Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove AES-128 encryption Ransomware?
Ransomware is the worst type of cyber infection you could possibly come across online. And guess what, your computer has managed to catch it. That means you already know you’re in trouble. Ransomware exhibits many malicious traits and it’s perfectly capable of causing you irreversible damage. Therefore, you have absolutely no reason whatsoever to hesitate. The way ransomware-type programs work is, they use highly complicated encrypting algorithms to lock your personal files. Due to the parasite’s trickery, ALL OF YOUR DATA is being held hostage. Pictures, music, videos, your Microsoft Office documents – they’re inaccessible. And practically useless. Once the ransomware virus gets activated, it adds a random file extension to your data thus making it unreadable. Your machine can’t recognize this new file format and you cannot use/view/work with your very own personal information. And it goes without saying that there might be some immensely important files stored on the PC which fall victims to the parasite as well. However, you can’t expect hackers to take care of your Internet experience because this is not why ransomware exists. It exists to scam you. Once your personal data is completely locked, the virus starts demanding a certain sum of money. Apart from the fact these manipulations are extremely unfair, they could also seriously damage your bank account. So don’t allow it. Instead, take care of your machine ASAP. In today’s article we tackle AES-128 which is a particularly strong and problematic encryption. It’s used by some relatively new ransomware infections such as Locky and CoinVault. And, unfortunately, it’s destructive. Any virus that applies the AES-128 encryption is something you definitely do NOT want to deal with. For one thing, there is still no working mechanism to restore files that have been modified by this encryption protocol. You know what that means, don’t you? You can’t have your files back. As mentioned, ransomware viruses are not only very aggressive but notoriously harmful as well. The minute you notice some .txt file on the desktop asking for ransom, you know you’re in danger. However, if this aggravating ransom message is claiming that your data has been encrypted with rsa-2048 and AES-128 ciphers, consider your files gone. That is why it’s highly recommended to keep backups of your valuable personal information. Also, make sure you stay away from ransomware in the future. Don’t make the same mistake twice and don’t let cyber criminals harass you. If you want to remove the virus manually, keep on reading.
How did I get infected with?
Hackers have a rich variety of infiltration methods to choose from when it comes to spreading their parasites. Ransomware is stealthy. As you could imagine, nobody installs such a virulent threat voluntarily. That means the infection managed to land on board without your consent. For example, you might have come across some corrupted third-party commercial that you clicked. Well, now you realize that you should have ignored it. Another popular infiltration technique that many parasites apply is bundling freeware/shareware. It goes without saying that some of the oldest tricks in the book still work like a charm – watch out for spam email-attachments or various email messages from unknown senders. Crooks don’t seem to be giving them up any time soon so don’t overlook the serious danger those put you in. Ransomware might also be hiding within some malicious Word document. Another possibility is that the virus invaded your PC trough a Trojan horse or other similar infection. Always keep an eye out for potential parasites when surfing the Web unless you’re willing to compromise your own machine. There are many dangerous programs out there; it should be your number one priority online to prevent virus infiltration. Avoid suspicious looking web links, stay away from random executable files and pay close attention to the software you install.
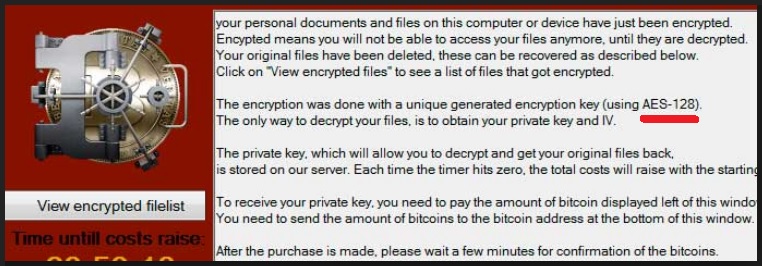
Why is AES-128 encryption dangerous?
The aforementioned ransom note is a clear sign that your files are already locked. However, there is a slight possibility that you could stop the encrypting process if you notice it on time. What you should know about the vicious AES-128 encryption is the fact it takes up a lot of CPU and memory. Therefore, it causes the computer speed to slow down drastically. In this situation it’s important that you take action immediately! Don’t hesitate to shut down the encrypting process because this way you could save your files. Keep in mind that any sluggishness exhibited by your machine has an explanation. In the worst case scenario, this explanation is ransomware. The AES-128 encryption, as you learned already, is very dangerous. Remember, no matter how many ransom notes you see on your PC screen and regardless of their bogus promises, you have to ignore them. Paying the ransom (which, by the way, is usually quite a hefty one) guarantees you nothing. You’re supposed to receive some highly questionable decryption key – a unique combination of symbols that should help you regain access to your infected files. The problem is, could you trust hackers? You might receive nothing in exchange for your money so paying the ransom is simply not an option. Do the right thing concerning your cyber security and don’t waste time because now is not the time to be a procrastinator. The ransomware will not delete itself. Make sure you remove the virus and don’t allow hackers to blackmail you. To delete this nuisance manually, please follow the detailed removal guide that you will find down below.
AES-128 encryption Removal Instructions
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with AES-128 encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate AES-128 encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
- and delete the display Name: backgroundcontainer

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
It is always a good idea to use a reputable anti-malware program after manual removal, to prevent this from happening again.



