Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Can’t Remove Remove 1EGgvLwVTQ3UGnjk4LzcPwyXaEk2Fioqd5 Malware pop-ups?
The email reads:
Hello! `
This is important information for you!
Some months ago I hacked your OS and got full access to your account *********
On day of hack your account ******* has password: ********
So, you can change the password, yes.. Or already changed… But my malware intercepts it every time.
How I made it:
In the software of the router, through which you went online, was a vulnerability. I used it…
If you interested you can read about it: CVE-2019-1663 – a vulnerability in the web-based management interface of the Cisco routers.
I just hacked this router and placed my malicious code on it.
When you went online, my trojan was installed on the OS of your device.
After that, I made a full backup of your disk (I have all your address book, history of viewing sites, all files, phone numbers and addresses of all your contacts).
A month ago, I wanted to lock your device and ask for a not big amount of btc to unlock.
But I looked at the sites that you regularly visit, and I was shocked by what I saw!!!
I’m talk you about sites for adults.
I want to say – you are a BIG pervert. Your fantasy is shifted far away from the normal course!
And I got an idea….
I made a screenshot of the adult sites where you have fun (do you understand what it is about, huh?).
After that, I made a screenshot of your joys (using the camera of your device) and glued them together.
Turned out amazing! You are so spectacular!
I’m know that you would not like to show these screenshots to your friends, relatives or colleagues.
I think $762 is a very, very small amount for my silence.
Besides, I have been spying on you for so long, having spent a lot of time!
Pay ONLY in Bitcoins!
My BTC wallet: 1EGgvLwVTQ3UGnjk4LzcPwyXaEk2Fioqd5
You do not know how to use bitcoins?
Enter a query in any search engine: “how to replenish btc wallet”.
It’s extremely easy
For this payment I give you two days (48 hours).
As soon as this letter is opened, the timer will work.
After payment, my virus and dirty screenshots with your enjoys will be self-destruct automatically.
If I do not receive from you the specified amount, then your device will be locked, and all your contacts will receive a screenshots with your “enjoys”.
I hope you understand your situation.
– Do not try to find and destroy my virus! (All your data, files and screenshots is already uploaded to a remote server)
– Do not try to contact me (you yourself will see that this is impossible, the sender address is automatically generated)
– Various security services will not help you; formatting a disk or destroying a device will not help, since your data is already on a remote server.
P.S. You are not my single victim. so, I guarantee you that I will not disturb you again after payment!
This is the word of honor hacker
I also ask you to regularly update your antiviruses in the future. This way you will no longer fall into a similar situation.
Do not hold evil! I just good do my job.
Good luck.
1EGgvLwVTQ3UGnjk4LzcPwyXaEk2Fioqd5 is a Bitcoin address. Cyber criminals ask you send money to it. In fact, they demand you send money to it. They present you with their Bitcoin wallet in an email. One that’s brimming with threats. Then, expect you to comply out of fear. These people prey on your naivety, and hope to profit off of it. Don’t let them! Here’s the thing. One day, you get an email. At first glance, it appears to come from your own email account. Take a second glance. On further inspection, you’ll see that it’s only a spoof email. And, the cyber criminals use it to further the illusion, they’re selling. And, that is, that they have hacked your PC, a while back. And, have used that time to spy on you, and gather lewd information from your online activities. They proceed to threaten to release said stolen information. That is, unless you comply with their demands. Do not! Don’t comply. Don’t contact them. Don’t pay them. Do nothing of the sort. Understand that you’re dealing with scamware. You’ve fallen prey to scammers. Do your best to discover the exact hiding place of the threat on your PC. Then, delete it the first chance you get. It’s the best course of action, you can take. Don’t delay taking it.

How did I get infected with?
Scamware uses trickery to invade. More often than not, they use spam emails. You get an email that appears to come from a legitimate source. Like, a well-known company. DHL, PayPal, Amazon. There are quite a few choices. The email states you have to download an attachment, or click a link. Supposedly, to verify data or confirm a purchase. If you follow its instructions, you’ll regret it. That’s how you allow the scamware into your PC, and not even know it. Of course, that’s not the only way. The infection can also sneak in via fake updates, freeware, corrupted links, sites, and torrents. The tool has plenty of tricks up its sleeve. It’s up to you to hinder its successful invasion. Always do your due diligence. Make sure to catch the threat in the act of attempting invasion. Spot it, and prevent its success. Vigilance is crucial. Take the time to be thorough. Read terms and conditions, look for the fine print. Know what you say YES to. Even a little extra attention can save you a ton of troubles.
