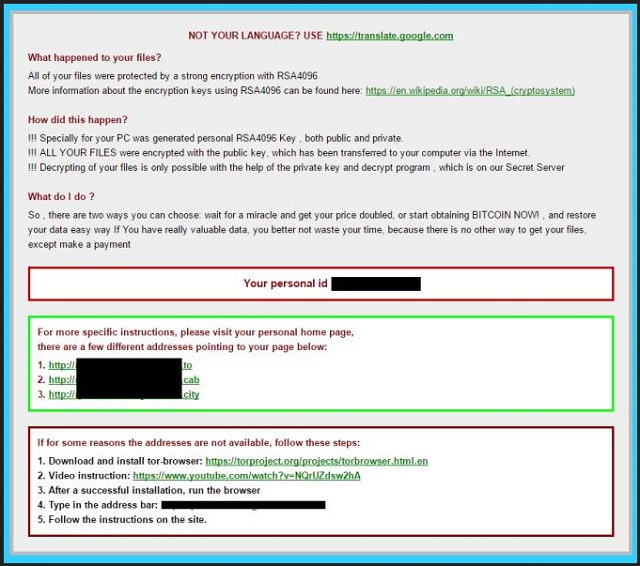
Reader recently start to report the following message being displayed when they boot their computer:
NOT YOUR LANGUAGE? USE https://translate.google.com
What happened to your files ?
All of your files were protected by a strong encryption with RSA4096
More information about the encryption keys using RSA4096 can be found here: http://en.wikipedia.org/wiki/RSA_(cryptosystem)
How did this happen ?
!!! Specially for your PC was generated personal RSA4096 Key , both public and private.
!!! ALL YOUR FILES were encrypted with the public key, which has been transferred to your computer via the Internet.
!!! Decrypting of your files is only possible with the help of the private key and decrypt program , which is on our Secret Server
What do I do ?
So , there are two ways you can choose: wait for a miracle and get your price doubled, or start obtaining BITCOIN NOW! , and restore your data easy way
If You have really valuable data, you better not waste your time, because there is no other way to get your files, except make a payment
For more specific instructions, please visit your personal home page, there are a few different addresses pointing to your page below:
Your personal id [removed]
If for some reasons the addresses are not available, follow these steps:
1 – Download and install tor-browser: http://www.torproject.org/projects/torbrowser.html.en
2 – After a successful installation, run the browser
3 – Type in the address bar: [removed]
4 – Follow the instructions on the site
CryptXXX Ransomware was discovered in April 2016. In less than three months this pest managed to gain popularity for all the wrong reasons. The parasite impersonates some of the most dreaded ransomware infections – CryptoWall and TeslaCrypt. That makes CryptXXX Ransomware a program you most certainly do not want to cross paths with. However, as you’re reading removal guides, it’s safe to assume you already came across the virus. Furthermore, you got infected with it. You should know you’ve fallen victim to a particularly deceptive, devastating and aggressive parasite. Ransomware-type viruses are on the rise right now because they bring easy profit to their developers. The problem is, hackers’ illegitimate revenue comes solely at your expense. Be very careful with ransomware parasites and don’t let crooks scam you. Now, how does the scheme work? Once CryptXXX Ransomware gets installed, it initiates a thorough scan on your PC. This way the parasite locates all your personal files so it could encrypt them. If you notice the computer is somewhat sluggish, that might be a sign of a vicious ransomware-type program. Immediately shut down the machine; this will stop the encrypting process and prevent further damage. However, people usually encounter CryptXXX Ransomware’s presence when it’s too late. The virus adds a malicious .crypt extension to all your personal files; this way the target data changes format. As you could imagine, your PC will not be able to recognize the new file format so it won’t read your files. Therefore, CryptXXX Ransomware leaves all your private files locked, inaccessible and practically useless. It goes without saying there might be some immensely important files among the infected ones which are unreadable as well. Do you see why ransomware is considered to be the most virulent infection online? The virus holds your data hostage. Then, just to make your situation even worse, CryptXXX Ransomware demands a ransom. While encrypting your data, this program drops !Recovery_[victim_id].html and !Recovery_[victim_id].txt files. You will find these files in all folders that contain encrypted information because they provide you detailed payment instructions. According to the ransom messages, you have to pay 2.4 Bitcoin (which is almost 1400 USD) if you want to free your files. Is your data really worth 1400 USD, though? Our advise is to ignore hackers’ aggravating ransom notes. Don’t give into your despair and panic because this might cost you a hefty sum of money.
How did I get infected with?
Ransomware mainly gets spread online via malicious email-attachments or messages from unknown senders. Therefore, next time you see some suspicious email in your inbox, delete it on the spot. Other popular infiltration methods are corrupted torrents, unsafe freeware or shareware bundles, illegitimate websites and potentially dangerous third-party pop-ups. The parasite might have also landed on board with the help of Trojan horse. You see, hackers could be impressively creative when it comes to malware so don’t neglect your safety. Always keep an eye out for threats and remain cautious online. In addition, CryptXXX Ransomware is known to get downloaded via Exploit Kits as well.
Why is CryptXXX dangerous?
The CryptXXX Ransomware virus takes down a rich variety of file formats – anything from music and pictures to MS Office documents and presentations. The parasite encrypts .mp3, .mp4, .rar, .png, .txt, .map, .pdf, .jpeg, .jpg, .ppt, .crw, .xls, .doc, .docx and many more files. As you could imagine, some PC users would give into anxiety when they see the sudden, unauthorized modifications CryptXXX Ransomware has made. That is exactly what hackers rely on. This parasite uses the RSA4096 asymmetric encrypting algorithm which means the data it encrypts is effectively locked. In order to free your files, you have to use a decryption key. However, this decryption key doesn’t come for free. Ransomware offers cyber criminals an extremely easy way to blackmail gullible people; don’t become one of the victims. No matter how intimidating CryptXXX Ransomware’s ransom notes are, paying the money would be a mistake and you know it. Hackers don’t have the slightest reason to play by the rules so there’s no guarantee you’ll regain access to your encrypted files. The ransom message states that you could either “wait for a miracle and get your price doubled, or start obtaining BITCOIN NOW”. What hackers don’t tell you is that there is a third option – delete CryptXXX Ransomware and use a decryption tool in order to free your locked files. To get rid of this parasite manually, please follow the comprehensive removal guide you’ll find down below.
CryptXXX Removal Instructions
STEP 1: Kill the Malicious Process
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 3: Locate Startup Location
STEP 4: Recover CryptXXX Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with CryptXXX encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate CryptXXX encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



