Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Can’t Remove Remove 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y Malware pop-ups?
The 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y Bitcoin wallet is associated with a phishing email scam. The scheme behind which is quite simple. The crooks pretend to be hackers. They claim that a Trojan horse has infected your PC through a porn website. The crooks state that their virus has managed to record a compromising video of you. They threaten to leak that video to your contact list unless you pay up. And they are not shy about the sum. The asked amount varies from victim to victim, but it’s usually within the $700 to $800 (USD) range. The crooks even give deadlines. You have two days to transfer the money to the 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y wallet. If you fail to do so, the ransom will double. Do not give in! Recognize the email for what it is: a hoax. The scammers behind it exploit common misconceptions. They play with your fears and push you into impulsive actions. Don’t make their job easier! Slow things down. If you take a moment to consider the situation, you’ll see right through the lies. The 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y email doesn’t address you with your name or username. It doesn’t specify which website was used for the attack. It doesn’t provide proof of the video’s existence. The message is just a text composed by crafty crooks.

How did I get infected with?
The 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y message pops up by courtesy of scamware. As for the parasite, it sneaks into your OS through trickery. The parasite uses myriads of tricks to infect your computer. It hides behind freeware, pirated software, corrupted links, and spam messages. It hides in the shadows and waits for you to let your guard down. Do not make that mistake! No anti-virus app can protect you if you give into naivety. Only your vigilance can keep your PC secure and virus-free. Even a little extra attention can spare you an avalanche of problems. So, don’t be lazy. Always take the time to do your due diligence. Don’t visit questionable websites. Download software from reliable sources only. When available, use the advanced/custom setup option. And, of course, be very careful with your inbox. Do not give into naivety. The emails are still the number one virus distribution method. The parasites prey on your carelessness and recklessness. Don’t prove yourself an easy target. Treat all unexpected messages as potential threats. Whether is an instant message or an email, always verify the senders.
Why are these ads dangerous?
The alarming email pops up out of the blue. It threatens to leak a compromising video of you if you don’t comply with the crooks requirements. These criminals ask for an astonishing amount of money paid in Bitcoin. Their choice of currency is not a caprice. You cannot get your money back once you transfer them to the 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y wallet. The Bitcoin currency is untraceable. So, don’t swing into action. Paying the ransom won’t accomplish anything. The crooks have nothing against you. They use scare tactics to lure you into unwanted actions. Do not fall for their tricks! Do not open your wallet. Don’t pay for a non-existent threat. Acknowledge that you’ve fallen prey of scamware. A parasite lurks in the shadows of your operating system and threatens to lure you into a trap. Do yourself a huge favor. Located the piece of malware and delete it before it gets you in serious trouble. The sooner you clean your OS, the better!
How Can I Remove Remove 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y Malware Pop-ups?
If you perform exactly the steps below you should be able to remove the infection. Please, follow the procedures in the exact order. Please, consider to print this guide or have another computer at your disposal. You will NOT need any USB sticks or CDs.
STEP 1: Uninstall suspicious software from your Add\Remove Programs
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 2: Delete unknown add-ons from Chrome, Firefox or IE
STEP 1 : Uninstall unknown programs from Your Computer
Simultaneously press the Windows Logo Button and then “R” to open the Run Command
Type “Appwiz.cpl”
Locate the any unknown program and click on uninstall/change. To facilitate the search you can sort the programs by date. review the most recent installed programs first. In general you should remove all unknown programs.
STEP 2 : Remove add-ons and extensions from Chrome, Firefox or IE
Remove from Google Chrome
- In the Main Menu, select Tools—> Extensions
- Remove any unknown extension by clicking on the little recycle bin
- If you are not able to delete the extension then navigate to C:\Users\”computer name“\AppData\Local\Google\Chrome\User Data\Default\Extensions\and review the folders one by one.
- Reset Google Chrome by Deleting the current user to make sure nothing is left behind
- If you are using the latest chrome version you need to do the following
- go to settings – Add person
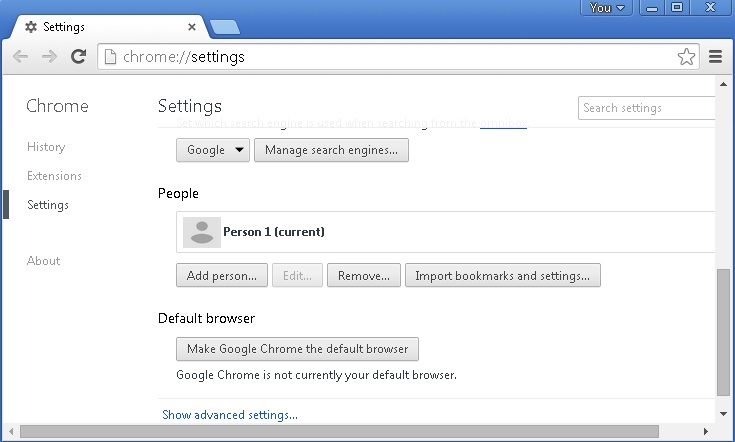
- choose a preferred name.
