Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Can’t Remove On this day i hacked your os and got full access to your account Malware?
There have been quite a few email scams, circulating the web. One day, you receive an email that’s full of lies. One that’s designed to frighten you into acting against your better judgment. “On this day i hacked your os and got full access to your account” is one such email. You find it in your inbox, because of an infection. A cyber threat, that belongs to the scamware family, slithered into your system. It’s the culprit behind the scary-seeming email. It’s yet another Bitcoin Email Scam, and it’s nothing that stands out. The infection follows a similar pattern. It invades your PC via slyness and finesse. Then, once inside, sends the email. It’s classic fear mongering. The infection uses scare tactics to get you to pay strangers a ransom of sorts. The email claims that cyber criminals have stolen private information from you. And, if you wish for it to stay private, you have to pay up. Understand that it’s all a lie. Consider it a phishing scam. If you bite, they profit off of your naivety. Don’t bite! If the email pops up into your inbox, try to stay level-headed. Acknowledge the presence of a scamware on your PC. Find its exact hiding place, and delete it on discovery. It’s the best course of action, you can take.

How did I get infected with?
Scamware slithers into your system, because of trickery and carelessness. The infection turns to slyness and finesse in its approach towards infiltration. And, its methods prove successful, if you provide the carelessness. Consider it a key ingredient for the tool’s invasion. Let’s explain. Scamware tools are quite deceitful, when it comes to sneaking into your system. They resort to a variety of tricks. But neither one can prove successful without you. There aren’t enough ways to stress that! The usual antics include the use of freeware, corrupted links, sites, and torrents. The tool can also pretend to be a system or program update. Like, Java or Adobe Flash Player. And, of course, it can turn to spam emails. Say, you receive an email that seems to come from a well-known company, like Amazon. It urges you into downloading an attachment, or clicking a link. Do that, and you end up with an infection. Don’t give into naivety, and leave your fate to chance. Always take the time to do your due diligence. Read terms and conditions, know what you say YES to, look for the fine print. Double-check everything! Even a little extra attention today can save you a ton of troubles tomorrow. Choose caution over carelessness. One keeps threats out, while the other opens your PC up to them.
Why are these ads dangerous?
The email reads that your system got hacked a while back. And, during that time, the hackers have spied on you. They observed your browsing habits, and took screenshots of your activities. They threaten that your web cam proved to be a window to your life. And, through the camera, they managed to catch you in your most private actions. The email claims that the hackers will send these private screenshots to your contact list. Then, colleagues, relatives and friends get to see them. Supposedly, get to see you doing things, you’d rather keep private. They then request you pay them money, if you wish for them not to go through with their plan. They expect the payment in Bitcoins, and it ranges between 500 and 1000 US Dollars. But even if it were a single cent, you still shouldn’t pay. These people are lying to you! They strive to get you into a frenzy, and exploit you, in your panicked state. Don’t let them fulfill their scam! Accept that these people are pushing lies your way, and don’t send them money. That doesn’t mean that you’re in the clear, though. There is an infection on your computer. It’s responsible for the deceitful email. The scamware lurks, somewhere in the corners of your PC. It tries to take advantage of your gullibility and fear. Don’t allow that! Do your best to find its exact hiding place, and when you do, get rid of it. The sooner the infection leaves your system, the better.
How Can I Remove On this day i hacked your os and got full access to your account Malware?
If you perform exactly the steps below you should be able to remove the infection. Please, follow the procedures in the exact order. Please, consider to print this guide or have another computer at your disposal. You will NOT need any USB sticks or CDs.
STEP 1: Uninstall suspicious software from your Add\Remove Programs
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 2: Delete unknown add-ons from Chrome, Firefox or IE
STEP 1 : Uninstall unknown programs from Your Computer
Simultaneously press the Windows Logo Button and then “R” to open the Run Command
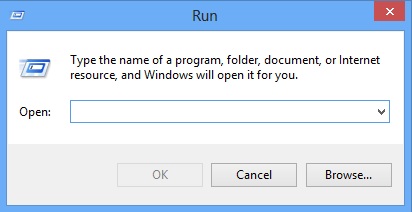
Type “Appwiz.cpl”
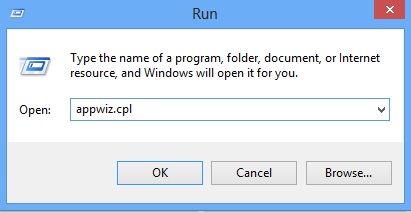
Locate the any unknown program and click on uninstall/change. To facilitate the search you can sort the programs by date. review the most recent installed programs first. In general you should remove all unknown programs.
STEP 2 : Remove add-ons and extensions from Chrome, Firefox or IE
Remove from Google Chrome
- In the Main Menu, select Tools—> Extensions
- Remove any unknown extension by clicking on the little recycle bin
- If you are not able to delete the extension then navigate to C:\Users\”computer name“\AppData\Local\Google\Chrome\User Data\Default\Extensions\and review the folders one by one.
