Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Black.mirror@qq.com Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
[WHAT HAPPENED]
Your important files produced on this computer have been encrypted due a security problem
If you want to restore them, write us to the e-mail: black.mirror@qq.com
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us.
After payment we will send you the decryption tool that will decrypt all your files.
[FREE DECRYPTION AS GUARANTEE]
Before paying you can send to us up to 3 files for free decryption.
Please note that files must NOT contain valuable information
and their total size must be less than 1Mb
[HOW TO OBTAIN BITCOINS]
The easiest way to buy bitcoin is LocalBitcoins site.
You have to register, click Buy bitcoins and select the seller
by payment method and price
https://localbitcoins.com/buy_bitcoins
[ATTENTION]
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Do not rename encrypted files
Do not try to decrypt your data using third party software, it may cause permanent data loss
If you not write on e-mail in 36 hours – your key has been deleted and you cant decrypt your files
Your ID:
Ransomware is a particularly nasty type of virus. If you’ve ever crossed paths with a file-encrypting infection, you know just how bad things are. This time, you fell victim to one of the newest members of the ransomware family. Even though it’s a relatively young parasite, it is perfectly capable of stealing your money. All ransomware infections are strictly profit-oriented. The program currently on your PC is no different. As soon as it lands on board, problems start. Your entire device gets thoroughly scanned so the ransomware could locate your files. It goes without saying that this is the easiest step of hackers’ plan. The virus finds all your photos, music files, MS Office documents, videos. Basically, this parasite targets every single piece of information on your computer. Ransomware is focused on causing a mess. It’s incredibly successful in that department because your files get locked out of the blue. Before you know it, the virus has encrypted a huge variety of formats. The bigger the confusion and panic, the better. Hackers are shamelessly taking advantage of your anxiety because, after all, this is a scam. Your private files get renamed. You will notice that a [black.mirror@qq.com].aleta extension has been added to them. Seeing this extension means the encryption process is complete. You are no longer able to use, view or open any of your files. Most PC users store some very important information on their computers. We’d strongly recommend that you keep backups of your most precious data. If another ransomware program gets to you, you have to be prepared. Protecting your files could save you serious trouble in the future. Make sure never have to deal with file-encrypting infections again. The parasite uses a complicated algorithm to lock your data. It turns all your personal files into unreadable gibberish. As mentioned, the new file extension gives away that the encryption is over. Hackers hold your information hostage for one very prosaic reason. They offer you a special deal – if you buy a decryptor, you regain access to your data. As you could imagine, following hackers’ instructions wouldn’t really be a wise idea. The only thing crooks are trying to do is involve you in a fraud. Freeing your locked information is their last concern so paying simply isn’t an option. The parasite creates detailed ransom notes but you have to ignore all of them.
How did I get infected with?
The infection relies on stealthy infiltration methods to travel the Internet. Well, you wouldn’t voluntarily download an aggressive file-encrypting parasite. Thus, hackers present their infections as something else and wait for your curiosity to get the job done. The most commonly used method involves spam messages and emails. Every single time you come across a random email-attachment, know it could be malicious. Clicking it open lets the infections hiding there loose. Ultimately, you’re the one who compromises your own safety. Unless for some reason you want to test out the limits of your luck, stay away from any spam emails. Malware often is disguised as job applications or other perfectly safe messages. Save yourself the hassle that is fighting a cyber virus. Pay close attention to the programs you download too. The parasite could get attached to some freeware/shareware bundle and slither itself along the other programs. Stay away from illegitimate websites as well as the unverified software there. It is your job to protect your device from intruders. Ransomware might also use some help from other parasites, usually Trojan horses. Check out your PC and always be careful when surfing the Web.
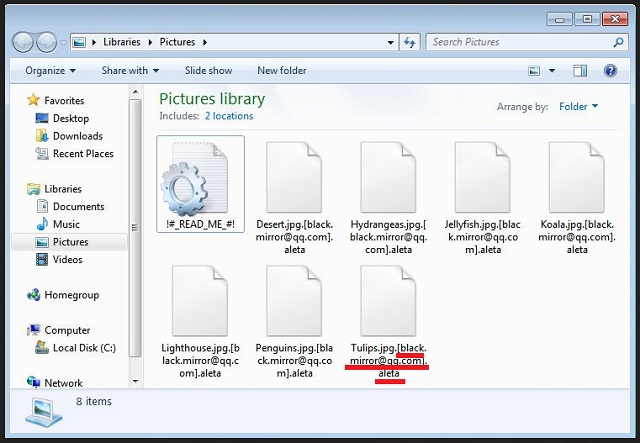
Why is Black.mirror@qq.com dangerous?
Your files become inaccessible. If you’re unfortunate enough to not have any backup copies, this trick could make you very nervous. As mentioned already, that is exactly what hackers are aiming for. They are making an effort to trick you into paying for a decryption key. According to the ransom notes dropped by the virus, you have to make a payment. However, you should know better than to give your Bitcoins away. Do not contact cyber criminals and stay away from the Black.mirror@qq.com email address. Even if you pay the entire ransom right now, your data might remain encrypted and unusable. Ransomware is nothing but a cheap attempt for a scam so be careful. Keep your Bitcoins instead of letting hackers blackmail you. Please follow our manual removal guide down below and get rid of the ransomware.
Black.mirror@qq.com Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Black.mirror@qq.com Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Black.mirror@qq.com encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Black.mirror@qq.com encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



