Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
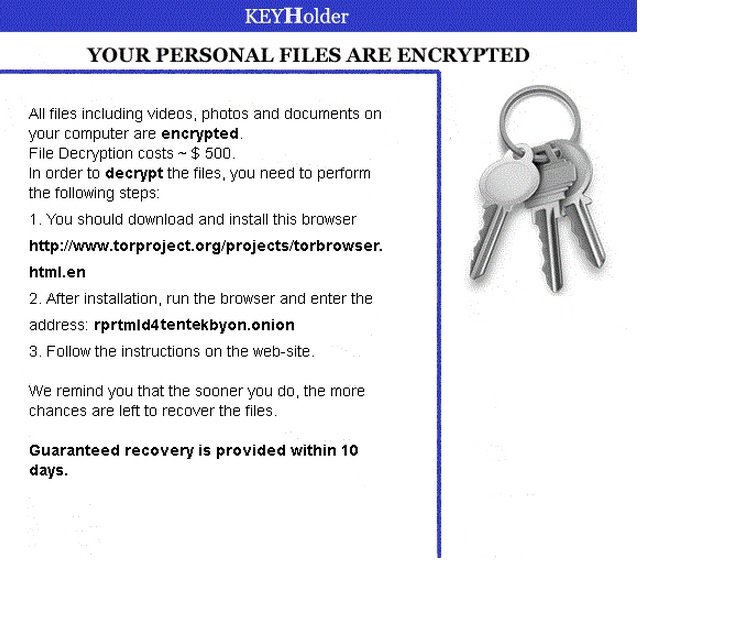
If you are seeing “Your personal files are encrypted” message – you are infected with KeyHolder Ransomware!
KeyHolder is classified as ransomware. Once it has infected your system, it encrypts all of your files and holds them for ransom until you pay up. There are three ways the situation can go down after it first makes an appearance and threatens your files. One, you refuse to pay and your files stay encrypted. Two, you pay up and receive the necessary information with which to decrypt your files. And three, you pay up and your files still stay encrypted. That’s right, there is a strong possibility that even if you do whatever KeyHolder demands from you, you might still be left with your files encrypted. In any case, KeyHolder is a serious threat and should be removed from your system as soon as possible
How did I get infected with KeyHolder?
KeyHolder resorts to the usual antics in order to infiltrate your PC. Some of the most common entry points it finds is through compromised web links, spam email messages, false system upgrades, and freeware downloads from suspicious sources. These are all old but gold ways of infiltration that help KeyHolder trick users into installing it on their PC.
Why is KeyHolder Dangerous?
Once in, KeyHolder Ransomware encrypts all of the files on your computer starting with photos, all the way up to music, videos and documents. As soon as it has finished with the encryption, it shows you a message informing you of the conditions of the “release” of your files. It basically tells you what you need to do if you want your files decrypted – how much you need to pay and how long you have to do so. The message is the only thing on your desktop, but don’t be alarmed, if you restart the computer, your icons will reappear and the message will be gone. Despite your best hopes though, your files will still remain encrypted. If you decide to take your chances and pay the ransom, KeyHolder requires you to download the Tor Internet browser and once you’ve installed it, you’ll find further instructions there. Best case scenario, you’ll receive the decryption key and restore your files. Worst case scenario, you’ll lose all your files. Either way, you should remove KeyHolder as soon as you possibly can.
How to Remove KeyHolder?
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
from Windows 7 (Win 8 instructions are further below)
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your infected computer
- Restart the computer
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.

- Once the operating system loads press simultaneously the Windows Logo Button and the R key.

