Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Magic Ransomware?
There’s a new ransomware, roaming the internet, and becoming users’ greatest plague. The infection is named Magic, and trust us when we say: there’s nothing magical about it. Once it slithers into your system, you’re in trouble. The ransomware encrypts all of your files – pictures, documents, videos, music, movies, etc. Nothing is safe. Nothing is beyond its reach. All of a sudden, you find everything is no longer accessible. You can see it because it hasn’t moved. It’s right where you left it. But when you try to open it, you cannot. The one difference, which is truly visible, is that every file you have stored on your PC will be renamed. More specifically, each file will be renamed with the .magic file extension placed at the end. So, if you have a picture called ‘abc,’ after the ransomware’s done with it, it will be ‘abc.magic.’ After the ransomware is done with the encryption process, it demands you pay ransom if you wish to receive a decryption key and take back your files. So, if you to retain the key and decrypt your data, you’re required to pay one bitcoin, which is roughly the equivalent of $375 US. Do NOT pay! Do NOT go through with the ransom! There are several ways the exchange can go down, and they all end with you losing the fight against the ransomware. The game is rigged against you from the start. You can’t win. The best course of action you can take is just to say goodbye to your data and cut your losses. After all, files can be replaced, while with your private life – it’s an entirely different story. Make the right choice. Choose you, not your files.
How did I get infected with?
Ransomware doesn’t just appear on your system out of the blue as if by magic (pun intended). Same applies to the Magic infection. It cannot enter your system just because it feels like it. It’s bound to ask permission before it gets in, which means that your current predicament is due to you approving the installment of the nasty tool. You’re probably shaking your head in denial right now. After all, how can you agree to install an application, and then not remember it? Well, it’s rather straightforward. You don’t remember it because the infection slithered its way in through slyness and finesse. It duped you. It fooled you into permitting it in and kept you oblivious to it. You were clueless right until the point, the ransomware’s programming kicked in, and it encrypted everything, thus revealing itself. But how did it manage to trick you? Well, more often than not, it turns to the old but gold means of infiltration as they’ve proven their worth over time. Its favorite method is through freeware as it provided possibly the easiest entry point. That’s because, for reasons beyond comprehension, users throw caution to the wind and don’t even read the terms and conditions when installing freeware. They just agree with everything and hope for the best. Well, that’s a horrendous strategy with gruesome consequences. Other means of invasion include hiding behind spam email attachments or posing as a bogus update. Don’t rely on luck or chance! Do your due diligence! Remember, infections like the Magic ransomware, prey on carelessness! So, don’t provide it! Don’t rush and don’t give into distraction and naivety! Instead, be more thorough and attentive. Even a little extra attention goes a long way.
Why is Magic dangerous?
The virus bears the name magic.exe. Once it encrypts your data using AES encryption, it leaves two text files on your desktop. One of them is DECRYPT_ReadMe.TXT, and it contains the infection’s ransom demands. And, the other one is DECRYPT_ReadMe1.TXT. In it, the ransomware, all so thoughtfully, lists all of the affected files, which have been encrypted and are no longer accessible. After the encryption process is complete, you’re faced with a choice – pay or not pay. Experts strongly advise that you do NOT pay! Don’t comply with the infection’s demands for you have everything to lose and little to gain. Because think about it for a second. Even if you pay and you are given the decryption key, and it works, and every file is accessible again, how do you know that the ransomware won’t just put you through all of this again tomorrow? The answer is: you don’t! Nothing is stopping the pesky tool\s programming from kicking in again the very next day, and encrypt all of your data once more. Then you’re back to square one. Only this time, you’ve lost close to a $400 and, what’s worse, you’ve given access to your personal and financial information to strangers. By paying the infection’s ransom, you allow them into your private life. Do you believe that will end well for you? Are you prepared to take such a colossal gamble? Isn’t it bad enough that these unknown individuals have taken over your PC and quarantined your files, are you honestly going to let them in on your private details, as well? Don’t! Do yourself a favor, and pick the lesser evil – choose your privacy over your data. Don’t rely on the unknown third parties to keep their word, hand you the decryption key, and leave you be. That’s not going to happen. That’s not how it’s going to go down. The Magic ransomware is programmed to exploit you in any way possible. Don’t let it. Again: files can be replaced! Do yourself a favor, and say goodbye to your data. It may seem harsh, but it’s for the best.
Magic Removal Instructions
STEP 1: Start Your Computer into Safe Mode with Networking
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Restart the computer
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.

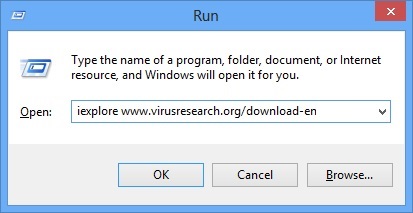
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type iexplore www.virusresearch.org/download-en
- Internet Explorer will open and a professional scanner will prompt to be downloaded
- Run the installer
- Follow the instruction and use the professional malware removal tool to detect the files of the virus.
- After performing a full scan you will be asked to register the software. You can do that or perform a manual removal.
Remove Magic Manually
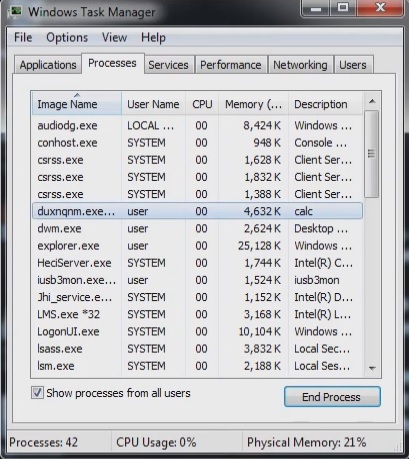
Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
Locate the process of teslacrypt. Have in mind that this is usually a random generated file.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Before you kill the process, type the name on a text document for later reference.
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you run the professional scanner to identify the files.
It is always a good idea to use a reputable anti-malware program after manual removal, to prevent this from happening again.