Why are these ads dangerous?
As stated, 1EGgvLwVTQ3UGnjk4LzcPwyXaEk2Fioqd5 is a Bitcoin wallet. The scammers demand you make a payment to it. They request Bitcoins. The exact ransom amount varies, but tends to stay between 700 and 800 US Dollars. Of course, it can be much higher, as well. The ransom supposedly buys off the cyber criminals’ silence. They promise that, once you pay up, they won’t release what they stole from you. And, according to them, that’s videos of you doing lewd activities. Their email reads that, upon hacking your PC, they gained control of your camera. So, they have spied on your action from day one. And, have taken pictures and videos of you, in compromising positions. If you refuse to comply, they threaten to release them to the public. As well as, to your friends, coworkers, and family. After all, they claim to have access to your contacts, and social media accounts, too. These are all lies! These people feed you falsehoods, and hope you fall for them. Don’t! Don’t bite the lure, they set up. It’s all a scam. The sooner you accept that, the better. Don’t fall victim to deceit. Be sure to acknowledge the deception, and don’t act against your best interest. There aren’t enough ways to stress this. Don’t comply with these demands! Don’t send these cyber criminals a single dollar. Accept them for the scammers they are. And, act against the scamware, plaguing your system. The sooner you remove it, the better.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How Can I Remove Remove 1EGgvLwVTQ3UGnjk4LzcPwyXaEk2Fioqd5 Malware Pop-ups?
If you perform exactly the steps below you should be able to remove the infection. Please, follow the procedures in the exact order. Please, consider to print this guide or have another computer at your disposal. You will NOT need any USB sticks or CDs.
STEP 1: Uninstall suspicious software from your Add\Remove Programs
STEP 2: Delete unknown add-ons from Chrome, Firefox or IE
STEP 1 : Uninstall unknown programs from Your Computer
Simultaneously press the Windows Logo Button and then “R” to open the Run Command
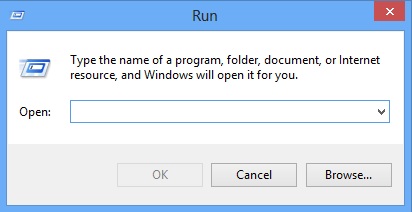
Type “Appwiz.cpl”
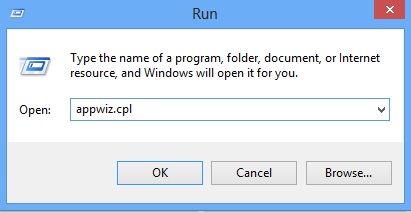
Locate the any unknown program and click on uninstall/change. To facilitate the search you can sort the programs by date. review the most recent installed programs first. In general you should remove all unknown programs.
STEP 2 : Remove add-ons and extensions from Chrome, Firefox or IE
Remove from Google Chrome
- In the Main Menu, select Tools—> Extensions
- Remove any unknown extension by clicking on the little recycle bin
- If you are not able to delete the extension then navigate to C:\Users\”computer name“\AppData\Local\Google\Chrome\User Data\Default\Extensions\and review the folders one by one.
- Reset Google Chrome by Deleting the current user to make sure nothing is left behind
- If you are using the latest chrome version you need to do the following
- go to settings – Add person
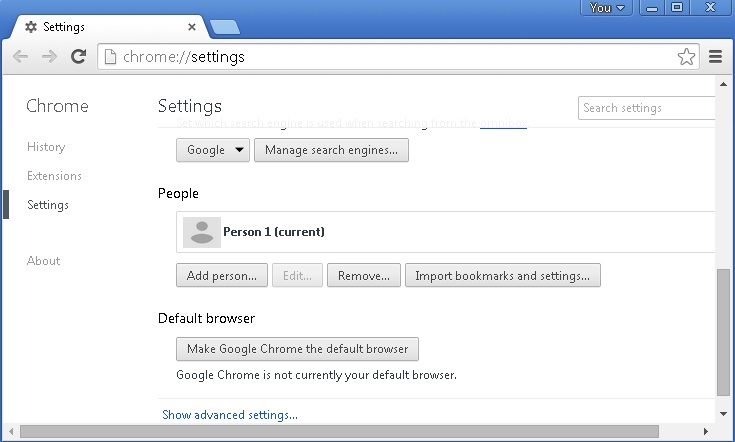
- choose a preferred name.
