Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Can’t Remove Remove 1JBFFHR8tGiMgYLpnZCVG8n4cSpm591urc Malware pop-ups?
1JBFFHR8tGiMgYLpnZCVG8n4cSpm591urc is a Bitcoin address. It’s one, you get asked to use, and send money to. Why? Well, supposedly, to pay off cyber criminals, who have compromising videos of you. Let’s explain. First off, you have to realize, there’s a scamware, lurking on your computer. You’re the victim of a scamware attack. The nasty tool finds a way to infiltrate your system. Then, once it settles, you receive an email. One that seems to come from your own account. But appearances can be deceiving. The email is a spoof, and aims to affirm the illusion that you’re in trouble. The email claims that your PC got hacked, a while back. And, there’s now a Trojan, on board. The hackers state, they have videos of you, which you wouldn’t want to get shared. And, that, if you wish for them not to get shared, you must follow their demands. They request payment in Bitcoin to the 1JBFFHR8tGiMgYLpnZCVG8n4cSpm591urc address. Do NOT pay these cyber criminals. There’s no Trojan on your computer. Hackers don’t have compromising videos of you. Consider this a phishing scam. These malicious strangers feed you lies, and hope you fall for them. Don’t bite their lure. Don’t act against your best interests. It’s a scam. Find the scamware’s exact hiding place, and remove it. The sooner you do, the better.

How did I get infected with?
Scamware tools are sneaky. They resort to all manner of tricks, when it comes to invasion. And, believe it or not, more often than they, they invade via spam emails. Yes, you get an email that appears to come from a legitimate source. Like, a well-known company, like DHL, or PayPal. The email contains a link, and it urges you to click it. Or, has an attachment, it wants you to download. It claims that you must do so to ‘verify information‘ or ‘confirm a purchase.‘ It feeds you a lie, and hopes you’re careless enough not to realize it. The infection preys on your carelessness. Your naivety, haste, and distraction ease its infiltration. Make sure not to provide them. Always be thorough, and take the time to do your due diligence. Attention goes a long way. Other common invasive methods include the following. Hiding behind freeware, fake updates, corrupted links, sites, or torrents. The cyber threat has quite the list of tricks to choose from. Whichever one, it ends up going with, you’re the last line of defense. Caution helps you to keep an infection-free PC. Carelessness doesn’t. Make the right choice.
Why are these ads dangerous?
The email claims that the hackers have access to your microphone and camera. They say, they have collected pictures and videos of you, doing provocative activities. And, threaten that, unless you comply, they’ll release them to your contacts. You, usually, get stuck with a deadline. You get two days to complete the transfer to the 1JBFFHR8tGiMgYLpnZCVG8n4cSpm591urc address. The ransom, they demand, varies in price. It tends to stay between 700 and 800 US Dollars, according to most reports. However, even if the request were for a single dollar, you still shouldn’t pay. Don’t fall for the sham! Users, who received such an email, don’t even have cameras on their devices. The cyber extortionists use scare tactics. They hope to profit off of your fear and naivety. Don’t let them! Acknowledge that you’ve fallen prey to scammers. Do your best to locate the hiding place of the scamware, responsible for the email. Then, as soon as you discover it, delete it. And, remember. Don’t pay a ransom for a non-existent threat.
How Can I Remove Remove 1JBFFHR8tGiMgYLpnZCVG8n4cSpm591urc Malware Pop-ups?
If you perform exactly the steps below you should be able to remove the infection. Please, follow the procedures in the exact order. Please, consider to print this guide or have another computer at your disposal. You will NOT need any USB sticks or CDs.
STEP 1: Uninstall suspicious software from your Add\Remove Programs
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 2: Delete unknown add-ons from Chrome, Firefox or IE
STEP 1 : Uninstall unknown programs from Your Computer
Simultaneously press the Windows Logo Button and then “R” to open the Run Command
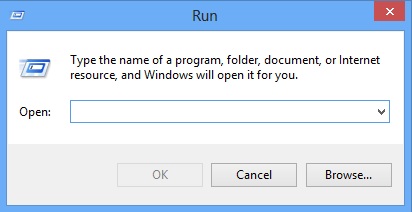
Type “Appwiz.cpl”
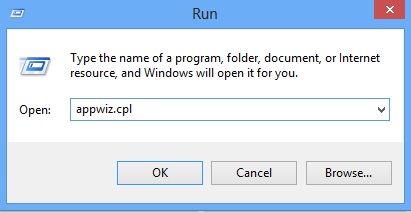
Locate the any unknown program and click on uninstall/change. To facilitate the search you can sort the programs by date. review the most recent installed programs first. In general you should remove all unknown programs.
STEP 2 : Remove add-ons and extensions from Chrome, Firefox or IE
Remove from Google Chrome
- In the Main Menu, select Tools—> Extensions
- Remove any unknown extension by clicking on the little recycle bin
- If you are not able to delete the extension then navigate to C:\Users\”computer name“\AppData\Local\Google\Chrome\User Data\Default\Extensions\and review the folders one by one.
