Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove ASN1 Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
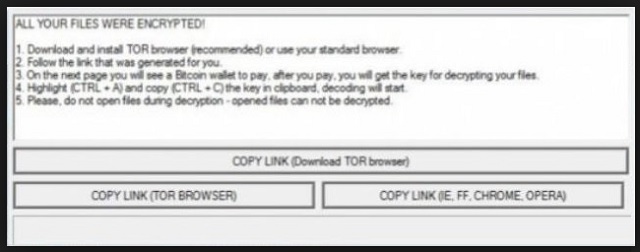
ALL YOUR FILES WERE ENCRYPTED!
1. Download and install TOR browser (recommended) or use your standard browser.
2. Follow the link that was generated for you.
3. On the next page you will see a Bitcoin wallet to pay, after you pay, you will get the key for decrypting your files.
4. Highlight (CTRL + A) and copy (CTRL + C) the key in clipboard, decoding will start.
5. Please, do not open files during decryption – opened files can not be decrypted.
or
Your files were encrypted!
1(0) BTC -> [Bitcoin wallet address] (4:23:59:49)
For getting decryption key, you must pay amount, written above, to the bitcoin address, written above. Amount in brackets indicates already paid amount. For buy bitcoin online, google it now. This page will refresh every 120 seconds. If you already paid, please, wait for page refreshing.
If software was deleted, download it now . Absence of payment during next five days will double the amount.
Chat with support now
ASN1 is a ransomware infection. Those are quite possibly the most dreaded type of cyber threat. And, that’s a title, the tools have earned. They sneak into your system undetected, and take over in one fell swoop. All of a sudden, your files are no longer your files. You come to find them locked. Under the clutches and control of a ransomware tool. One that seek monetary compensation for their release. One that claims that if you don’t pay, you’ll lose everything. And, if you do, everything will work out. You transfer the ransom. You receive the decryption key, you need. You apply it, and free your files. Then, it all goes back to normal. You’re free of the infection and its keep. And, it sounds amazing, doesn’t? Except, it’s nothing but lies. It’s a false narrative, presented by cyber criminals. Extortionists, you can’t and shouldn’t trust. These people WILL double-cross you. They will NOT honor the deal, they’re offering. So, don’t take it. Do yourself a favor, and make the right but difficult choice, placed before you. Forsake your files. Don’t comply. You WILL lose more than your data, if you do. If you follow their demands, and pay the ransom, you lose your privacy. You give these strangers access to your personal and financial details. Is that something, you’re willing to do? It’s tough, but say goodbye to your files and move on. Don’t partake in the fight against a ransomware. You’ll lose.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How did I get infected with?
ASN1 uses the old but gold methods of infiltration to enter your system. It turns to freeware, spam email attachments, and corrupted links. It can even pretend to be a bogus update. Like, Java or Adobe Flash Player. And, here’s the thing. If you’re not careful enough to catch it in its invasive attempts, that’s it. It slips right through the cracks, provided by your carelessness. If you wish, to at least improve your chances of spotting the tool, be cautious! Always take the time to do your due diligence. Read the terms and conditions. Don’t rush, and don’t give into naivety. Distraction often leads straight to infections. So, pick caution instead. Carelessness is a one-way street to cyber threats. But vigilance helps you avoid them. If anything, a little extra attention can’t hurt. You can spare a few additional moments of research if they can save you a ton of headaches and issues in the future. Can’t you?
Why is ASN1 dangerous?
ASN1 doesn’t make it as easy for you to know it’s there as other such tools. Once it slithers its way in, it proceeds with encryption. It locks everything with the help of AES and RSA ciphers. But, here’s the major difference, we hinted at. While most ransomware programs add a special extension at the end of your files, ASN1 does not. Instead, it leaves them as they are. So, they seem untouched. That is, until you try to open them. That’s when you notice you can’t. You can’t reach your documents, videos, pictures, music, anything. All is under ASN1’s keep. The infection even deletes Volume Shadow Copies. That way, it can make sure that you have no alternative to compliance. If you wish to get your data back, the ransomware offers your only solution. But, as was already explained, ASN1’s solution is an unacceptable one. If you pay the ransom, you’ll give access to your private information to cyber criminals. Extortionists can use your personal and financial details as they see fit. Can you think of even one scenario, where that ends well for you? And, even if you have a wild imagination, and you can, you still shouldn’t. First of all, the amount it requests moves from 0.25 to 1 Bitcoin. In case, you’re unfamiliar, 1 Bitcoin currently surpasses $600. The ransom is no pocket change. And, secondly, payment only means you’ll receive a decryption key. That also raises a few questions. Will there even be a key, at all? What if it doesn’t send one? What if it does, but it doesn’t work? And, even if it’s the right key, what then? Here’s what you have to realize. Paying the ransomware only remove the encryption. The ransomware remains. And, what if it strikes back the next day? What then? You have no guarantees it won’t. Whichever way you look at it, you lose. So, don’t play the game, the infection sets up. Like, all ransomware, ASN1 is a formidable foe. Discard your data. Protect your privacy.
ASN1 Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover ASN1 Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with ASN1 encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate ASN1 encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



