Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.

If you are seeing “Your important files strong encryption” message – don’t panic!
If all of your computer data has been encrypted and all you find is a message from CryptoTorLocker2015 demanding ransom for their decryption, you’re dealing with a ransomware program. CryptoTorLocker2015 is a brand new ransomware tool, which belongs to the Encryptor Category and has its own wallpaper, theme, ransom messages, and so on. Not only is it a highly dangerous and harmful application, but it’s also extremely unreliable. Even if you do pay the ransom it asked for, you can still end up with your files encrypted, and your computer locked. That’s why it’s recommended to not give into CryptoTorLocker2015’s requests. One of the reasons why paying is a horrible idea is that by doing so, you’ll give the people behind the ransomware more information on you, which they can later use for their own malicious purposes. So, aside from giving them money, you’ll also provide them with your personal and financial data. If you pay, they will know not only your IP address, but also your name, bank account or credit card details. Think long and hard whether there is something on your computer that’s worth you gambling with your privacy?
CryptoTorLocker2015 can infect your system by hiding behind corrupted links, corrupted websites, or spam email attachments. However, more often than not, it turns to using freeware as a means of invasion. That’s because it provides possibly the easiest way in. For some reason, most users believe that if they skip reading the terms and conditions and agree to everything in haste, there will be no repercussions. Unfortunately, they find out the hard way just how wrong they are. You should always be careful when dealing with freeware as it’s often bundled with all sorts of dangerous malware. If you wish to avoid dealing with CryptoTorLocker2015, remember that a little extra attention can go a long, long way. here is what this ransomware will display once it infects you.
Your important files strong encryption RSA-2048 produces on this computer:Photos,Videos,documents,usb disks etc.Here is a complete list of encrypted files,and you can personally verify this.CryptoTorLocker2015! which is allow to decrypt and return control to all your encrypted files.To get the key to decrypt files you have to pay 0.5 Bitcoin 100$ USD/EUR. Just after payment specify the Bitcoin Address.Our robot will check the Bitcoin ID and when the transaction will be completed, you’ll receive activation,Purchasing Bitcoins,Here our Recommendations 1. Localbitcoins.com This is fantastic service,Coinbase.com Exchange,CoinJar =Based in Australia,We Wait In Our Wallet Your Transaction WE GIVE YOU DETAILS! Contact ME if you need help My Email = information@jupimail.com AFTER YOU MAKE PAYMENT BITCOIN YOUR COMPUTER AUTOMATIC DECRYPT PROCEDURE START! YOU MUST PAY Send 0.5 BTC To Bitcoin Address: 1KpP1YGGxPHKTLgET82JBngcsBuifp3noW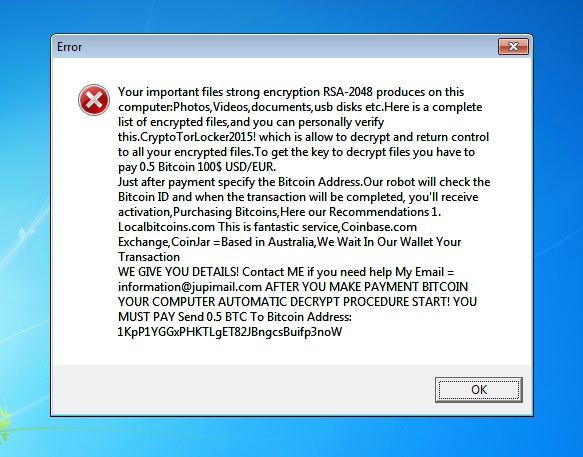
After sneaking in your system undetected, CryptoTorLocker2015 proceeds to lock your computer and encrypt everything you have stored on it – photos, documents, music, videos, everything. It makes it impossible for you to use your computer (and, naturally, your files), and sometimes it even blocks your internet access, as well. Then it proceeds to show you a message containing its demands. Since the ransomware application tracks your location with the help of your IP address, the message is usually in your native language. It claims that you were caught in illegal activities and because of that you’re subject to pay a fine. Since the message is usually authentic-looking, most users fall for it and pay up, so they don’t go to jail. CryptoTorLocker2015 typically asks for a payment of 100 USD or 100 EUR for the decryption key with which you can save your files, and avoid prison. The program even provides you with several payment methods to make it easier for you to pay. In order to avoid getting extorted into paying money to the wicked unknown people behind the ransomware tool, make sure you create backups for all of your important files. That way, you won’t risk paying the ransom, and still be left with encrypted data and no decryption key. Don’t pay CryptoTorLocker2015’s ransom, because, in the end, it’s not worth the risk.
Cryptolocker 2015 Removal Instructions
STEP 1: Start Your Computer into Safe Mode with Networking
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Restart the computer
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.

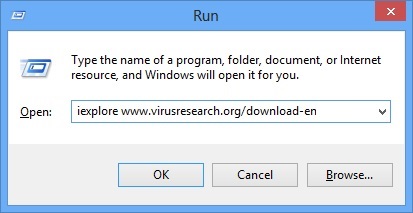
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type iexplore www.virusresearch.org/download-en
- Internet Explorer will open and a professional scanner will prompt to be downloaded
- Run the installer
- Follow the instruction and use the professional malware removal tool to detect the files of the virus.
- After performing a full scan you will be asked to register the software. You can do that or perform a manual removal.
Remove Cryptolocker 2015 Manually
You need to delete the following files and registry keys. These were in our case:
C:\Users\user\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup:HOW TO DECRYPT FILES.txt
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
You will also need to recreate the broken shortcuts in your desktop manually.
the Trojan locks the computer and displays a fraudulent message on the screen informing the user that they are in breach of copyright law. You need to locate the picture and delete it.
You can alternatively use your msconfig to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you run the professional scanner to identify the files. A few tools were developed to decrypt the encrypted files, but there is NO guarantee they will work.
It is always a good idea to use a reputable anti-malware program after manual removal, to prevent this from happening again.