- Reset Google Chrome by Deleting the current user to make sure nothing is left behind
- If you are using the latest chrome version you need to do the following
- go to settings – Add person
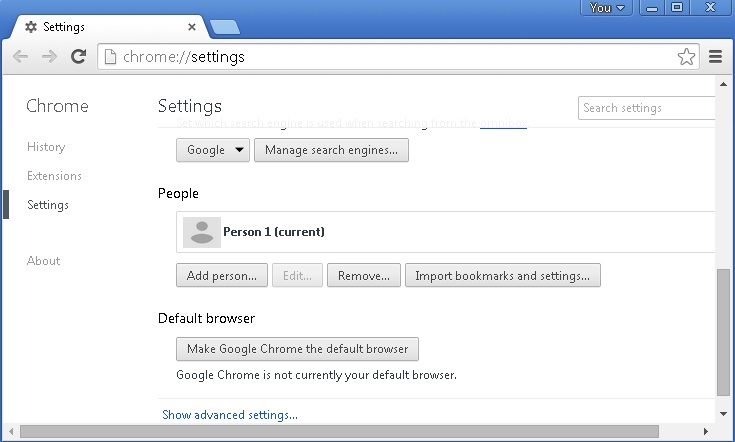
- choose a preferred name.
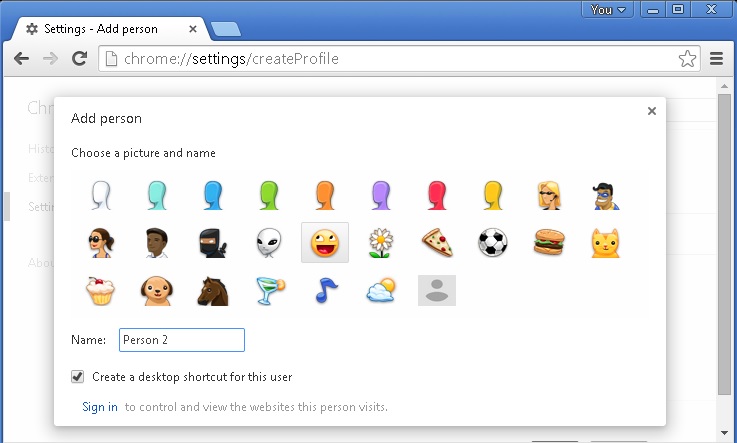
- then go back and remove person 1
- Chrome should be malware free now
Remove from Mozilla Firefox
- Open Firefox
- Press simultaneously Ctrl+Shift+A
- Disable and remove any unknown add on
- Open the Firefox’s Help Menu
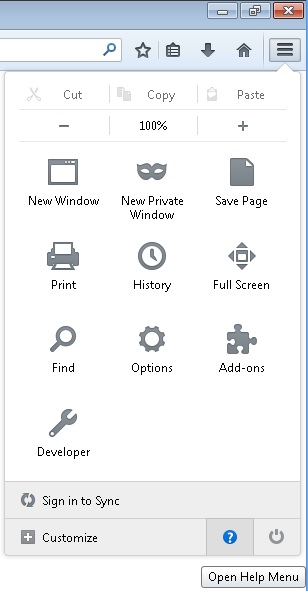
- Then Troubleshoot information
- Click on Reset Firefox
Remove from Internet Explorer
- Open IE
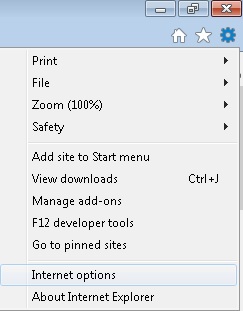
- On the Upper Right Corner Click on the Gear Icon
- Go to Toolbars and Extensions
- Disable any suspicious extension.
- If the disable button is gray, you need to go to your Windows Registry and delete the corresponding CLSID
- On the Upper Right Corner of Internet Explorer Click on the Gear Icon.
- Click on Internet options
- Select the Advanced tab and click on Reset.
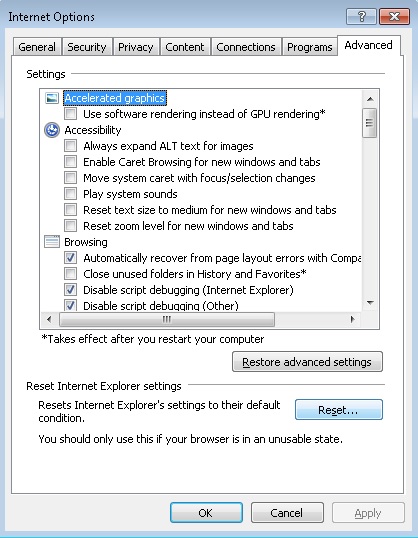
- Check the “Delete Personal Settings Tab” and then Reset
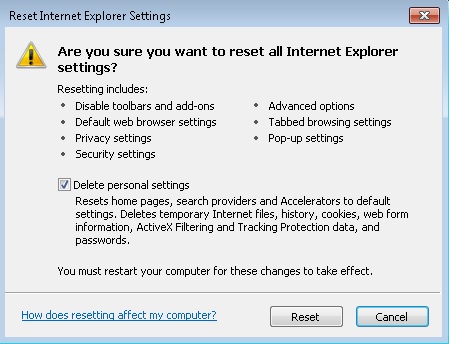
- Close IE
Permanently Remove Remove 1JBFFHR8tGiMgYLpnZCVG8n4cSpm591urc Malware Leftovers
To make sure manual removal is successful, we recommend to use a free scanner of any professional antimalware program to identify any registry leftovers or temporary files.