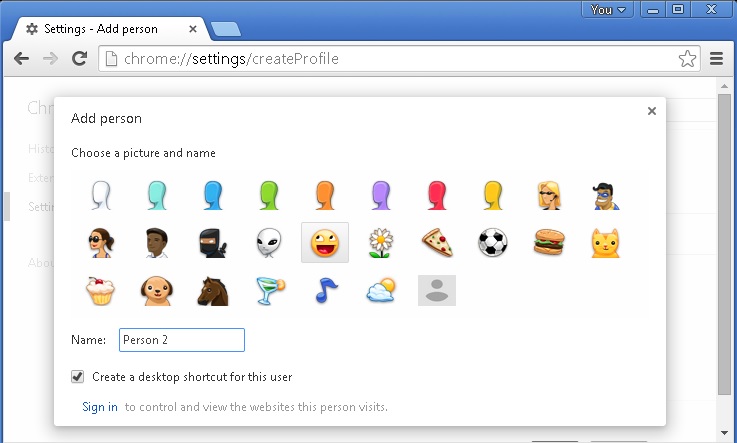
- then go back and remove person 1
- Chrome should be malware free now
Remove from Mozilla Firefox
- Open Firefox
- Press simultaneously Ctrl+Shift+A
- Disable and remove any unknown add on
- Open the Firefox’s Help Menu
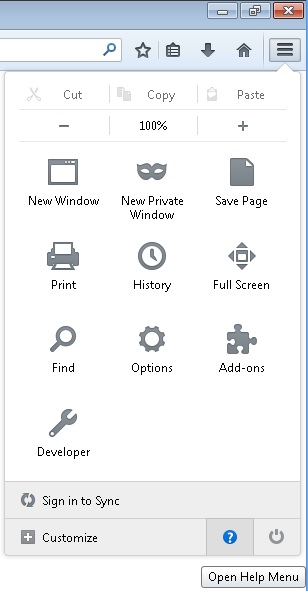
- Then Troubleshoot information
- Click on Reset Firefox
Remove from Internet Explorer
- Open IE
- On the Upper Right Corner Click on the Gear Icon
- Go to Toolbars and Extensions
- Disable any suspicious extension.
- If the disable button is gray, you need to go to your Windows Registry and delete the corresponding CLSID
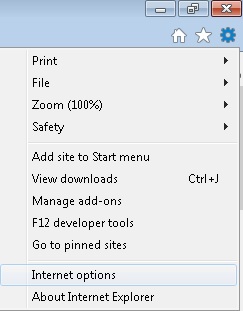
- On the Upper Right Corner of Internet Explorer Click on the Gear Icon.
- Click on Internet options
- Select the Advanced tab and click on Reset.
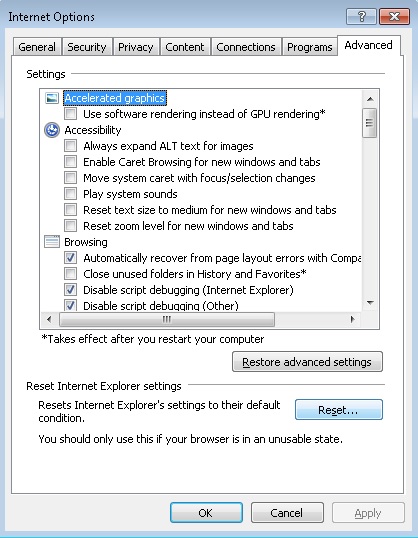
- Check the “Delete Personal Settings Tab” and then Reset
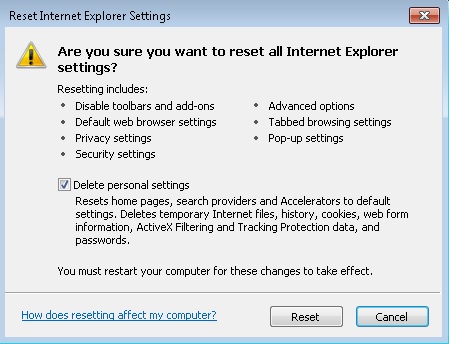
- Close IE
Permanently Remove Remove 1EGgvLwVTQ3UGnjk4LzcPwyXaEk2Fioqd5 Malware Leftovers
To make sure manual removal is successful, we recommend to use a free scanner of any professional antimalware program to identify any registry leftovers or temporary files.