Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Can’t Remove Remove 1GB22WpNfFPcAYnad1Sd3qWoVJeDbtN72M Malware pop-ups?
The email reads:
Hi! As you may have noticed, I sent you an email from your account. This means that I have full access to your account: At the time of hacking your account(**********) had this password: *********** You can say: this is my, but old password! Or: I can change my password at any time! Of course! You will be right, but the fact is that when you change the password, my malicious code every time saved a new one! I’ve been watching you for a few months now. But the fact is that you were infected with malware through an adult site that you visited. If you are not familiar with this, I will explain. Trojan Virus gives me full access and control over a computer or other device. This means that I can see everything on your screen, turn on the camera and microphone, but you do not know about it. I made a video showing how you satisfy yourself in the left half of the screen, and in the right half you see the video that you watched. With one click of the mouse, I can send this video to all your emails and contacts on social networks. I can also post access to all your e-mail correspondence and messengers that you use. If you want to prevent this, transfer the amount of $720 to my bitcoin address (if you do not know how to do this, write to Google: “Buy Bitcoin”). My bitcoin address (BTC Wallet) is: 1GB22WpNfFPcAYnad1Sd3qWoVJeDbtN72M After receiving the payment, I will delete the video and you will never hear me again. I give you 48 hours to pay.I have a notice reading this letter, and the timer will work when you see this letter. Filing a complaint somewhere does not make sense because this email cannot be tracked like my bitcoin address.
1GB22WpNfFPcAYnad1Sd3qWoVJeDbtN72M is a Bitcoin address. One that cyber criminals, urge you to use, and send a payment to. Let’s elaborate. You’re the victim of an invasion. A cyber threat slithered its way into your PC. One that belongs to the scamware category. It infiltrated your system via slyness and finesse. And, is now attempting to extort you for profit. Here’s the thing. Once the scamware invades, you receive an email. It appears to come from your own account, but that’s a trick. In actuality, it’s a spoof email, designed to further the illusion that a hacker has control of your system. Don’t fall for it. The email is pretty standard. It uses scare tactics, and preys on your naivety. It tries to convince you of the hack, and places a plethora of threats before you. The infection’s goal is to get you to act against your best interests. Don’t fall for its deception. Try to stay level-headed, and acknowledge the trickery. Accept that the mail is a direct consequence of a cyber threat’s invasion. Discover its exact hiding place. Then, delete it ASAP. The faster the scamware leaves your system, the better.

How did I get infected with?
Scamware tools use trickery to invade your PC. They turn to the old but gold methods, and slip past you undetected. However, they can do that, only if you’re careless. Your carelessness, proves essential for their covert invasion. Here’s the thing. These program use a variety of methods to infiltrate your computer. Freeware, spam emails, corrupted links, sites or torrents, fake updates. They have their pick of tricks. But whichever one, they end up choosing, it proves useless, unless you’re careless. Think about it. If you’re thorough, and take your time, you can catch the cyber threat in the act. You can spot it trying to sneak in unnoticed, and hinder its success. But, if you’re not, it manages to slip by you. Don’t ease its infiltration! Do your due diligence. Even a little extra attention can save you a ton of troubles. Next time, you allow anything off the web into your PC, be wary! Keep your eyes peeled, be thorough, and double-check everything. Make sure to read terms and conditions, and look for the fine print. Catch the infection in the act of attempting invasion. And, prevent its success. Caution helps you to keep an infection-free PC. Carelessness does the opposite. Make the right choice. Avoid dealing with the 1GB22WpNfFPcAYnad1Sd3qWoVJeDbtN72M Bitcoin address. And, the threat, behind it.
Why are these ads dangerous?
