Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove NanoLocker Ransomware?
NanoLocker is a ransomware tool. And, ransomware is quite possibly the worst type of cyber infection you can catch. It targets anything and everything you have stored on your computer – pictures, documents, videos, music, etc. The tool encrypts every single file and, in a sense, takes it hostage. It then demands you pay ransom if you ever wish to regain control of them. Your files are still found on your PC. The infection doesn’t relocate them or anything. It merely cloaks them. It’s just that you cannot access them. You can’t open a single one of them. Your only opportunity, to get your data back, is if you get a hold of the decryption key. Naturally, to get it, you have to pay up. But, let’s be reasonable for a moment. Think about how the situation can unfold. There are several ways this standoff between you and the ransomware can go down. And, you’re always on the losing side, even if you win. Confused? Let’s elaborate. NanoLocker slithers into your PC, encrypts everything, and places its demands – pay up and we’ll give you a decryption key. So, let’s discuss one of the scenarios, which is seemingly the best one. You pay the ransom, and the application hands you the decryption key. You then reclaim your files, and all is well in the world. So far, so good, right? Well, wrong. Consider this. What’s to stop the ransomware infection from kicking back in the very next day? The answer is ‘Nothing.’ NanoLocker can strike again and encrypt your data once more, even though you’ve already gone through the exchange of money for a decryption key. That’s how the tool is programmed. It’s designed to exploit you for as long as you let it. So, don’t let it! Don’t allow strangers with wicked agendas to take advantage of you. Don’t rely on the honor of unknown third parties, and instead of complying with the ransomware demands, accept you can’t win, and cut your losses. Yes, it’s harsh, but it’s the best course of action you can take.
How did I get infected with?
How do you imagine you got stuck with an infection as dreadful as NanoLocker? After all, it couldn’t have just popped up out of the blue one day. As much as you don’t want to hear it, it’s because of you. You’re behind the malware getting into your system. Don’t beat yourself up too hard. Tools, like this one, are full-on masters of deceit. They not only slither into your PC, but they cover their tracks quite well. They sneak in undetected by preying on your carelessness. To achieve that level of deception, they turn to every known trick in the book. Through slyness and subtlety, they manage to slip through the cracks of your distraction and invade your PC. So, don’t be careless. Don’t rush and don’t throw caution to the wind. Instead, be more vigilant and do your due diligence. That way, you just might spot the infection trying to slither in, and stop it before it makes a mess. Some of the most commonly used means of infiltration such applications tend to turn to include hiding behind freeware, corrupted sites of links, or spam email attachments. And, they can also pretend to be bogus updates, like Adobe Flash Player or Java. Above all, you need to remember to be more careful as even a little extra attention can go a long way.
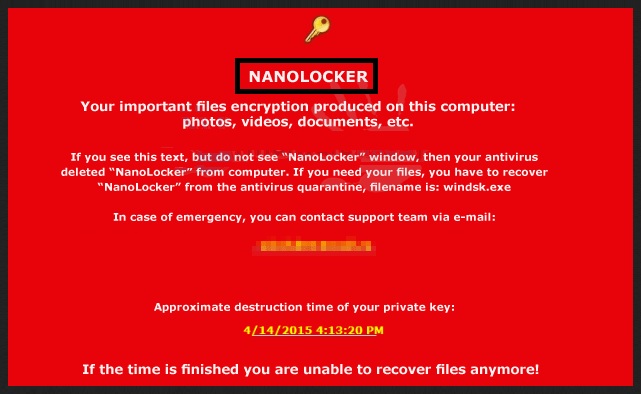
Why is NanoLocker dangerous?
NanoLocker is a ransomware, which employs the same, old strategy, characteristic for all such tools. It gets into your computer, encrypts all of the data you have on it, and requests you pay ransom if you wish to decrypt them. As long as your files are encrypted, they’re useless to you. You see them, but they’re beyond your reach. After the encryption process is complete, the application leaves a note for you to see so that you know what’s expected of you. The note may be an HTML, JPEG or TXT file, and it might contain directions that you write an email to a disposal email box from NeoEmailBox.com and Notsharingmy.info. Ultimately, there are many ifs, and buts, and mights, but what it comes down to is that this is a fight you can’t win. So, as unpleasant as it may seem, say goodbye to your data and do some damage control. Yes, the infection may have taken over your files, but, at least, don’t let it get a hold of your private details. Don’t grant it access to your personal and financial information, which is what you’ll do if you comply with its demands and pay its ransom. Cut your losses! If you wish to avoid finding yourself in the same situation, create backups of your files, and be more cautious when installing freeware or visiting questionable websites.
NanoLocker Removal Instructions
STEP 1: Start Your Computer into Safe Mode with Networking
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Restart the computer
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.

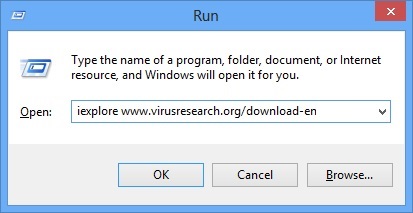
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type iexplore www.virusresearch.org/download-en
- Internet Explorer will open and a professional scanner will prompt to be downloaded
- Run the installer
- Follow the instruction and use the professional malware removal tool to detect the files of the virus.
- After performing a full scan you will be asked to register the software. You can do that or perform a manual removal.
Remove NanoLocker Manually
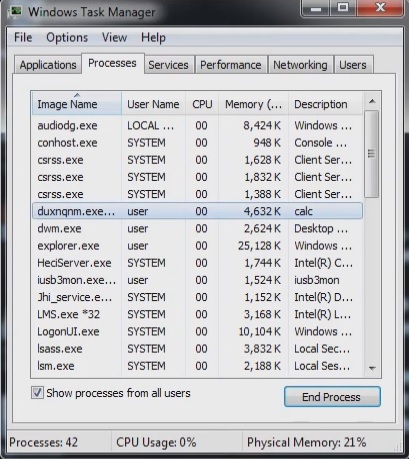
Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
Locate the process of teslacrypt. Have in mind that this is usually a random generated file.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Before you kill the process, type the name on a text document for later reference.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you run the professional scanner to identify the files.
It is always a good idea to use a reputable anti-malware program after manual removal, to prevent this from happening again.