Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Everis Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
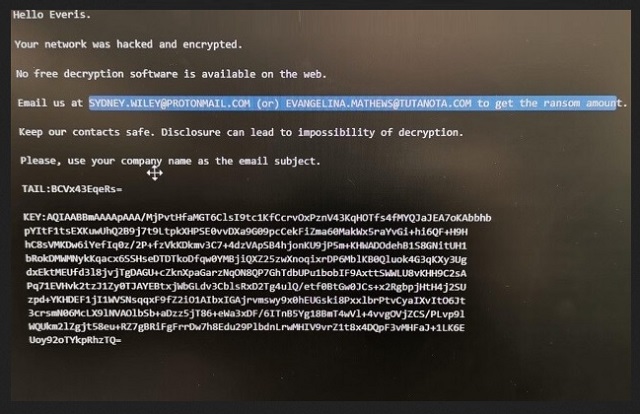
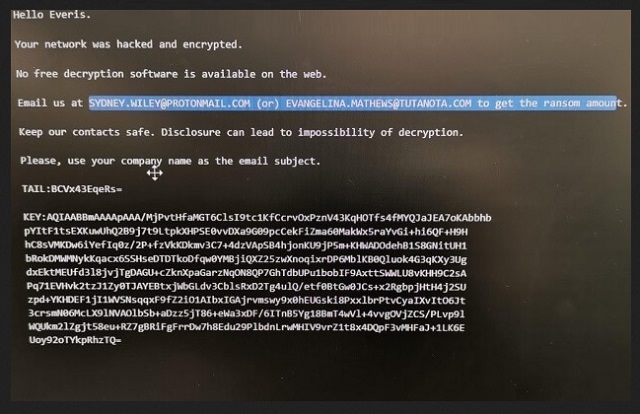
Hello Everis.
Your network was hacked and encrypted.
No free decryption software is available on the web.
Email us at SYDNEY.WILEY@PROTONMAIL.COM (or) EVANGELINA.MATHEWS@TUTANOTA.COM to get the ransom amount.
Keep our contacts safe. Disclosure can lead to impossibility of decryption.
Please, use your company name as the email subject.
TAIL:-
KEY:-
Everis is the name of an atrocious ransomware threat. It uses trickery to slither into your system. Then, spreads its corruption throughout. The tool uses strong encryption algorithms to lock your data. Then, proceeds to extort you for its release. Yes, it targets everything, you keep on your computer. Documents, archives, music, videos. Say, you have a picture called ‘1.jpg.’ After Everis strikes, you discover it renamed to ‘1.jpg.everis.’ The extension can be either of the two: ‘.3v3r1s‘ or ‘.everis.’ Once it’s in place, the file becomes unusable. The only way to turn it accessible again, is to pay up. After you pay the ransom, Everis demands, it promises to send you a unique decryption key. Apply said key, and your files are free. Or, that’s what the cyber kidnappers would have you believe. They leave you a ransom note, with instructions, they expect you to follow. It’s usually a text file, you can find on your Desktop. As well as, in each folder that contains locked files. Sometimes it can even appear in place of your Desktop background photo. These people prey on your fear and naivety, and hope to profit off of them. Don’t let them. Do not pay the ransom. To do so, is a mistake, you’ll regret it. So, don’t.
How did I get infected with?
Everis slips its way into your system via deception. It uses the old but gold methods to invade. Like, lurking behind corrupted links, sites or torrents. Or, pretending to be a false system or program update. Like, Adobe Flash Player or Java. And, it can also turn to freeware and spam emails. One day, you receive an email that appears to come from a legitimate source. Like, a well-known company. PayPal, DHL, Amazon. It reads that you’re required to verify information, or confirm a purchase. And, to do so, you have to click a link, or download an attachment. If you do so, you get stuck with an infection. Don’t give into carelessness. Don’t ease the infection’s infiltration. The Everis ransomware preys on your naivety, haste and distraction. It needs you to rush, and leave your fate to chance. Don’t do it, don’t oblige. Take the opposite approach, and be extra thorough. After all, vigilance allows you to catch cyber threats in the act of attempting invasion. You can spot them, and keep them out. Always choose caution over the lack thereof. Do your due diligence, and remember. Even a little extra attention can save you a ton of troubles.
Why is Everis dangerous?
You must NOT pay the ransom. Ignore the cyber kidnappers’ demands. Compliance guarantees you nothing. So, don’t waste your time, energy and money, trying to comply. Even if you do, everything these people ask of you, it brings you no positives. Here’s the thing. After Everis strikes, you face a choice. To pay, or not to pay. Let’s examine the potential outcomes of that decision, shall we? If you decide to take your chances, and pay, you’ll regret it. These extortionists offer you zero guarantees that payment works. After you transfer the requested ransom amount, what happens next? You wait for the expected decryption key, right? Well, what if they don’t send it? What if they get your money, and send you nothing? Or, what if they do send you a key, but it fails to decrypt your data. Don’t take any chances! Don’t forget that you’re dealing with malicious cyber criminals with questionable agendas. These strangers don’t care whether you’ll regain control over your files. All, they care about is your money. Don’t let them have it. Even, in the case when they do send you the right key, don’t rejoice. Remember that the key removes the encryption, not the encryptor. So, you pay to removes the ‘.everis‘ extension, but not the Everis ransomware. The infection remains, ready to strike again, a mere minute after decryption. Heed experts’ advice, and don’t pay these people. Don’t contact them. Don’t reach out to them at all. Compliance is not the way to go.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Everis Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Everis Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Everis encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Everis encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.