The email is a means to an end. The cyber criminals, behind the scamware, try to profit off of your fear and naivety. They try to make money of off you. How? Well, they feed you lies, and hope you bite. Once you open the email from the spoofed account, it states the following. Supposedly, your system got infected with a Trojan a while back. And, said Trojan made it easier for these criminals to spy on you. They tracked your every move, and didn’t stop there. They claimed to have control over your camera and microphone. “I can see everything on your screen, turn on the camera and microphone, but you do not know about it.” And, proceed to claim, they have videos and pictures. Ones of the sensitive nature. Then, they threaten to release them to your friends and contacts. “I can send this video to all your emails and contacts on social networks.” That is, unless you send them money to the provided Bitcoin address. The 1GB22WpNfFPcAYnad1Sd3qWoVJeDbtN72M one. It’s a scheme, users have come to calling, ‘sextortion.’ The price of the ransom varies. It can be anywhere from 500 to 1000 US dollars, or more. Regardless of the sum, you shouldn’t pay. Understand that the email spews out lies. It’s part of a sham to scam money off of you. Pay these people nothing. Acknowledge the email for what it is. A lie, crafted by cyber criminals, who seek to exploit you for monetary gain. There’s a scamware on board your PC. Find its exact hiding place. Then, delete it.
How Can I Remove Remove 1GB22WpNfFPcAYnad1Sd3qWoVJeDbtN72M Malware Pop-ups?
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
If you perform exactly the steps below you should be able to remove the infection. Please, follow the procedures in the exact order. Please, consider to print this guide or have another computer at your disposal. You will NOT need any USB sticks or CDs.
STEP 1: Uninstall suspicious software from your Add\Remove Programs
STEP 2: Delete unknown add-ons from Chrome, Firefox or IE
STEP 1 : Uninstall unknown programs from Your Computer
Simultaneously press the Windows Logo Button and then “R” to open the Run Command
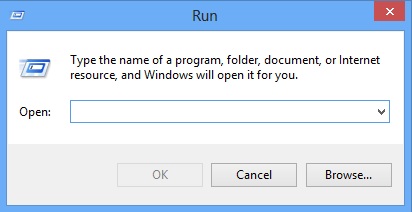
Type “Appwiz.cpl”
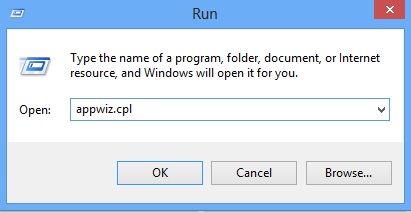
Locate the any unknown program and click on uninstall/change. To facilitate the search you can sort the programs by date. review the most recent installed programs first. In general you should remove all unknown programs.
STEP 2 : Remove add-ons and extensions from Chrome, Firefox or IE
Remove from Google Chrome
- In the Main Menu, select Tools—> Extensions
- Remove any unknown extension by clicking on the little recycle bin
- If you are not able to delete the extension then navigate to C:\Users\”computer name“\AppData\Local\Google\Chrome\User Data\Default\Extensions\and review the folders one by one.
- Reset Google Chrome by Deleting the current user to make sure nothing is left behind
- If you are using the latest chrome version you need to do the following
- go to settings – Add person
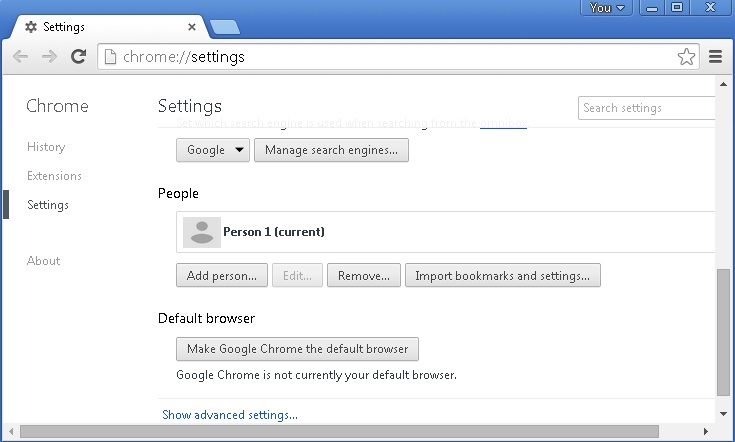
- choose a preferred name.
