Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
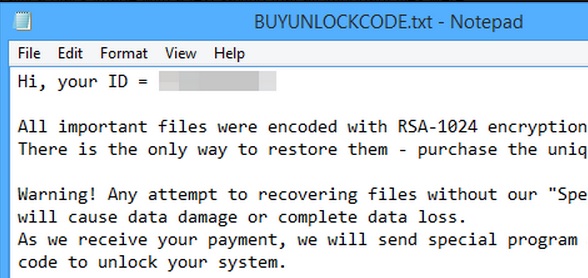
If you are seeing “All important files were encoded with RSA-1024 encryption…” message – you are infected with BUYUNLOCKCODE Ransomware!
You would certainly not enjoy being infected with BUYUNLOCKCODE ransomware because this virus will encrypt all your files, which means that you will not have access to any program or application on your PC. Your screen will be locked and you will be presented with a message saying that you need to purchase a “unique unlock code”.
Here is a portion of the threat message:
Hi, your ID = XXXXX
All important files were encoded with RSA-1024 encryption algorithm. There is the only way to restore them – purchase the unique unlock code.
Warning! Any attempt to recovering files without our “Special program” will cause data damage or complete data loss. As we receive your payment, we will send special program and your unique code to unlock your system.
Guarantee: You can send one of the encrypted file by email and we decode it for free as proof of our abilities.
No sense to contact the police. Your payment must be made to the e-wallet. It’s impossible to trace. Don`t waste your and our time.
So, if you are ready to pay for recovering your files, please reply this email Sin.Jun@tom.com
Then we will send payment instructions.
You are also threatened that you will lose your data if you do not buy the code or if you try to recover your files using other methods. All in all, ransomware BUYUNLOCKCODE removal is essential as there is not doubt the software is malicious and the consequences of its infiltration are damaging.
How did I get infected with?
Ransomware infections are distributed with the help of Trojans. If such an infection has found its way to your computer, very soon a ransomware infection will follow as the Trojan connects to the Internet and downloads it. It is very likely that you got infected with BUYUNLOCKCODE ransomware by opening a spam email attachment. This is how ransomware is mainly spread among users. If you want to prevent the infiltration of such infections, you should never open unknown or dubious looking emails with attachments, and should make sure your system is well maintained.
Why is it Dangerous?
It is important to remember to regularly back up your files because this is pretty much the only way to restore them if they have been encrypted by BUYUNLOCKCODE or any other ransomware. Please note that you should not buy the suggested unlock code under any circumstance. It does not guarantee that you will get your files back and will also put your banking details in the hands of cyber criminals. Data loss is more than enough of a damage, you do not need to lose money as well. When you encounter the message by BUYUNLOCKCODE ransomware, do not panic and take measures to remove the infection immediately.
BUYUNLOCKCODE Removal Procedure
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
from Windows 7 (Win 8 instructions are further below)
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your infected computer
- Restart the computer
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.

- Once the operating system loads press simultaneously the Windows Logo Button and the R key.

- A dialog box should open. Type iexplore www.virusresearch.org/download-en
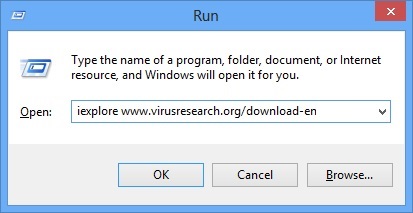
- your Internet Explorer will open and a professional scanner will start downloading
- Follow the instruction and use the professional malware removal tool to detect the files of the virus.
