Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove TeslaCrypt Ransomware?
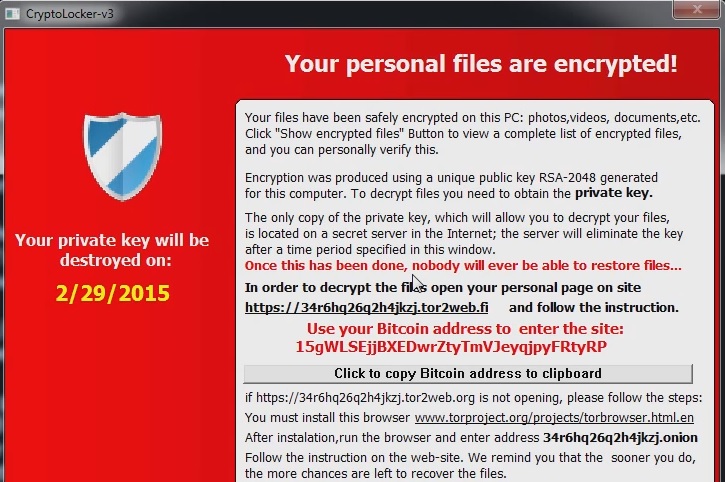
TeslaCrypt is the newest ransomware infection. If your desktop background has been changed and you are seeing a warning message saying that all your files have been encrypted, then it is obvious that a ransomware infection has gained access to your system. Another thing you will notice is that you will not be able to launch your browser, run your programs or open your files. These are all things typical for ransomware infections, so you cannot expect that TeslaCrypt will act any differently. If on the message it says CryptoLocker-v3, do not be surprised. This is just a different name for the same infection, and the consequences of its infiltration will also be the same. Although the displayed message will state that you should not delete TeslaCrypt ransomware, we strongly advise you to do it because such infections should not remain on your PC.
How did I get infected with?
Same as any other ransomware infection, TeslaCrypt is mainly distributed with the help of spam emails. In your spam folder you might discover emails from unknown senders containing attachments, and in their subject field it might say “Urgent”, “Important documents attached”, or anything else of this sort. This is a tactics cyber criminals use to attract your attention and to provoke your curiosity so that you open the corrupted email message and download the attachment. You might have assumed already that doing it will end up badly. This means that you will initiate the setup of TeslaCrypt ransomware or other infections. You should make sure you ignore the emails by unfamiliar senders in your spam folder in order to prevent future infiltration by TeslaCrypt ransomware.
Why is TeslaCrypt dangerous?
The main purpose of the hackers that created TeslaCrypt ransomware is to get as much money as possible from users. To do this they rely on the panic users will feel when they find out that they cannot access their files and programs. The majority of users will rush into paying the required ransom, but you should not be one of them. There is no guarantee that the suggested decryption key exists or that it will really help you decrypt your files. Also, TeslaCrypt ransomware should immediately be removed because it might perform suspicious activity behind your back like connecting to the Internet and attracting more infections to your PC. Even if you buy the decryption key, you should remove the infection because otherwise you will experience the same issues in future. The problem with the encrypted files still remains though, so what we would advise you to do is look for alternative decryption methods and perform file backup regularly.
TeslaCrypt Removal Instructions
STEP 1: Start Your Computer into Safe Mode with Networking
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Restart the computer
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.

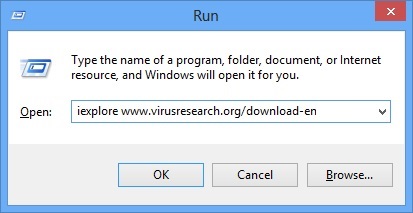
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type iexplore www.virusresearch.org/download-en
- Internet Explorer will open and a professional scanner will prompt to be downloaded
- Run the installer
- Follow the instruction and use the professional malware removal tool to detect the files of the virus.
- After performing a full scan you will be asked to register the software. You can do that or perform a manual removal.
Remove TeslaCrypt Manually
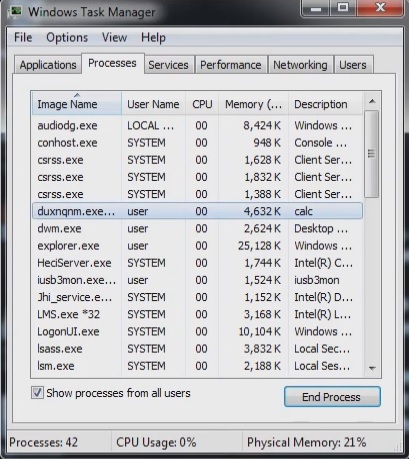
Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
Locate the process of teslacrypt. Have in mind that this is usually a random generated file.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Before you kill the process, type the name on a text document for later reference.
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you run the professional scanner to identify the files.
How to Restore the Encrypted Files
Method 1 – recover the encrypted files by hand:
You can try to use the built in feature of Windows called System Restore. By default the system restore feature is automatically turned on. Windows creates shadow copy snapshots that contain older copies since the system restore was performed. These snapshots will let us to recover any previous version of your file, although it will not be the latest one, still you can recover some important information. Please note, that Shadow Volume Copies are only available with Windows XP SP2, Vista, Windows 7 and Windows 8.
Method 2 – partially restore the encrypted files by using Microsoft Office junk files:
Basically you need to show your hidden files. The fastest way to do that is:
- Open Folder Options by clicking the Start button .
- In the search box type “FOLDER OPTIONS”.
- Select View TAB
- Under Advanced settings, find Show hidden files and folders and select it and then click OK.
It is always a good idea to use a reputable anti-malware program after manual removal, to prevent this from happening again.