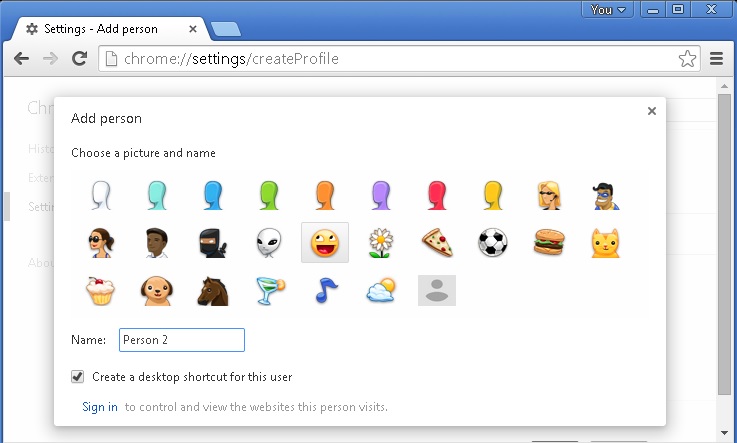
- then go back and remove person 1
- Chrome should be malware free now
Remove from Mozilla Firefox
- Open Firefox
- Press simultaneously Ctrl+Shift+A
- Disable and remove any unknown add on
- Open the Firefox’s Help Menu
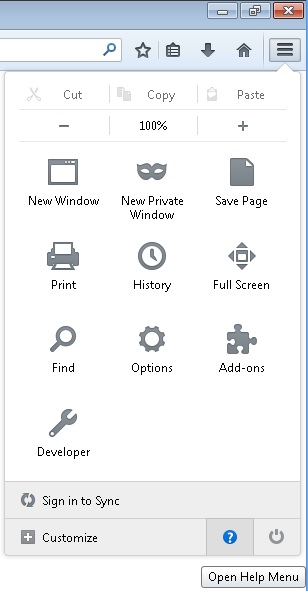
- Then Troubleshoot information
- Click on Reset Firefox
Remove from Internet Explorer
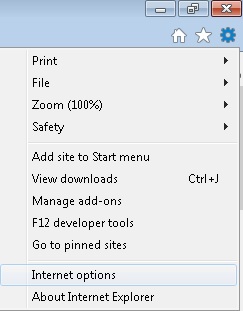
- Open IE
- On the Upper Right Corner Click on the Gear Icon
- Go to Toolbars and Extensions
- Disable any suspicious extension.
- If the disable button is gray, you need to go to your Windows Registry and delete the corresponding CLSID
- On the Upper Right Corner of Internet Explorer Click on the Gear Icon.
- Click on Internet options
- Select the Advanced tab and click on Reset.
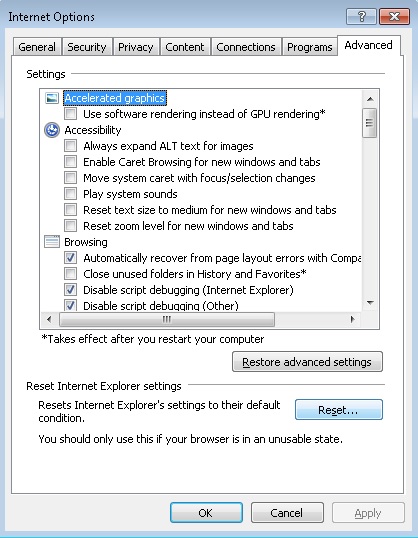
- Check the “Delete Personal Settings Tab” and then Reset
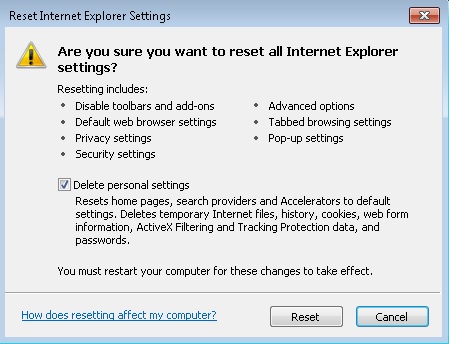
- Close IE
Permanently Remove Remove 1GB22WpNfFPcAYnad1Sd3qWoVJeDbtN72M Malware Leftovers
To make sure manual removal is successful, we recommend to use a free scanner of any professional antimalware program to identify any registry leftovers or temporary files.