- After performing a full scan you will be asked to register the software. You can do that or perform a manual removal as shown in step 2
from Windows 8
Start Your Computer into Safe Mode with Networking
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Move the mouse to the upper right corner until the windows 8 charm menu appears
- Click on the magnifying glass
- select Settings
- in the search box type Advanced
- On the left the following should appear
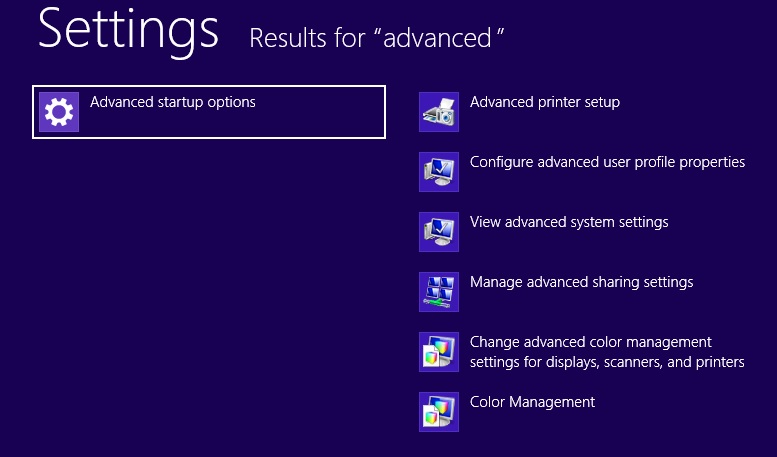
- Click on Advanced Startup Options
- Scroll down a little bit and click on Restart Now
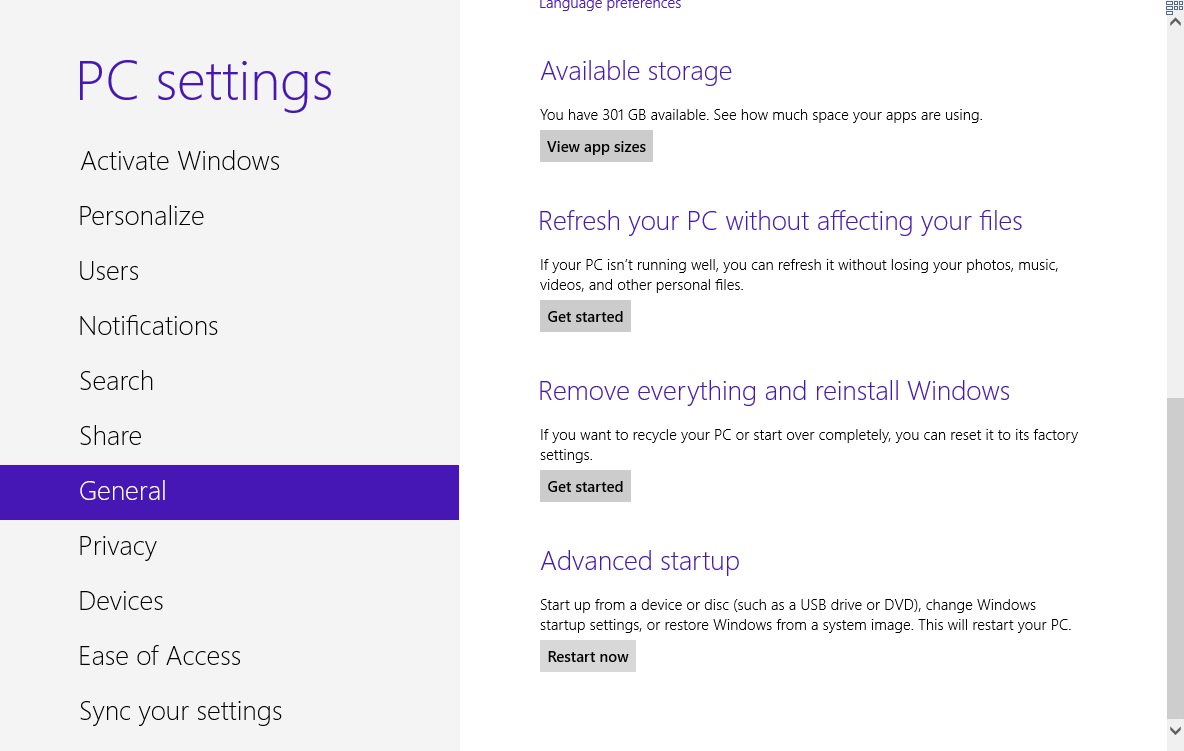
- Click on Troubleshoot
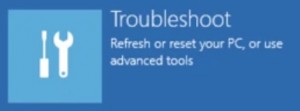
- Then Advanced options

- Then Startup settings

- Then Restart
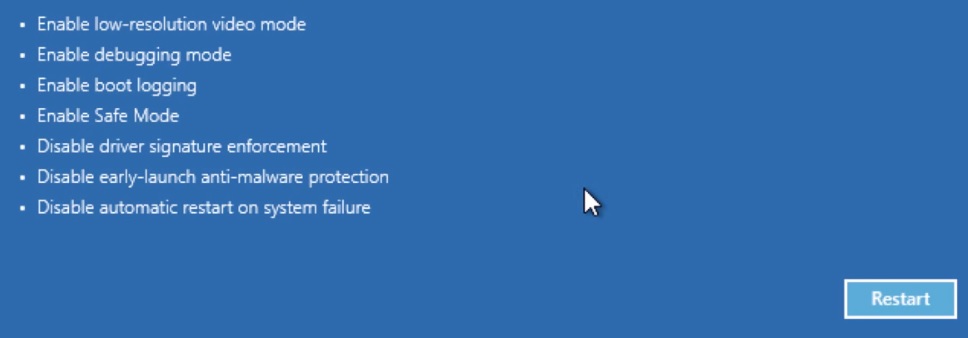
- When you see this screen press F5 – Enable Safe Mode with Networking

- Once the operating system loads press simultaneously the Windows Logo Button and the R key.