- A dialog box should open. Type iexplore www.virusresearch.org/download-en
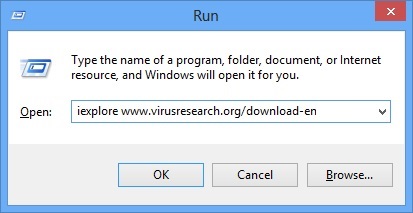
- your Internet Explorer will open and a professional scanner will start downloading
- Follow the instruction and use the professional malware removal tool to detect the files of the virus.
- After performing a full scan you will be asked to register the software. You can do that or perform a manual removal as shown in step 2
from Windows 8
Start Your Computer into Safe Mode with Networking
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Move the mouse to the upper right corner until the windows 8 charm menu appears
- Click on the magnifying glass
- select Settings
- in the search box type Advanced
- On the left the following should appear
- Click on Advanced Startup Options
- Scroll down a little bit and click on Restart Now
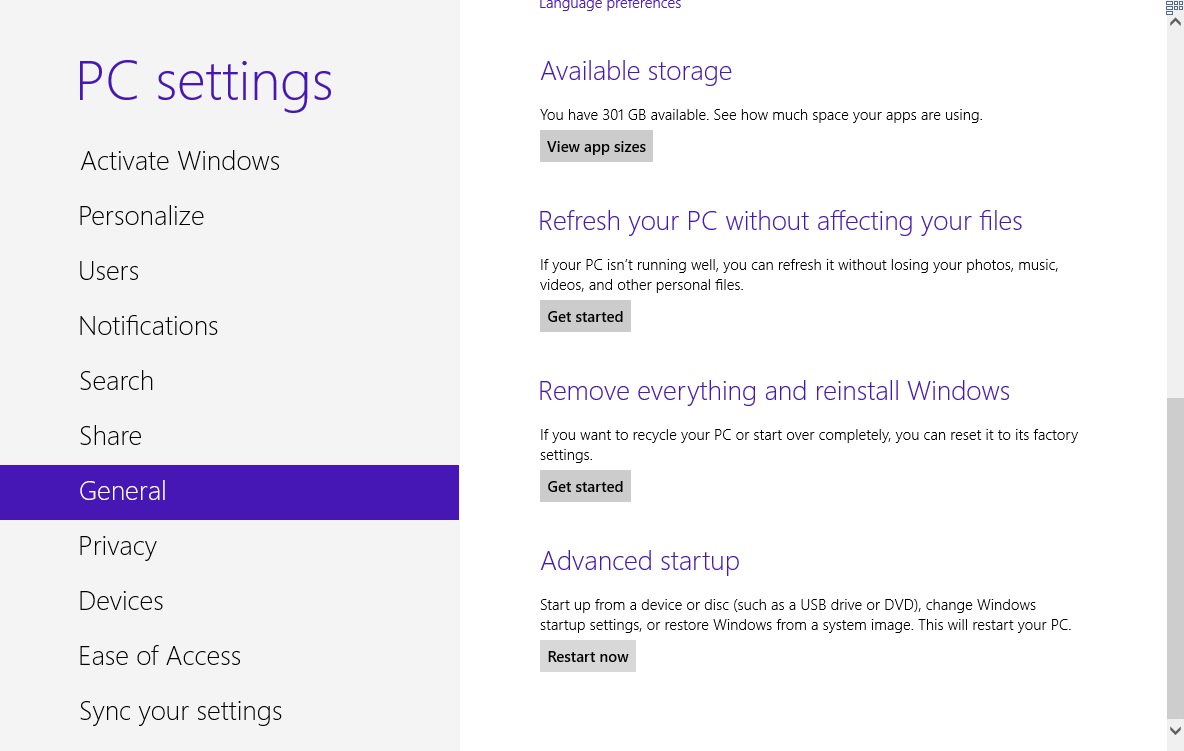
- Click on Troubleshoot
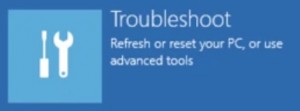
- Then Advanced options

- Then Startup settings

- Then Restart
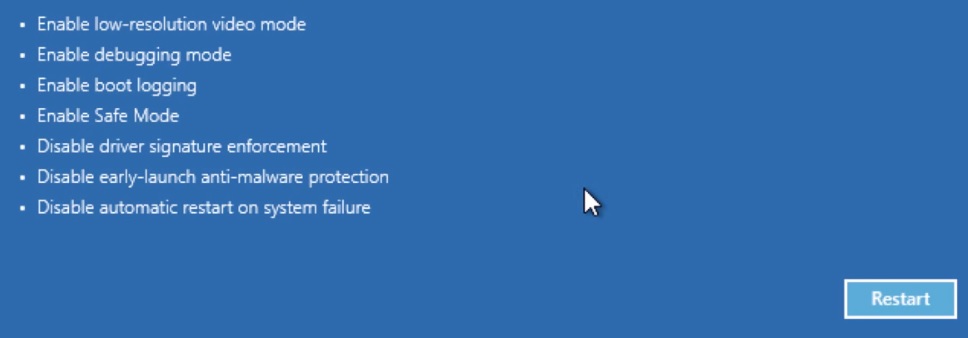
- When you see this screen press F5 – Enable Safe Mode with Networking

- Once the operating system loads press simultaneously the Windows Logo Button and the R key.

- A dialog box should open. Type iexplore www.virusresearch.org/download-en
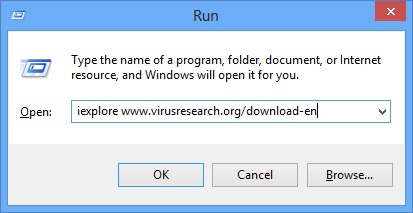
- Internet Explorer will open and a professional scanner will start downloading
- Follow the instruction and use the professional malware removal tool to detect the files of the virus.
- After performing a full scan you will be asked to register the software. You can do that or perform a manual removal.
- To perform Manual removal you need to follow the steps below.
STEP 2: Locate the virus start-up point
while in safe mode, simultaneously press the Windows Logo Button and then “R” to open the Run Command
Type “services.msc” locate the service named SecurityCenterServer and disable it.
Open your Windows Registry Editor
navigate and delete the following registry keys:
HKLM\SYSTEM\CURRENTCONTROLSET\SERVICES\SecurityCenterServer
HKLM\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN|Dmsqksqrwqbsr, C:\Users\”USERNAME”\AppData\Roaming\Kgaord\posdqm.exe
SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN|Dmsqksqrwqbsr, C:\Users\”USERNAME”\AppData\Roaming\Kgaord\posdqm.exe
Please, note, that the file names are random and yours might be different.