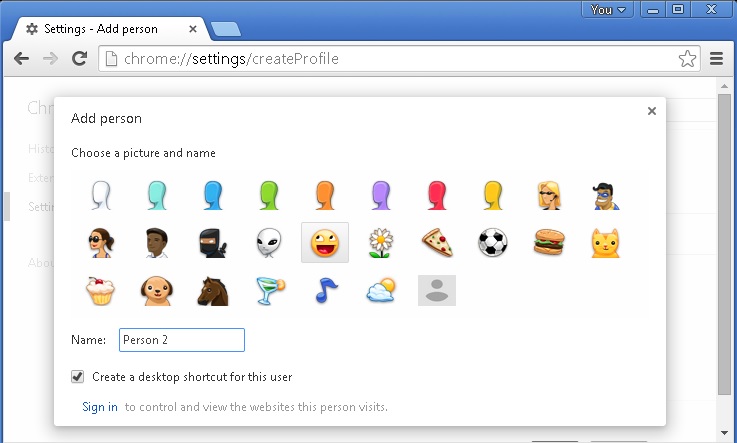
- then go back and remove person 1
- Chrome should be malware free now
Remove from Mozilla Firefox
- Open Firefox
- Press simultaneously Ctrl+Shift+A
- Disable and remove any unknown add on
- Open the Firefox’s Help Menu
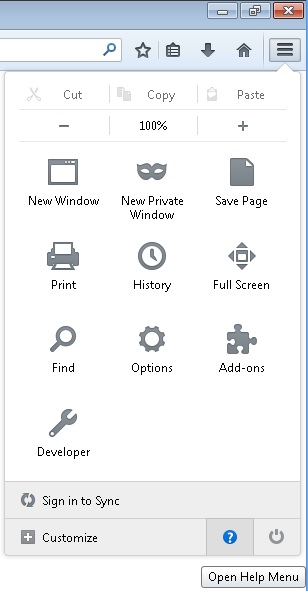
- Then Troubleshoot information
- Click on Reset Firefox
Remove from Internet Explorer
- Open IE
- On the Upper Right Corner Click on the Gear Icon
- Go to Toolbars and Extensions
- Disable any suspicious extension.
- If the disable button is gray, you need to go to your Windows Registry and delete the corresponding CLSID
- On the Upper Right Corner of Internet Explorer Click on the Gear Icon.
- Click on Internet options
- Select the Advanced tab and click on Reset.
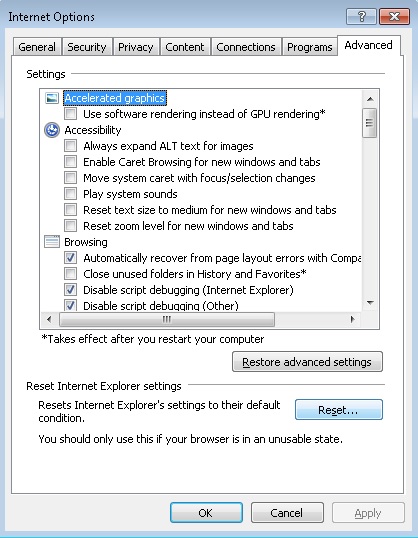
- Check the “Delete Personal Settings Tab” and then Reset
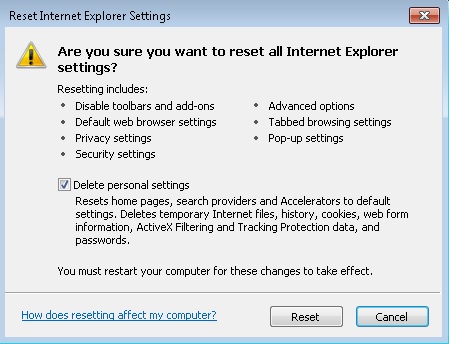
- Close IE
Permanently Remove Remove 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y Malware Leftovers
To make sure manual removal is successful, we recommend to use a free scanner of any professional antimalware program to identify any registry leftovers or temporary files.