- Reset Google Chrome by Deleting the current user to make sure nothing is left behind
- If you are using the latest chrome version you need to do the following
- go to settings – Add person
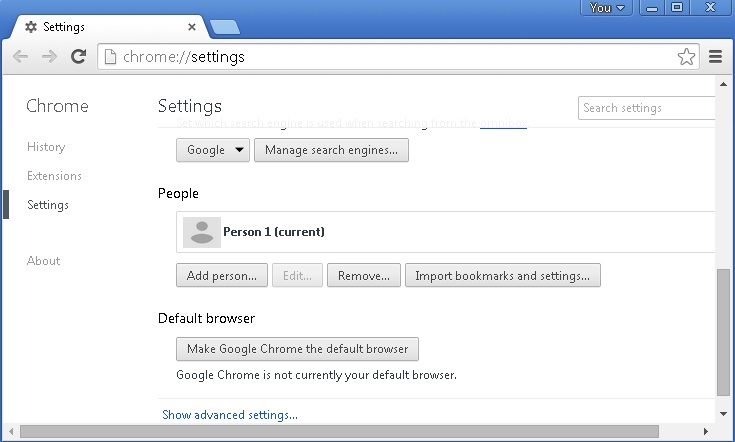
- choose a preferred name.
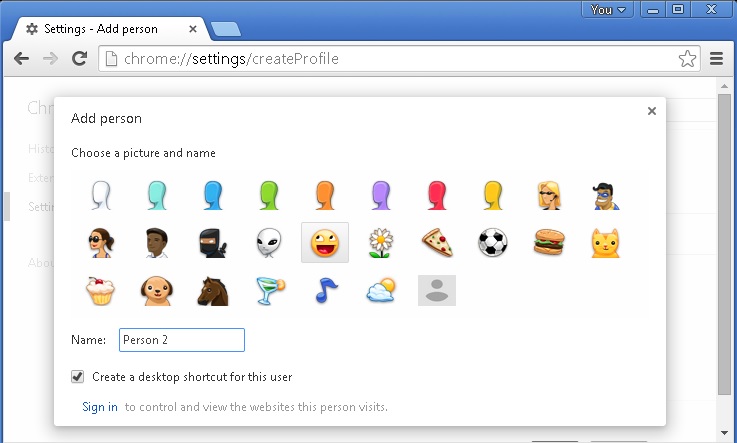
- then go back and remove person 1
- Chrome should be malware free now
Remove from Mozilla Firefox
- Open Firefox
- Press simultaneously Ctrl+Shift+A
- Disable and remove any unknown add on
- Open the Firefox’s Help Menu
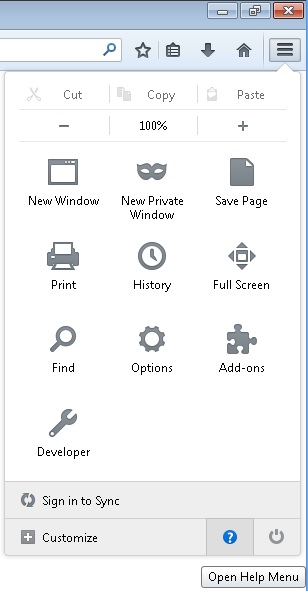
- Then Troubleshoot information
- Click on Reset Firefox
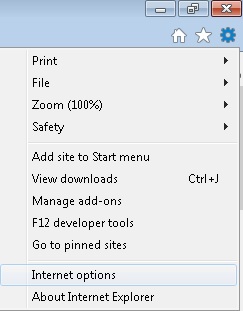
Remove from Internet Explorer
- Open IE
- On the Upper Right Corner Click on the Gear Icon
- Go to Toolbars and Extensions
- Disable any suspicious extension.
- If the disable button is gray, you need to go to your Windows Registry and delete the corresponding CLSID
- On the Upper Right Corner of Internet Explorer Click on the Gear Icon.
- Click on Internet options
- Select the Advanced tab and click on Reset.
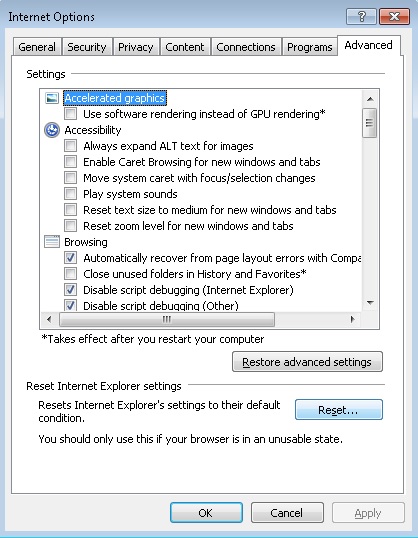
- Check the “Delete Personal Settings Tab” and then Reset
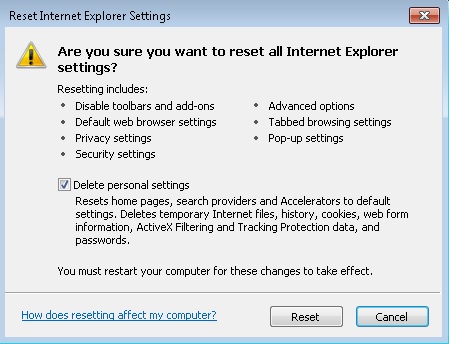
- Close IE
Permanently Remove On this day i hacked your os and got full access to your account Malware Leftovers
To make sure manual removal is successful, we recommend to use a free scanner of any professional antimalware program to identify any registry leftovers or temporary files.