Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove De_crypt_readme Ransomware?
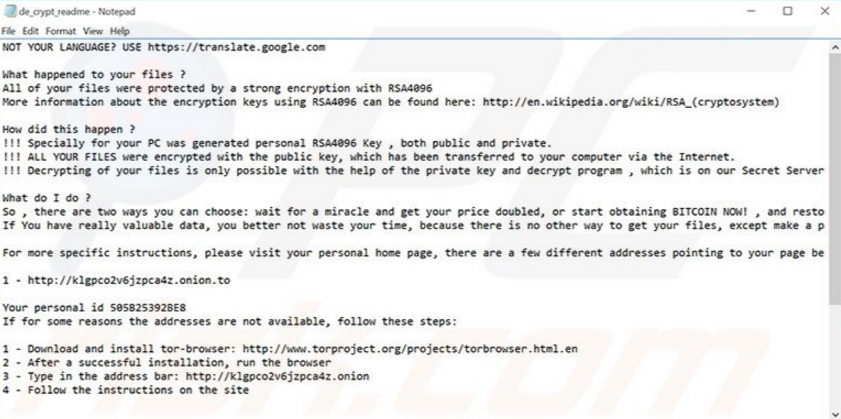
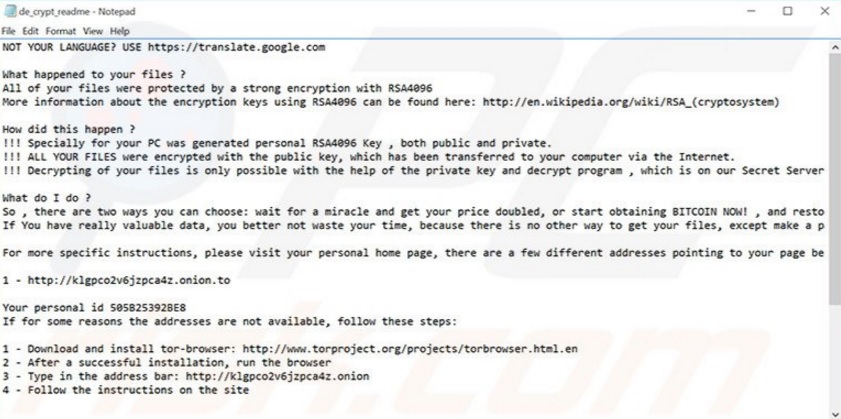
You’ve been unfortunate enough to catch a ransomware virus. Those are among the most dreaded types of infections you could have possibly come across online. Are you feeling unlucky? In this particular case the parasite you’re stuck with is called Crypt XXX. It appeared on the Web quite recently but already managed to cause thousands of people some serious damage. Now, before we proceed to the removal guide, there are a couple of things you should learn about this malicious parasite first. Hackers are always extremely well-informed when it comes to malware; are you? In the never-ending battle against cyber criminals the more you know, the better. Crypt XXX follows the classic ransomware pattern. It gets installed, it encrypts your personal files, it demands ransom. However, this pest exhibits some unusual, disturbing traits that make it very problematic. To begin with, Crypt XXX uses RSA4096 – a highly complicated asymmetric encrypting algorithm. We’ve already written many articles dedicated to ransomware programs that use such an algorithm. What does asymmetric mean? It means while encrypting your data, the virus creates two different keys. One of them is public (used to encrypt files) and the other one is private (used to decrypt files). As you could imagine, the incredibly valuable private key is known only to hackers. And they are not willing to give it for free. Asymmetric cryptography is a notoriously tricky system, as you’re soon to be convinced. Also, once Crypt XXX gets activated, consider your data gone. Pictures, music, Microsoft Office documents, presentations, videos – all of it is now inaccessible. The virus is very aggressive and takes down all your personal information, then holds it hostage. What if you have some immensely important files stored on your computer? They get locked as well. There’s no way to use or even view your encrypted data without the aforementioned decryption key. You can already tell why ransomare is so notoriously harmful, can’t you? We’ve noticed a great number of ransomware-type infections which rises at an alarming rate. That is because ransomware is effective. Many people would give into their anxiety seeing such random, unauthorized, unexpected modifications. Once you give into panic, you no longer think logically and that is exactly what hackers are aiming for. Crypt XXX drops de_crypt_readme.bmp, de_crypt_readme.html and de_crypt_readme.txt files. You will find them in each folder containing encrypted data. Here’s a clue – those are a lot of folders. The only reason why you’re currently seeing these files practically everywhere is because they provide payment instructions. You’re supposed to either “wait for a miracle and get your price doubled, or start obtaining BITCOIN NOW!”. Quite an aggravating way to ask for a ransom, isn’t it? Hackers promise to give you the decryption key in exchange for 1.2 Bitcoin which approximately equals to 535 USD. As you figured out already, if you don’t make the payment on time, the sum is supposed to double.
How did I get infected with?
It’s not a challenging task to get your machine infected with ransomware. This pest mainly travels the Web as a malicious attachment to spam emails or spam messages. It might also get installed with the help of a sneaky Trojan horse. In order to protect your machine from such parasites in the future, always pay attention to your safety. Keeping your device infection-free should be your number one priority every single time you browse the Web. Stay away from questionable websites, suspicious-looking executables, torrents and third-party ads. More often than not, those are harmful. Another popular infiltration technique is freeware/shareware bundling as it allows hackers to fill in your computer with malware in no time. We highly recommend you to stay away from illegitimate pages and the illegitimate bundles they offer. Also, don’t skip installation steps unless you’re willing to compromise your PC yourself. To sum up, the Crypt XXX virus may come from various sources. Keep an eye out for malware in the future and be cautious online.
Why is De_crypt_readme dangerous?
Due to the parasite’s shenanigans, you are now denied access to your own data. You will notice a brand new .crypt appendix that replaced your original file extensions. The machine can’t recognize this malicious file format so, logically, it can’t read your data. Unless you have a special decrypter, you cannot restore your files. What’s even worse here is the fact greedy cyber criminals are trying to take advantage of your disturbance. This whole scheme was created solely so hackers could blackmail you and, ultimately, steal about 535 USD of yours. Remember, this is a fraud. There’s absolutely no guarantee whatsoever that after paying the money demanded you will receive anything from crooks. As you could imagine, hackers aren’t exactly famous for being honorable people. Even if you keep your end of the bargain, your files might still remain encrypted. That is why you should never follow hackers’ instructions. Don’t pay anything. Instead, make sure you delete Crypt XXX on the spot and keep a backup of your most valuable data. To get rid of the ransomware manually, please follow the detailed removal guide that you’ll find down below.
De_crypt_readme Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 4: Recover De_crypt_readme Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with De_crypt_readme encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate De_crypt_readme encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.