- A dialog box should open. Type iexplore www.virusresearch.org/download-en
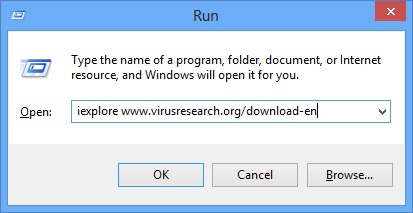
- Internet Explorer will open and a professional scanner will start downloading
- Follow the instruction and use the professional malware removal tool to detect the files of the virus.
- After performing a full scan you will be asked to register the software. You can do that or perform a manual removal.
- To perform Manual removal you need to follow the steps below.
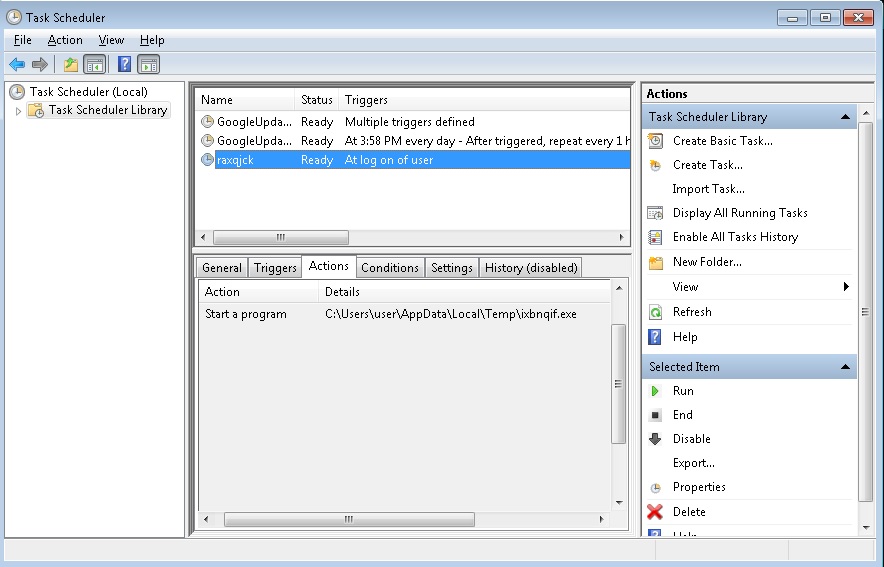
STEP 2: Locate the virus start-up point
Simultaneously press the Windows Logo Button and then “R” to open the Run Command
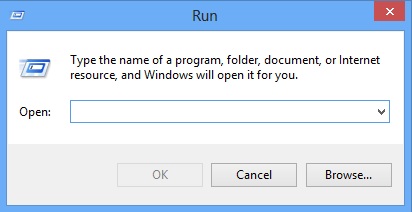
Type “taskschd.msc” in the box to open your Task Scheduler
After that, locate and remove the entries of the ransomware as shown below.
Delete the scheduled task and the file it is pointing at. Please not that the file name is random and yours might be different. The virus start-up location might be also in your Windows Registry Run Key – depending on the version you have.
HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce\bcdel cmd.exe /c del “%AppData%\SunDevPackUpdate\<random>.exe”
HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce\oldex cmd.exe /c del “path\RANDOM.exe”
HKCU\Control Panel\Desktop\Wallpaper “%AppData%\SunDevPackUpdate\wallpp.bmp”
Once you remove the starting location and delete the files, you can Restart Windows.
