Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Cerber2 Ransomware?
Reader recently start to report the following message being displayed when they boot their computer:
What happened to your files?
All of your files were protected by a strong encryption with RSA-2048 using CryptoWall. More information about the encryption keys using RSA-2048 can be found here: en.wikipedia.org/wiki/RSA_(crypto system)
What does this mean?
This means that the structure and data within your files have been irrevocably changed, you will not be able to work with them, read them or see them, it is the same thing as losing them forever, but with our help, you can restore them.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How did this happen?
Especially for you, on our server was generated the secret key pair RSA-2048 – public and private. All your files were encrypted with the public key, which has been transferred to your computer via the Internet. Decrypting of your files is only possible with the help of the private key and decrypt program, which is on our secret server.
What do I do?
Alas, if you do not take the necessary measures for the specified time then the conditions for obtaining the private key will be changed. If you really value your data, then we suggest you do not waste valuable time searching for the solutions because they do not exist.
Are your files modified? Do they have some bizarre .Cerber2 extension added to them? Then you’re dealing with ransomware. Unfortunately, this is the most devastating and virulent thing currently on the Web. And it’s wreaking havoc on your computer system. You see, there’s a reason why these programs are so immensely dreaded. Numerous reasons, actually. Ransomware gets spread online in complete and utter silence. Once the virus gets installed, its shenanigans begin almost immediately. By performing a thorough scan, it locates all your private data. Yes, this infection is aiming directly at your personal information. Why? Because it will upset you the most by encrypting your files. Do you now realize why so many people are afraid of ransomware? These programs are so impressively destructive that they must be avoided at all cost. After the scan is complete, this nuisance starts locking your data. By using a highly complicated encrypting cipher, it locks everything. Pictures and music and videos and documents. And more. Anything of importance on your machine falls victim to the parasite. Obviously, some precious and valuable files may get infected as well. That’s precisely what hackers want. The more havoc this infection wreaks, the better. It’s not easy to remain calm and collected when all your data gets locked out of the blue. Your infected data has been renamed and now has the .Cerber2 extension. The minute you see this appendix, know you’re in trouble. What the parasite actually does is, it copies your files. Then it deletes the originals. You can see what that leaves you with, can’t you? The encrypted (and unusable) copies. This is quite a clever technique created solely to scam naive people. As we mentioned, it’s very important not to give into panic. Yes, your files are encrypted. Yes, you have a dangerous infection on board. But you must remember that anxiety and worry will not solve the problem. If anything, giving into despair will make things worse. While encrypting your information, the virus drops payment instructions. It modifies your desktop wallpaper; it also creates .txt and .html files. They get added to all folders which contain locked information. As you could imagine, those are quite a lot of folders. The ransomware infects a huge variety of file formats – .pdf, .jpg, .png, .mp3, mp4, .doc, .docx, .xls, etc. Long story short, you now see a ransom message all the time. Its goal is to trick you into paying a hefty sum of money in Bitcoin (online currency). Needless to say you should never let hackers involve you in their scams. This infection is trying to blackmail you so make no mistake. Don’t even consider giving your money to cyber crooks.
How did I get infected with?
The ransomware mainly gets spread via spam email-attachments. Next time you spot something questionable in your inbox, delete it. Otherwise, you may end up compromising your own computer. Be cautious. More often than not, parasites are disguised as job applications or legitimate emails. Keep an eye out for malware every single time you browse the Web. Your safety should be your number one priority on the Web. Stay away from spam messages from unknown senders as well. In addition, ransomware programs often use Trojans to get installed. They also use malicious torrents and unreliable websites as infiltration methods. The Internet is infested with potentially dangerous programs. Hackers are full of ideas to cause harm. You do the math. You could be careless online and install a whole bunch of virulent infections. Or you could take your time and protect your PC system. Make the right decision; you won’t regret it.
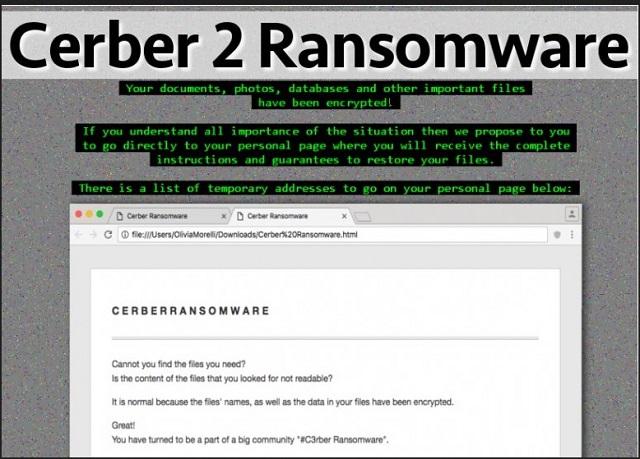
Why is Cerber2 dangerous?
Ransomware programs are a lot alike. They all follow the same pattern and don’t deviate from the rules much. The virus you’re now stuck with is quite similar to HolyCrypt, CryptVault, CryptoLocker, etc. You see, all these infections aim at your bank account. By locking your files, ransomware viruses play mind games with you. Be careful unless you want to get blackmailed and scammed. This program adds the .Cerber2 extension thus making your information inaccessible. Your computer is unable to read the new file format; you’re unable to use your files. Simple as that. Next step in the scheme are the ransom messages. Remember, ransomware is trying to steal your money. Thus, you cannot afford to trust ANY of its malicious promises and offers. Hackers are supposed to provide you a decryption key which sets your data free. However, this is nothing but a way to extort Bitcoins from gullible PC users. Don’t be a gullible PC user. Instead of paying the ransom, get rid of the parasite. Don’t support hackers’ illegitimate businesses and don’t become their sponsor. To delete this pest manually, please follow our detailed removal guide down below.
Cerber2 Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Cerber2 Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Cerber2 encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Cerber2 encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