STEP 3: Restore Encrypted Files
There are several methods you can use, however nothing is guaranteed.
Method 1 – recover the encrypted files by hand:
You can try to use the built in feature of Windows called System Restore. By default the system restore feature is automatically turned on. Windows creates shadow copy snapshots that contain older copies since the system restore was performed. These snapshots will let us to recover any previous version of your file, although it will not be the latest one, still you can recover some important information. Please note, that Shadow Volume Copies are only available with Windows XP SP2, Vista, Windows 7 and Windows 8.
Method 2 – partially restore the encrypted files by using Microsoft Office junk files:
Basically you need to show your hidden files. The fastest way to do that is:
- Open Folder Options by clicking the Start button .
- In the search box type “FOLDER OPTIONS”.
- Select View TAB
- Under Advanced settings, find Show hidden files and folders and select it and then click OK.
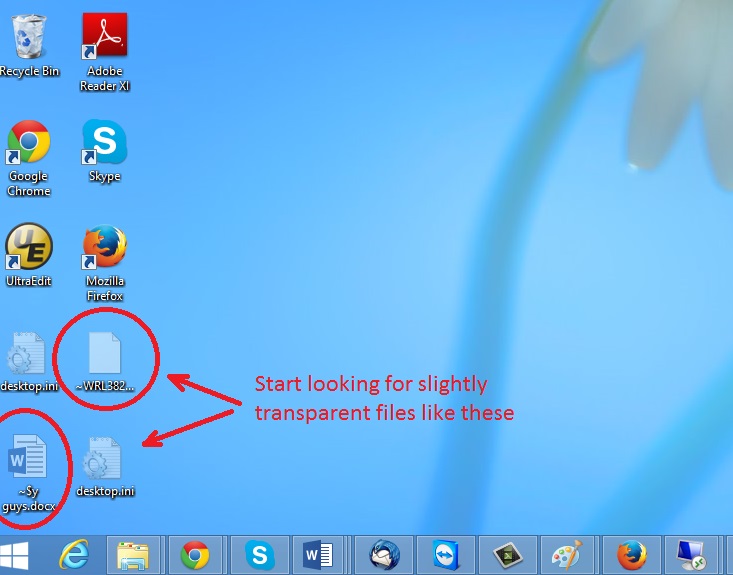
In the picture above I marked two hidden files. You are interested in every file that looks like ~WRL382.tmp This is actually a Microsoft office junk file that contains the previous version of the Word document itself. The Cryptowall parasite will not encrypt these files. The name of the file will be unknown, but you can recover a lot of lost documents using this method. This can be utilized for Microsoft Word and Microsoft Excel. In addition you can try to match the file sizes in order to figure out what is what and eventually you can restore a slightly older original document. In the picture on the left there is another method you can locate the files in question.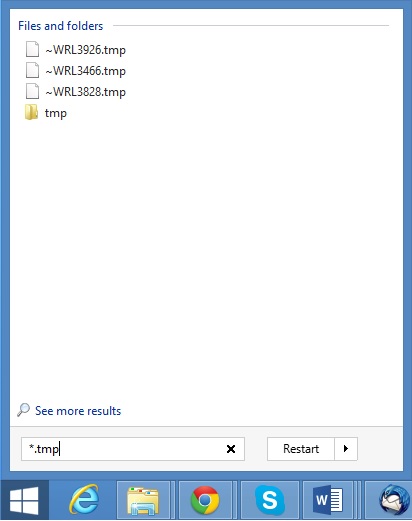 All you have to do is to hit the start button and type *.tmp. You will be presented a list of all the temp files located in your computer. The next thing is to open them one by one with Microsoft Word/Excel and recover the lost information, by saving it to another place. You can do that, by opening a new instance of MS Word/Excel, trough the file menu select open and then navigate to the location of the TMP file.
All you have to do is to hit the start button and type *.tmp. You will be presented a list of all the temp files located in your computer. The next thing is to open them one by one with Microsoft Word/Excel and recover the lost information, by saving it to another place. You can do that, by opening a new instance of MS Word/Excel, trough the file menu select open and then navigate to the location of the TMP file.
How to Decrypt the Encrypted Files
Unfortunately, there is no possibility to decrypt the crypted by BUYUNLOCKCODE files for now, unless you pay the ransom. Please, consider this as the very last option, because you might be funding further criminal activities.